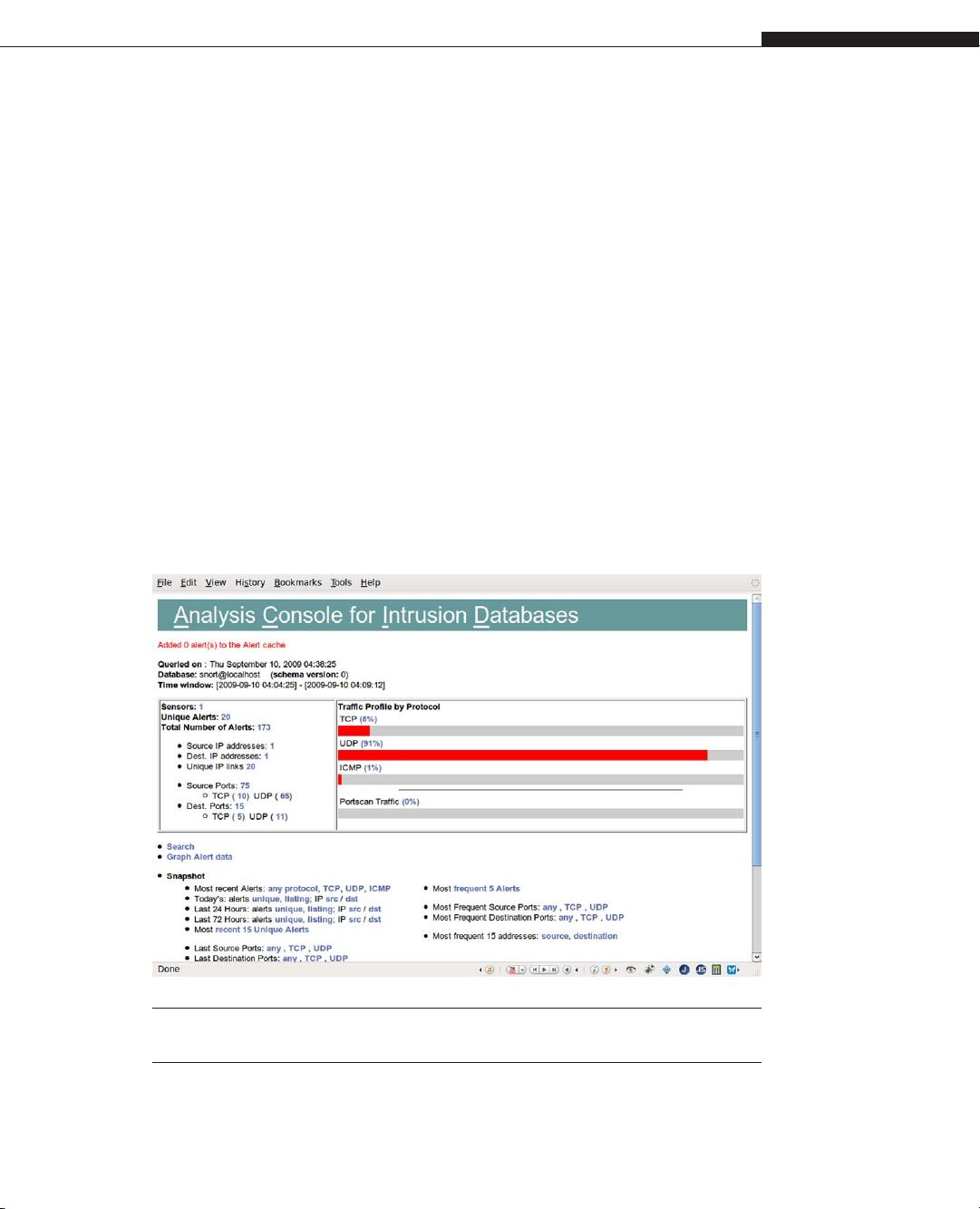
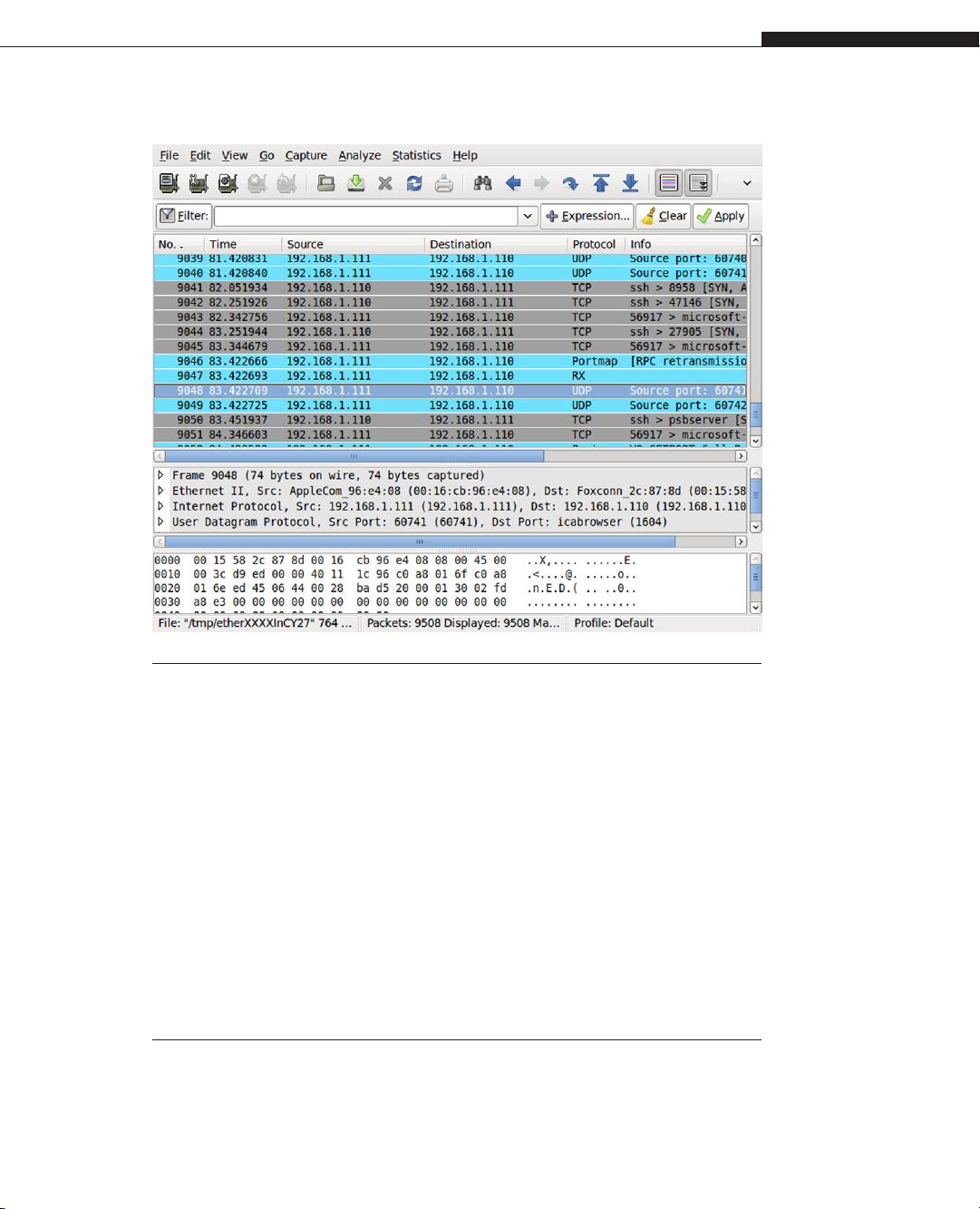
CHAPTER 1 Denial of Service20
An alternative if you use an ISP is to purchase additional capacity for the duration
of the DDoS attack. This adaptive provisioning can be provided via burstable circuits,
which can carry additional capacity if necessary. You typically pay a rate based on
your average use of the connection. Since attackers often “tune” the attack while it is
in progress, you will still need to carefully monitor the attack to determine how best
to respond. For example, an attack may change from trying to overload a server to
exploiting a network protocol.
THE FUTURE OF DENIAL OF SERVICE
Malware is now big business, and operating botnets has become a source of signifi-
cant income. Developing a large botnet is a financial investment. Likewise, consider-
able economic activity is moving onto the Internet, with some companies completely
dependent on the Internet for their business, including Google and Amazon.com. All
this creates a marketplace to supply more advanced attack and defense capabilities.
Attack
Based in St. Petersburg, the Russian Business Network (RBN) is a hosting organiza-
tion that offers “bulletproof ” hosting and a variety of other services, including botnet
rental, so you don’t even need to create your own botnet.
EE
If you can lease time on
an existing botnet, and use it effectively for a DDoS attack, you have successfully
reduced a technical challenge to a simple matter of paying some money.
This is probably the shape of the future in DDoS. Creating and controlling a large
botnet is still somewhat challenging, and also presents legal risks. It is also the case
that botnets can be “hijacked” if someone else, perhaps another criminal enterprise,
gets access to the command and control channels.
Current trends show that the malware world is becoming less vertically integrated
and more specialized. Many components of successful malware are not, by them-
selves, illegal. It is thus perfectly reasonable to set up shop and develop and sell
software to enable DDoS attacks, so long as the software has a potential legal appli-
cation, as well. For example, software used to protect intellectual property and thwart
reverse engineering can also be used to harden malware against reverse engineering,
making it hard to discover just what a particular kind of malware is doing, and how
to counteract it. Digital rights management (DRM) techniques can cloak a malware
payload until the time arrives to launch a DDoS attack. While the tools to conduct a
DDoS attack are improving, fortunately so are the tools to defend against an attack.
EE
RBN is the originator of the MPack malware kit, which you can purchase for between $500 and
$1000 (at the time of writing). Included with this kit is technical support and regular updates to the
vulnerabilities it can exploit. Additional functionality can be purchased to target specific vulnerabilities
or to cloak the software against antimalware and antivirus programs. MPack includes a Web-based
management console to allow you to track its progress as it infects machines.