from a specific range of very large and rarely used integer
values (we call it Dirty-zone). It is analogous to poisoning
the value. IntTracker only reports when a poisoned value
reaches a memory sink. Note that 1) all integer operations
along the propagation path of a poisoned value would not
change its poisonous feature (as proved in Section 2.3.3);
2) if there is any sanitization routine along the propagation
path of a poisoned value, the propagation can be automat-
ically stopped due to the fact that the poisoned value falls
out of the legitimate range allowed by the check. In other
words, IntTracker can reduce the false positives introduced
by sanitization routines.
Our contributions are highlighted as follows.
1. We define sanitization routines into two categories:
Santz-postcond which uses fixed patterns to catch over-
flows and can be identified through static analysis, and
Santz-spec which leverages specific program character-
istics to sanitize overflown values and are left for our
dynamic technique to handle.
2. We propose a novel efficient dynamic tracking tech-
nique. It uses very large and rarely used dirty val-
ues as the indicator of overflows, which allows natural
propagation and sanitization of overflown values.
3. We implement a prototype, IntTracker, as an exten-
sion of the GCC compiler [2]. Static taint analysis is
used to select integer operations along critical paths.
It also checks the presence of fixed patterns of widely
used sanitizations to exclude parts of the selected in-
teger operations. IntTracker detects integer overflows
through postcondition test [41][33]. Once an integer
overflow is detected, IntTracker poisons the overflown
value. Guards are inserted to memory sinks to detect
if poisonous values can reach these sinks.
4. Experimental results show that IntTracker is effective
in detecting harmful IO2BO vulnerabilities while by-
passing un-harmful ones, which substantially improves
the state of the art. Specifically, IntTracker could catch
all the 600 IO2BO vulnerabilities in the SAMATE’s
Juliet test suite [26] and 14 harmful IO2BO bugs in
real world. Furthermore, as for the patched code for
20 real-world IO2BO bugs with sanitization routines,
IntTracker only reports one IO2BO (i.e. one false posi-
tive) whereas IntPatch reports all of them. At last, Int-
Tracker has a negligible performance overhead (0.69%
on average).
Outline. The rest of this pap er is organized as follows. Sec-
tion 2 presents the design of IntTracker. Section 3 describes
implementation details. Section 4 presents the experimental
results. Limitations, related work and conclusion are dis-
cussed in Section 5, Section 6 and Section 7, respectively.
2. DYNAMIC TRACKING TECHNIQUE
2.1 Problem Definition
Inspired by discussions in Section 1, the occurrence of an
IO2BO vulnerability can be described as a process, in which
tainted data is first introduced by the user at a source point,
then overflow occurs at some point along its propagation to
a memory sink. Along its propagation path, tainted data
harmful IO2BO := Taint-source; [Arith_op;]
N
IO_op; [Arith_op;]
M
MEM;
anticipated IO2BO := Taint-source; [Arith_op;]
N
IO_op; Santz;
IO_op, Arith_op {+, -, *, <<}
MEM {malloc, memcpy, strncpy, realloc, }
Figure 1: IO2BO vulnerability description.
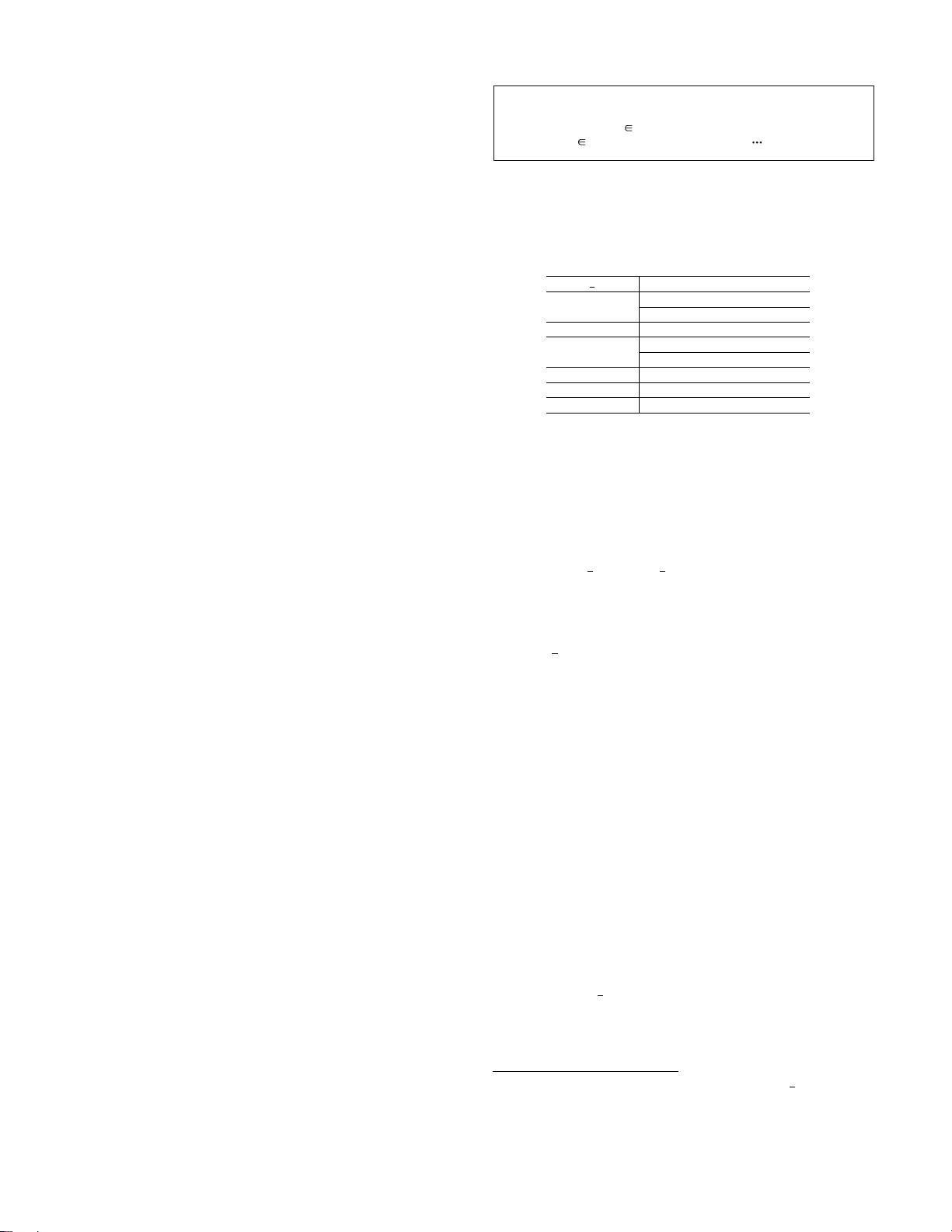
Table 1: Postcondition test. The subscript s indi-
cates a signed operation; the subscript u indicates
an unsigned operation.
Arith op Postcondtion Test
x = o
1
+
s
o
2
(o
1
> 0
∧
o
2
> 0
∧
x > 0)
∨
(o
1
< 0
∧
o
2
< 0
∧
x > 0)
x = o
1
+
u
o
2
x < o
1
∨
x < o
2
x = o
1
−
s
o
2
(o
1
< 0
∧
o
2
> 0
∧
x > 0)
∨
(o
1
> 0
∧
o
2
< 0
∧
x < 0)
x = o
1
−
u
o
2
o
1
< o
2
x = o
1
∗
s/u
o
2
x = 0
∧
x/o
1
= o
2
x = o
1
≪ o
2
x ≫ o
1
= o
2
would undergo a number of integer arithmetic operations.
Therefore, we can formally define the process of an IO2BO
vulnerability as shown in Figure 1.
Specifically, Taint-source denotes program points reading
values from users. It is the start of an IO2BO vulnerability,
introducing tainted (untrusted) data into programs. MEM
is memory manipulation routines, acting as sinks for taint-
ed data. Arith op and IO op are the operations on taint-
ed data along the path from Taint-source to MEM. Here,
we only consider arithmetic operations which could change
the concrete value of tainted data
2
. The superscript N and
M indicate the corresponding operation might occur several
times. IO op is the point where an integer overflow happens,
including addition, subtraction, multiplication and left-shift
operations in either signed or unsigned type. In addition,
as for anticipated IO2BOs, Santz indicates sanitization rou-
tines that are used to prevent overflown data from flowing
into MEM.
Our goal is to detect harmful IO2BOs and bypass the
anticipated IO2BOs.
2.2 Sanitization Routines
Experienced developers often anticipate the possibility of
overflows and insert sanitization routines after the overflow
sites to prevent overflown values from affecting further pro-
gram execution.
Postcondition test [33] is widely used as sanitization rou-
tines by developers to prevent integer overflows in advance
or to patch buggy code. The intuition of postcondition test
is to utilize the mismatch between an overflown value and
the expected value to detect overflow. We call them Santz-
postcond for short. Table 1 shows the details. As Santz-
postcond is of fixed patterns, we may exclude the check-
s for some Arith op’s by checking statically whether Santz-
postcond is present after them.
Meanwhile, there also exist other sanitization routines,
where developers usually leverage program characteristics
and employ program specific checks to sanitize overflown
2
Note that we do not consider division as Arith op just like
IntPatch [41]. Divisions are very rare along critical paths
according to our study of the 183 CVE IO2BO bugs.









