"深入理解哈希表:Java数据结构第四章大学内部资料 Lecture 61"
需积分: 0 97 浏览量
更新于2024-04-10
收藏 124KB PPT 举报
In this lecture, we delved into the topic of hash tables, which are a fundamental data structure in computer science. Hash tables are used to store key-value pairs, where each key is unique and maps to a specific value.
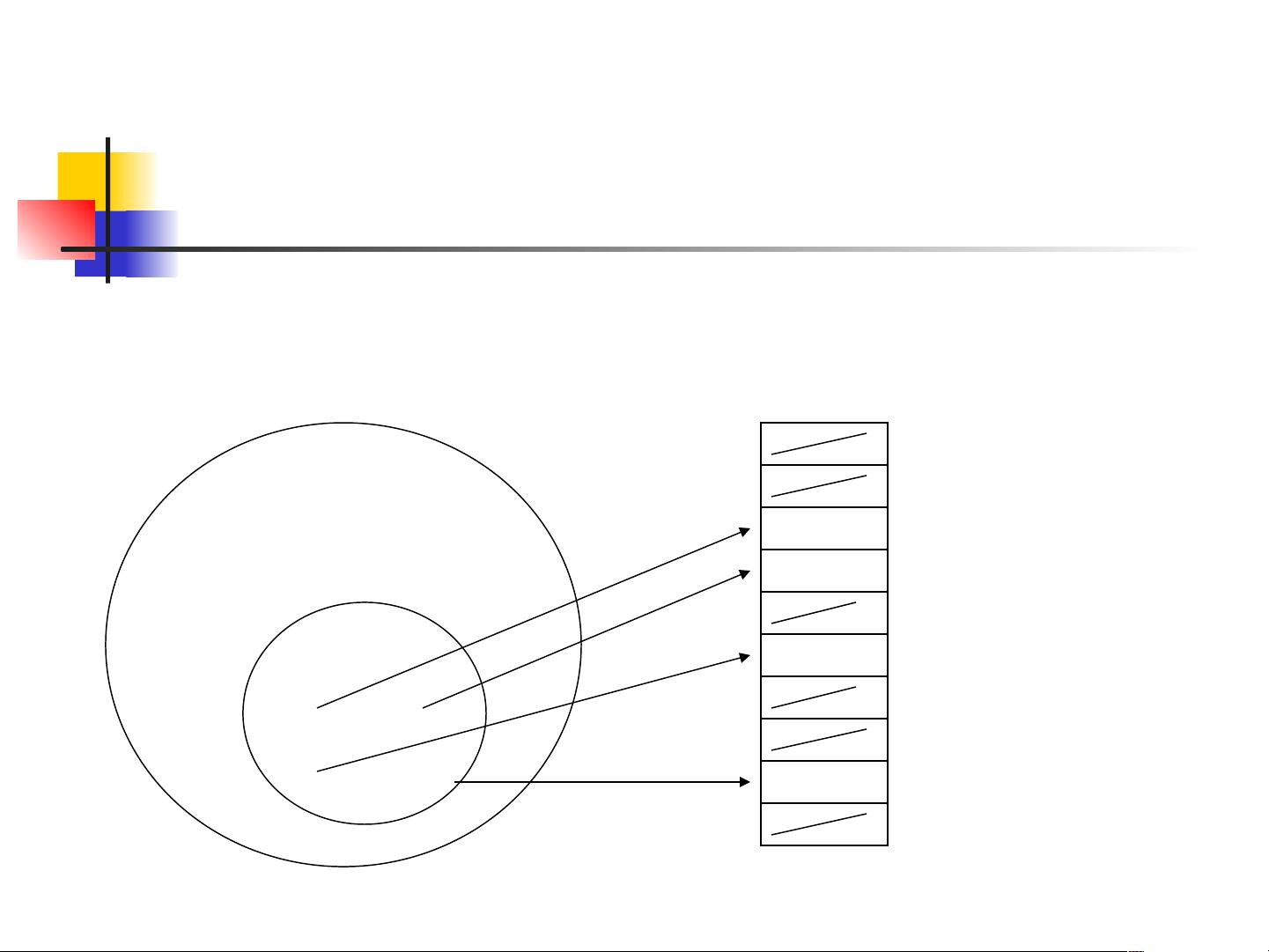
One of the key advantages of hash tables is their constant time complexity for basic operations such as insertion, deletion, and retrieval. This is achieved through the use of a hash function, which generates a unique index for each key in the hash table.
However, collisions can occur when two keys map to the same index due to the finite size of the hash table. There are several techniques for handling collisions, such as chaining and open addressing. Chaining involves storing multiple key-value pairs at the same index, while open addressing involves finding an alternative index for the colliding key.
We also discussed various applications of hash tables, including storing dictionaries, implementing caches, and optimizing database queries. Hash tables are widely used in programming languages such as Java, Python, and C++ due to their efficiency and versatility.
In conclusion, hash tables are a powerful data structure that play a crucial role in computer science and software development. By understanding how hash tables work and how to effectively handle collisions, programmers can design more efficient and scalable algorithms for a wide range of applications.
126 浏览量
1604 浏览量
1272 浏览量
190 浏览量
143 浏览量
270 浏览量
Peter_Parker
- 粉丝: 10
- 资源: 41
最新资源
- 用友NC凭证设置,如何进入模板设置界面,如何使用模板编辑器
- oracle biee 商务智能
- Google 搜索引擎优化入门指南
- More Effective C++
- 详细介绍计算机字符集的文档
- winsock_io方法
- 使用Eclipse开发Jsp
- IPv6网络管理与运营支撑系统的研究与设计
- Oracle RAC日常维护指令
- 一个好的ejb3.0帮助文档
- Switchvox AA60 用户手册
- 《信息技术学业水平测试模拟试卷》 单项选择题部分
- 2008年9月计算机等级考试网络工程师 真题及答案
- 《信息技术学业水平测试模拟试卷》 综合分析题部分
- 一个好的jasperreport中文帮助文档
- VOIP基本原理及相关技术
 已收录资源合集
已收录资源合集