2 Chapter 1: Introduction
browser, your IM agent, or a file-sharing program. The application programs running on hosts
are the real “users” of the network. Routers are machines whose job is to relay, or forward,
information from one communication channel to another. They may run programs but typically
do not run application programs. For our purposes, a communication channel is a means of
conveying sequences of bytes from one host to another; it may be a wired (e.g., Ethernet), a
wireless (e.g., WiFi), or other connection.
Routers are important simply because it is not practical to connect every host directly
to every other host. Instead, a few hosts connect to a router, which connects to other routers,
and so on to form the network. This arrangement lets each machine get by with a relatively
small number of communication channels; most hosts need only one. Programs that exchange
information over the network, however, do not interact directly with routers and generally
remain blissfully unaware of their existence.
By information we mean sequences of bytes that are constructed and interpreted by pro-
grams. In the context of computer networks, these byte sequences are generally called packets.
A packet contains control information that the network uses to do its job and sometimes also
includes user data. An example is information identifying the packet’s destination. Routers
use such control information to figure out how to forward each packet.
A protocol is an agreement about the packets exchanged by communicating programs
and what they mean. A protocol tells how packets are structured—for example, where the
destination information is located in the packet and how big it is—as well as how the infor-
mation is to be interpreted. A protocol is usually designed to solve a specific problem using
given capabilities. For example, the HyperText Transfer Protocol (HTTP) solves the problem of
transferring hypertext objects between servers, where they are stored or generated, and Web
browsers that make them visible and useful to users. Instant messaging protocols solve the
problem of enabling two or more users to exchange brief text messages.
Implementing a useful network requires solving a large number of different problems.
To keep things manageable and modular, different protocols are designed to solve different
sets of problems. TCP/IP is one such collection of solutions, sometimes called a protocol suite.
It happens to be the suite of protocols used in the Internet, but it can be used in stand-alone
private networks as well. Henceforth when we talk about the network, we mean any network
that uses the TCP/IP protocol suite. The main protocols in the TCP/IP suite are the Inter-
net Protocol (IP) [14], the Transmission Control Protocol (TCP) [15], and the User Datagram
Protocol (UDP) [13].
It turns out to be useful to organize protocols into layers; TCP/IP and virtually all other
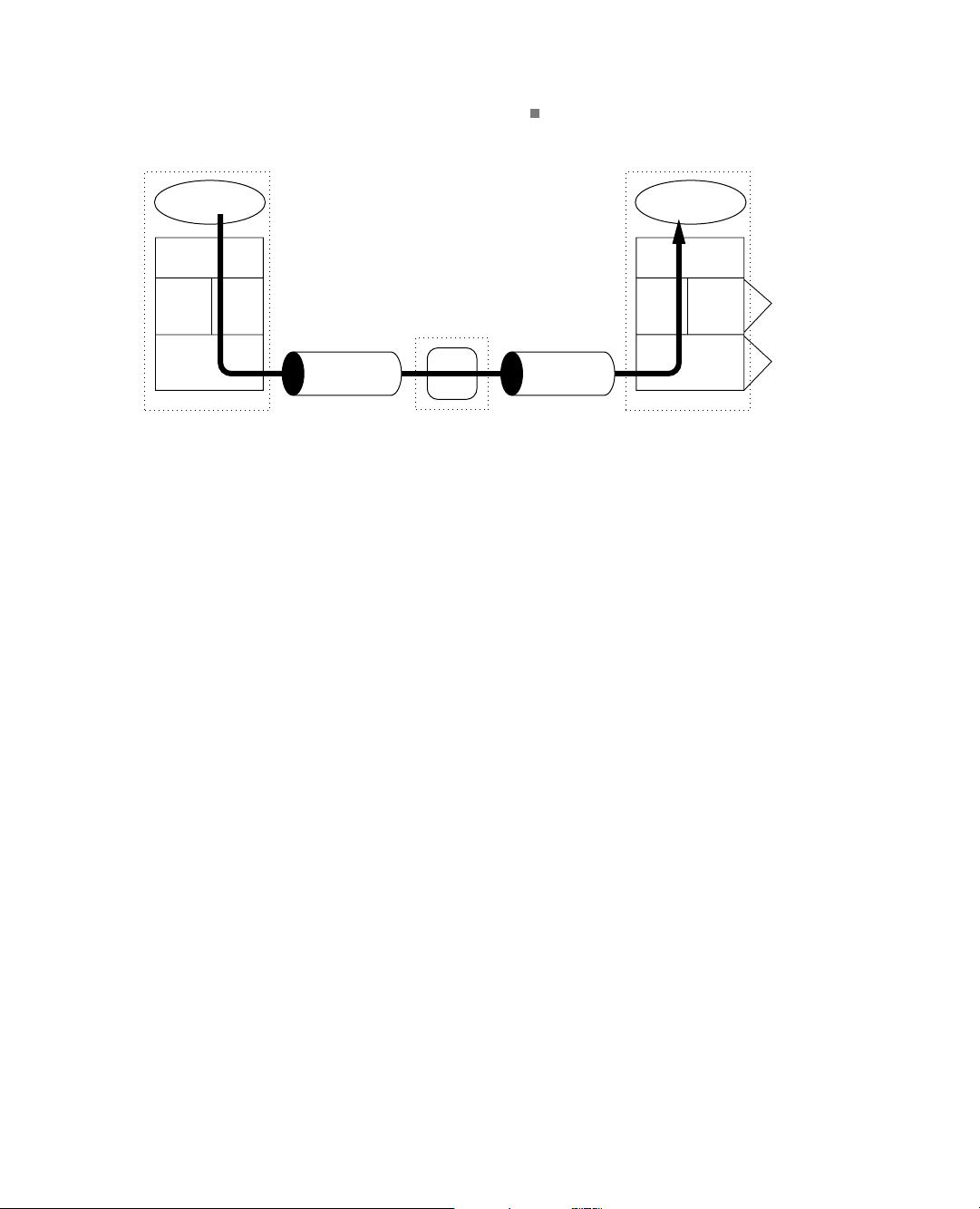
protocol suites are organized this way. Figure 1.1 shows the relationships among the protocols,
applications, and the sockets API (Application Programming Interface) in the hosts and routers,
as well as the flow of data from one application (using TCP) to another. The boxes labeled TCP,
UDP, and IP represent implementations of those protocols. Such implementations typically
reside in the operating system of a host. Applications access the services provided by UDP and
TCP through the sockets API. The arrow depicts the flow of data from the application, through
the TCP and IP implementations, through the network, and back up through the IP and TCP
implementations at the other end.