A Port Hopping Based DoS Mitigation Scheme in SDN Network
Liancheng Zhang, Yi Guo, Huiqiang Yuwen
China National Digital Switching System Engineering
and Technological Research Center
Zhengzhou City, China
e-mail: liancheng17@gmail.com
Yu Wang
School of Computer and Communication Engineering
Zhengzhou University of Light Industry
Zhengzhou City, China
e-mail: stonchor@163.com
Abstract—In order to resist DoS attack, taking advantages of
SDN network’s logically centralized control and network
programmable features, a port hopping based DoS mitigation
scheme in SDN network is proposed, which moves port
hopping function forward to SDN controller and presents a
timestamp feedback based hopping synchronization method.
This proposed scheme not only can reduce protected server’s
cost caused by port hopping, earlier detect and filter malicious
packets than traditional port hopping schemes, but also can
resist port scanning and internal attack. Theoretical analysis
and experimental results show that this proposed scheme can
effectively defend against DoS attack and port scanning
without consuming many resources on SDN controller.
Keywords-software defined network; denial of service; port
hopping; moving target defense; timestamp feedback
I. INTRODUCTION
Current denial of service (DoS) attack resistance methods
of software defined network (SDN) focus on DoS attack
detection or defense [1-3] for specific DoS attacks, but few
active defense method has been put forward.
Moving target defense (MTD) [4, 5] abandons the way of
building a defect-free defense system to protect network
security, and develops a mechanism by irregularly changing
network parameters over time to improve the attacker’s
complexity and cost. In this way, MTD can limit the leakage
of vulnerabilities and reduce the success rate of attacks.
Port hopping (PH) is a typical kind of MTD technology
[6, 7], which borrows idea from frequency hopping
communication and dynamically maps service ports to
unused and/or random ports. Port hopping technologies can
confuse potential attackers and increase their attack cost, as
they can’t locate opened ports used by network services.
This paper introduces the port hopping technology to
resist DoS attack in SDN network, which can improve the
proactive defense ability for defending against DoS attack in
SDN network with a relatively small price and cost.
II. P
ORT HOPPING BASED DOSMITIGATION SCHEME
Making full use SDN network’s features, such as
network programmable, logically centralized control and
control plane and data plane separation, a port hopping based
DoS mitigation (PH-DM) scheme is proposed, which locates
the port hopping function in SDN controller (cooperating
with OpenFlow switches), reduces the load on the server and
resists internal attackers at the same time.
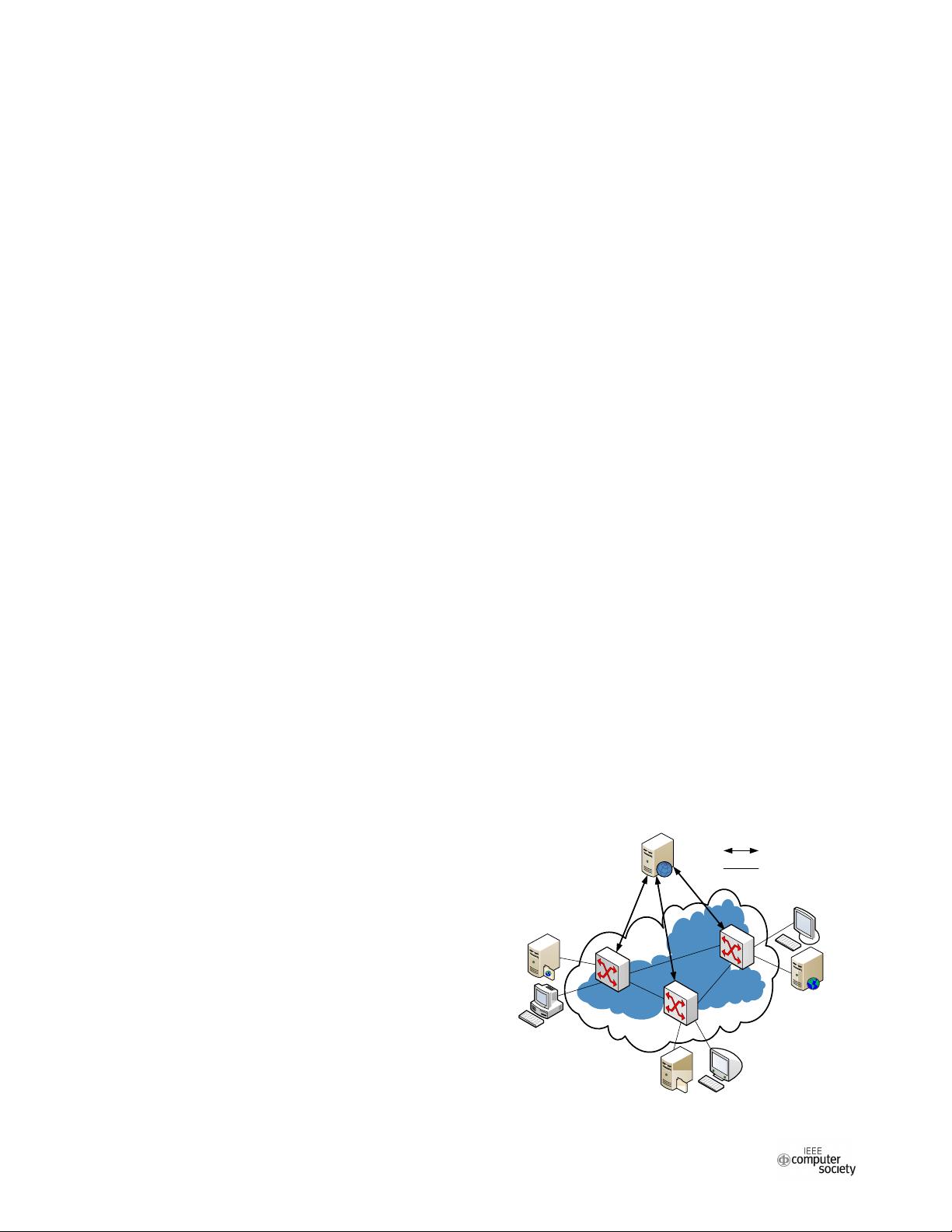
A. Basic Process and Architecture of the PH-DM Scheme
According to SDN network’s logically centralized
control and network programmable features, port hopping
module on the server side is forwarded to the SDN controller,
which reduces large load caused by port hopping on the
server. SDN controller (cooperating with OpenFlow switches)
acts as a DoS attack filtering gateway, and checks the
network connection launched by the clients, which mainly
checks whether the destination port of the connection suits
the opened port used in the current time slot. If the two ports
are the same, SDN controller will install specific flow entries
to the corresponding OpenFlow switches along the
transmission path, and the packets of this connection will be
transmitted to the target server if they match these installed
flow entries, by this way, the trusted and authorized clients
can communicate with the target server normally. If the
destination port differs from the opened port, this connection
will be considered to be malicious, which will be discarded
directly and won’t be forwarded, then illegal and malicious
network flows can’t access to the SDN network.
For the convenience of distinction, this paper defines the
protected server as the server and defines the host that will
access the server as the client. The specific architecture of
the PH-DM scheme is shown in Fig. 1.
Client
Server
Control channel
Data channel
OpenFlow switch 1
OpenFlow switch 2
OpenFlow switch 3
SDN
controller
Figure 1. Framework of the PH-DM scheme.
2016 12th International Conference on Computational Intelligence and Security
978-1-5090-4840-3/16 $31.00 © 2016 IEEE
DOI 10.1109/CIS.2016.76
314









