The Fog Computing Paradigm: Scenarios and
Security Issues
Ivan Stojmenovic
SIT, Deakin University, Burwood, Australia
and
SEECS, University of Ottawa, Canada
Email: stojmenovic@gmail.com
Sheng Wen
School of Information Technology,
Deakin University,
220 Burwood Highway, Burwood, VIC, 3125, Australia
Email: wesheng@deakin.edu.au
Abstract—Fog Computing is a paradigm that extends Cloud
computing and services to the edge of the network. Similar
to Cloud, Fog provides data, compute, storage, and application
services to end-users. In this article, we elaborate the motivation
and advantages of Fog computing, and analyse its applications
in a series of real scenarios, such as Smart Grid, smart traffic
lights in vehicular networks and software defined networks. We
discuss the state-of-the-art of Fog computing and similar work
under the same umbrella. Security and privacy issues are further
disclosed according to current Fog computing paradigm. As an
example, we study a typical attack, man-in-the-middle attack,
for the discussion of security in Fog computing. We investigate
the stealthy features of this attack by examining its CPU and
memory consumption on Fog device.
Index Terms—Fog Computing, Cloud Computing, Internet of
Things, Software Defined Networks.
I. INTRODUCTION
C
ISCO recently delivered the vision of fog computing
to enable applications on billions of connected devices,
already connected in the Internet of Things (IoT), to run
directly at the network edge [1]. Customers can develop,
manage and run software applications on Cisco IOx framework
of networked devices, including hardened routers, switches
and IP video cameras. Cisco IOx brings the open source Linux
and Cisco IOS network operating system together in a single
networked device (initially in routers). The open application
environment encourages more developers to bring their own
applications and connectivity interfaces at the edge of the
network. Regardless of Cisco’s practices, we first answer the
questions of what the Fog computing is and what are the
differences between Fog and Cloud.
In Fog computing, services can be hosted at end devices
such as set-top-boxes or access points. The infrastructure of
this new distributed computing allows applications to run as
close as possible to sensed actionable and massive data, com-
ing out of people, processes and thing. Such Fog computing
concept, actually a Cloud computing close to the ‘ground’,
creates automated response that drives the value.
Both Cloud and Fog provide data, computation, storage
and application services to end-users. However, Fog can be
distinguished from Cloud by its proximity to end-users, the
dense geographical distribution and its support for mobility
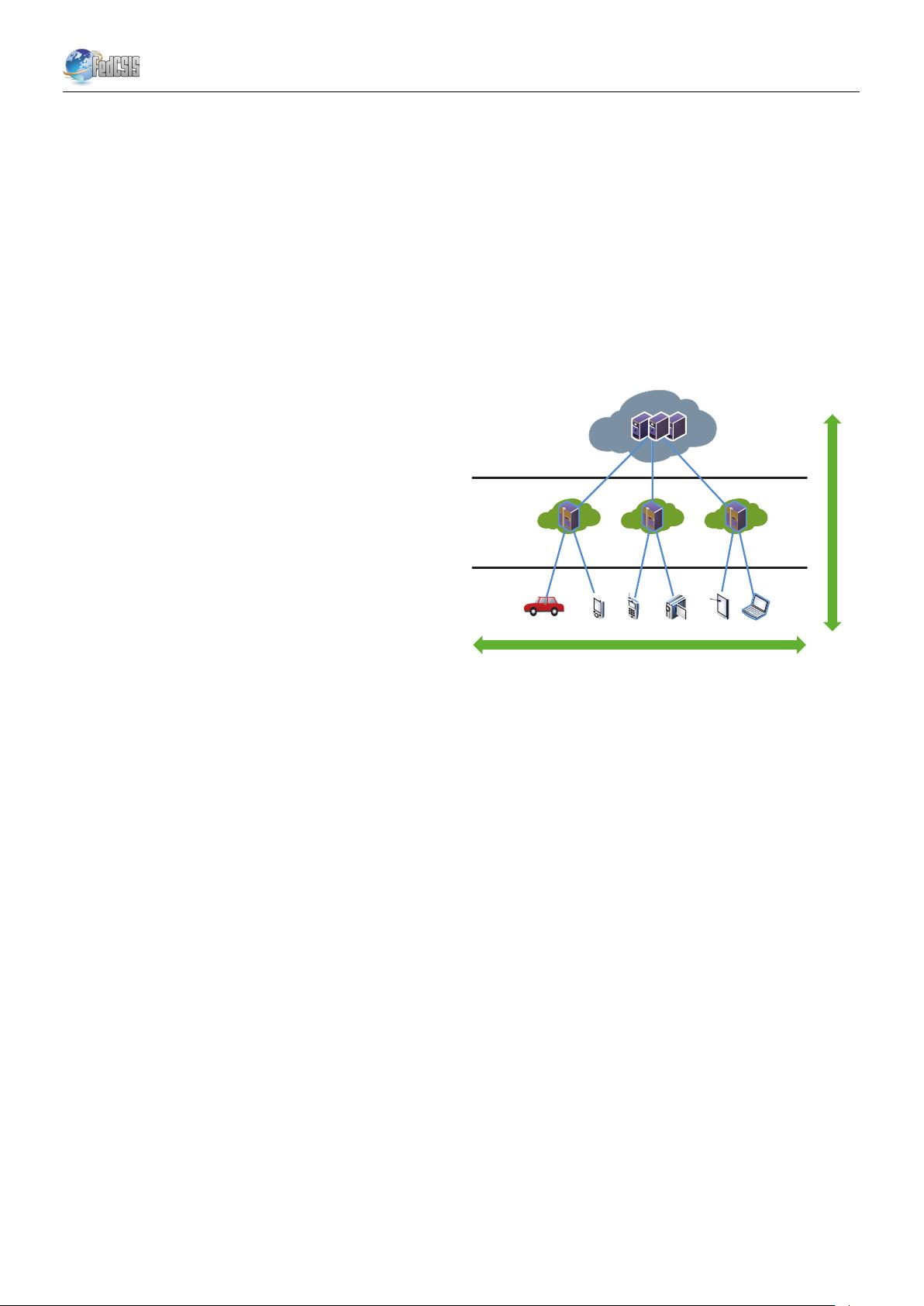
[2]. We adopt a simple three level hierarchy as in Figure 1.
Fig. 1. Fog between edge and cloud.
In this framework, each smart thing is attached to one of Fog
devices. Fog devices could be interconnected and each of them
is linked to the Cloud.
In this article, we take a close look at the Fog computing
paradigm. The goal of this research is to investigate Fog
computing advantages for services in several domains, such as
Smart Grid, wireless sensor networks, Internet of Things (IoT)
and software defined networks (SDNs). We examine the state-
of-the-art and disclose some general issues in Fog computing
including security, privacy, trust, and service migration among
Fog devices and between Fog and Cloud. We finally conclude
this article with discussion of future work.
II. WHY DO WE NEED FOG?
In the past few years, Cloud computing has provided many
opportunities for enterprises by offering their customers a
range of computing services. Current “pay-as-you-go” Cloud
computing model becomes an efficient alternative to owning
and managing private data centres for customers facing Web
applications and batch processing [3]. Cloud computing frees
the enterprises and their end users from the specification of
many details, such as storage resources, computation limitation
and network communication cost. However, this bliss becomes