Toward Vulnerability Assessment for 5G Mobile Communication Networks
Shibo Luo, Jun Wu, Member,IEEE, Jianhua Li,
and Longhua Guo
School of Electronic Information and Electrical
Engineering
Shanghai Jiao Tong University
Shanghai, China
luoshibo.pla@sjtu.edu.cn, junwuhn@sjtu.edu.cn
Bei Pei
Key Lab of Information Network Security
Ministry of Public Security
Shanghai, China
Abstract—For 5G, Software-Defined Networking have
emerged as a future mobile network architecture. It is so called
Software-Defined Networking based Mobile Networks (SDN-
MN). Because of the dynamic and virtual features of SDN-MN,
most traditional network vulnerability assessment
methodologies cannot be applied in SDN-MN directly. As a
result, a new methodology of vulnerability assessment for
SDN-MN is needed. In this paper, an effective vulnerability
assessment mechanism is proposed for SDN-MN using attack
graph algorithm and analytic hierarchy process (AHP). An
optimized attack graph is given to alleviate scalability problem.
In order to quantify security level, we define node minimal
effort to quantify attack cost and then derive system security
level. Aiming to calculate node minimal effort of attack graph
in SDN-MN dynamic environment, AHP and Technique for
Order Preference by Similarity to an Ideal Solution (TOPSIS)
are integrated into the methodology with regard to dynamic
vulnerability factors in SDN-MN. Finally, we offer a case study
to validate the methodology. The case study and evaluation
show the advantages of the proposed vulnerability assessment
mechanism.
Keywords-5G, Vulnerability assessment, Software-Defined
Networking based Mobile Networks, attack graph, node minimal
effort, analytic hierarchy process
I. INTRODUCTION
In recent years, Software-Defined Networking (SDN) has
attracted great attentions as emerging future network
architecture in the fields such as 5G, cloud services and so on.
Different from traditional network architecture, network
control plane of SDN is decoupled from forwarding and is
directly programmable. This feature is a great help to
simplify policy enforcement and network (re)configuration
and evolution [1][2].
On the other hand, today’s mobile customers desire to
remain connected anywhere, at any time, and using any
device. This triggered the investigation of 5G for the next
generation of terrestrial mobile telecommunications. In this
context, SDN based Mobile Networks (SDN-MN) have
emerged as a future architecture for 5G [4][8].
Accompanied with benefits of SDN-MN, the properties of
centralized control and programmability also produce some
new properties into network that introduce new security
challenges. That is to say SDN-MN is not as same static as
traditional networks and it is greatly dynamic. These
properties lead to new security vulnerabilities in SDN-MN.
To defend SDN-MN, it is the most primary to measure the
security of SDN-MN addressing the dynamic property.
A number of security researches for SDN have recently
been performed [3]. These work have found that the
relationship between elements in the SDN framework
introduce new vulnerabilities. Some of them were not
present before SDN. A comprehensive security attack
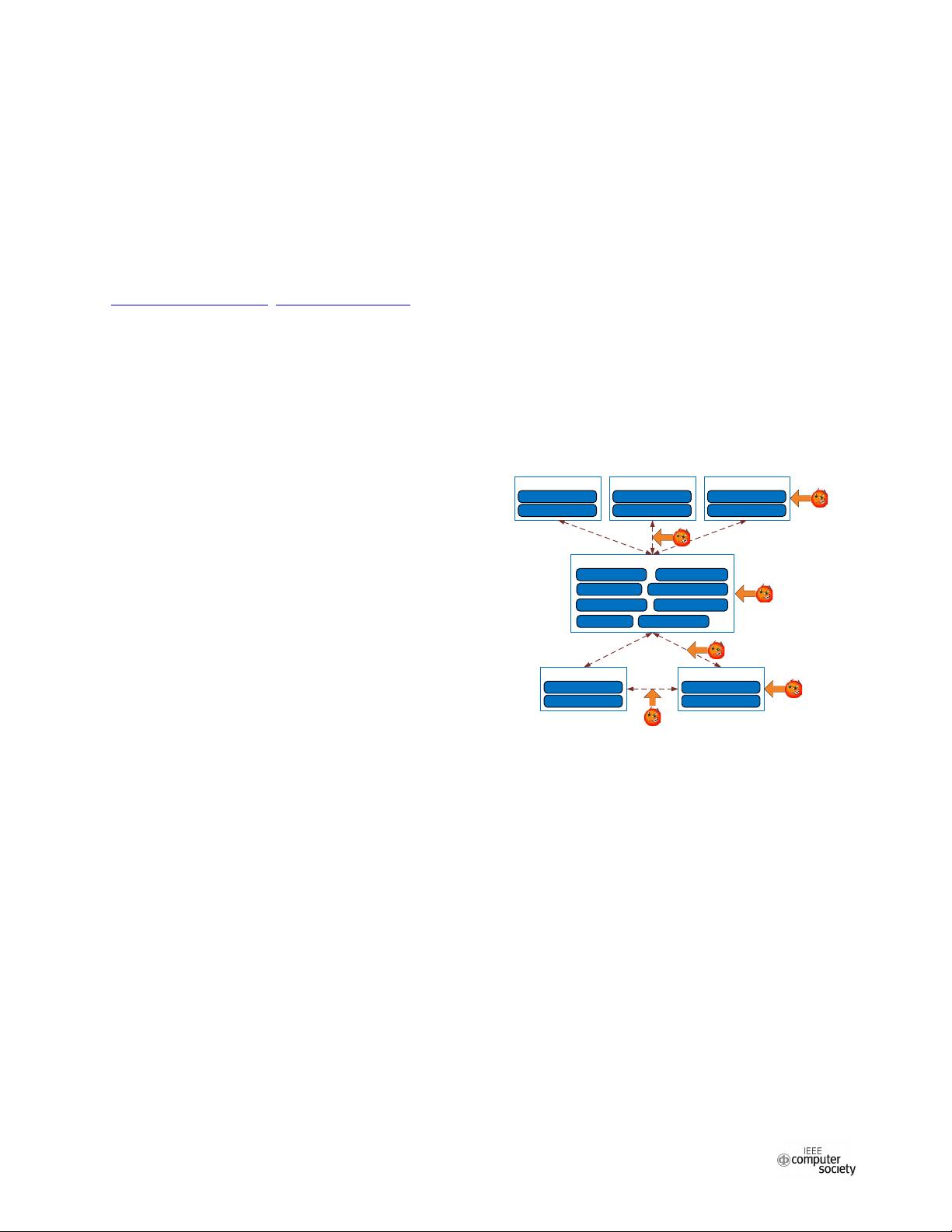
vectors map of SDN is illustrated in Fig. 1.
There are also already lots of researches focusing on
traditional network vulnerability assessment. Among the
researches, how to compose the measure of individual
components is one of the critical issues. Attack graph method
is to address this problem [5].
Among traditional researches, some of them only focus
on traditional networks that do not take the special properties
of SDN into consideration. And some of them only focus on
the isolated security issues in SDN that do not provide a
system level security methodology. All of them can’t be
applied in SDN-MN directly for vulnerability assessment.
Based on aforementioned analysis, it is very necessary to
provide an effective vulnerability assessment mechanism for
SDN-MN considering its vulnerability and virtual features.
This paper propose a vulnerability assessment scheme for
SDN-MN using attack graph and analytic hierarchy process
(AHP).The rest of the paper is organized as follows: The
basic idea of our vulnerability assessment methodology is
described in Section II. Section III presents the formalism for
an attack graph model. The quantification method of node
minimal effort of attack graph is discussed in Section IV. In
WorkStation
SDN App Logic
Northbound Interface
Service Compiler
Kernel
Network Function
Kernel
Network Function
Network Compiler
NMS Plugins
Network Configuration
WorkStation
SDN App Logic
WorkStation
SDN App Logic
Topology Discovering
Topology Monitoring
Southbound Interface
...
Attacks on traffic
flows
Attacks on control
plane communications
Attacks on
network
elements
Attacks on
controllers
Attacks on application
plane communications
Attacks on Apps
Fig. 1. Security attack vectors of SDN
2015 IEEE International Conference on Smart City/SocialCom/SustainCom together with DataCom 2015 and SC2 2015
978-1-5090-1893-2/15 $31.00 © 2015 IEEE
DOI 10.1109/SmartCity.2015.50
72









