802.1X协议详解:EAPOL报文封装与EAP数据包格式
需积分: 9 160 浏览量
更新于2024-09-08
收藏 587KB DOC 举报
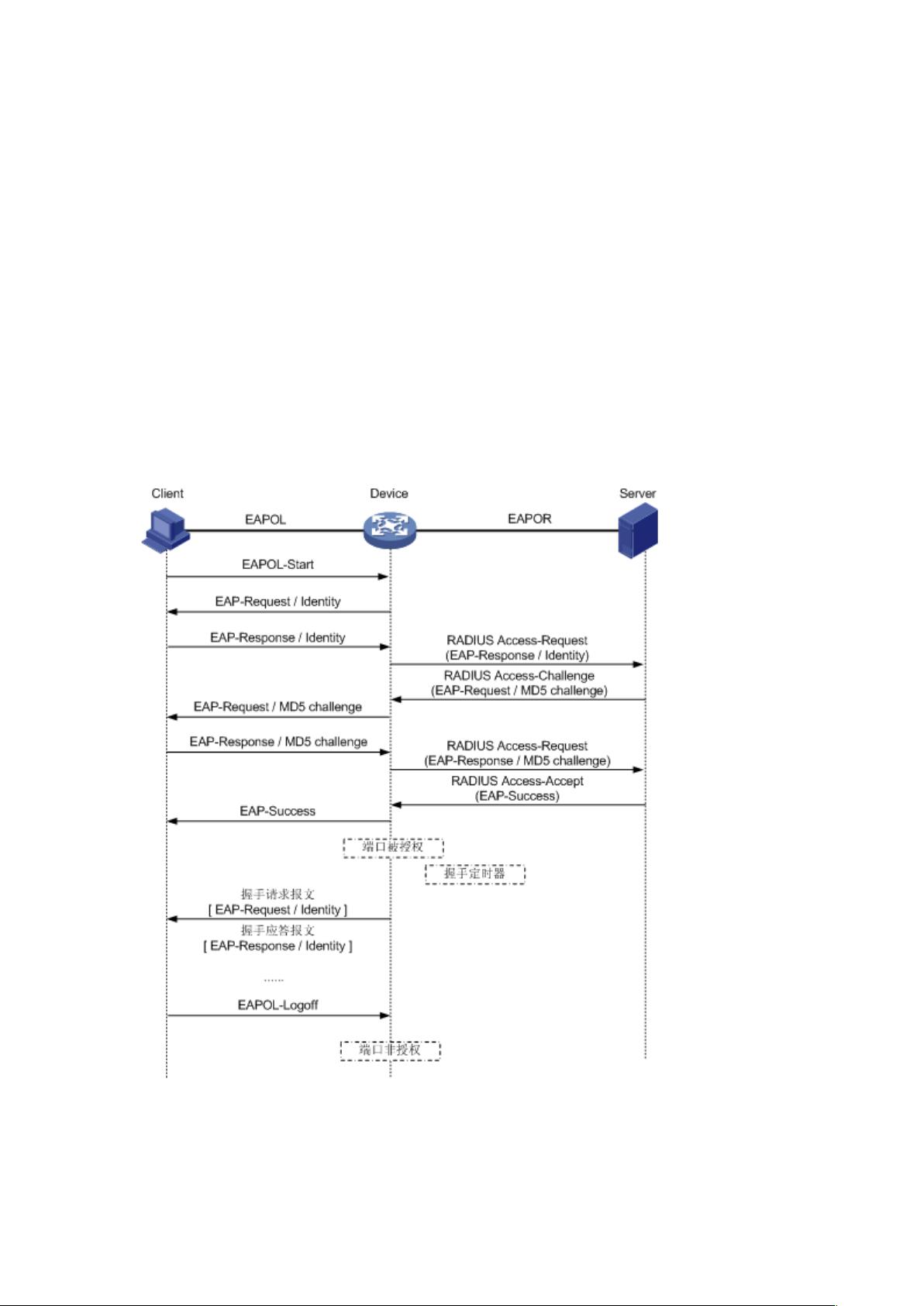
802.1X是一种基于IEEE 802.1标准的网络访问控制(NAC)技术,主要用于实现安全的有线局域网(WLAN)接入控制。它通过在客户端和接入点(Access Point, AP)之间传输EAP(Extensible Authentication Protocol)协议报文,确保只有经过认证的用户才能访问网络资源。本文将深入探讨802.1X的基本原理,特别是EAPOL(Ethernet Authentication Protocol over LANs)消息的封装。
EAPOL是802.1X的核心组件,它定义了一种报文封装格式,允许在LAN环境中透明地传递EAP协议数据。EAPOL数据包分为两种主要类型:
1. EAPOL-Packet:这种帧用于封装和携带认证信息,通常在客户端和设备端之间传输。它的结构包括EthernetType (0x888E)表示EAPOL协议,ProtocolVersion标识支持的协议版本,Type字段表示EAPOL数据帧类型,如EAP-Packet (0x00)用于认证信息交换,EAPOL-Start (0x01)用于认证过程的初始化,EAPOL-Logoff (0x02)则表示退出请求。Length字段表示Packet Body的长度,Packet Body部分根据Type的不同包含具体的EAP数据。
2. EAP数据包:当Type为EAP-Packet时,Packet Body会包装实际的EAP数据包。EAP数据包有四种Code类型:Request、Response、Success和Failure。Success和Failure类型的包不包含Data域,而Request和Response类型的包(如Identity请求和响应,以及MD5-Challenge质询和应答)具有Identifier来匹配请求和响应,Length表示包的整体大小,包括元数据和Data域内容。
EAPOL消息的封装确保了数据能在复杂的网络环境中安全传输,并且只有经过双方认可的EAP协议交互,用户才能完成认证过程。这使得802.1X成为现代WLAN安全策略中的关键一环,帮助网络管理员实现对无线用户的准入控制,保护网络免受未经授权的访问。理解并掌握802.1X和EAPOL的消息格式对于实施和维护一个安全的无线环境至关重要。
525 浏览量
1000 浏览量
420 浏览量
101 浏览量
168 浏览量
187 浏览量
234 浏览量
2014-09-15 上传
2009-06-25 上传
weixin_41468751
- 粉丝: 0
最新资源
- 网狐工具:核心DLL和程序文件解析
- PortfolioCVphp - 展示JavaScript技能的个人作品集
- 手机归属地查询网站完整项目:HTML+PHP源码及数据集
- 昆仑通态MCGS通用版S7400父设备驱动包下载
- 手机QQ登录工具的压缩包内容解析
- Git基础学习仓库:掌握版本控制要点
- 3322动态域名更新器使用教程与下载
- iOS源码开发:温度转换应用简易教程
- 定制化用户登录页面模板设计指南
- SMAC电机在包装生产线应用的技术案例分析
- Silverlight 5实现COM组件调用无需OOB技术
- C#实现多功能画图板:画直线、矩形、圆等
- 深入探讨C#语言在WPF项目开发中的应用
- 新版2012109通用权限系统源码发布:多角色用户支持
- 计算机科学与工程系网站开发技术源码合集
- Java实现简易导出Excel工具的开发教程