2006 IEEE TRANSACTIONS ON FUZZY SYSTEMS, VOL. 26, NO. 4, AUGUST 2018
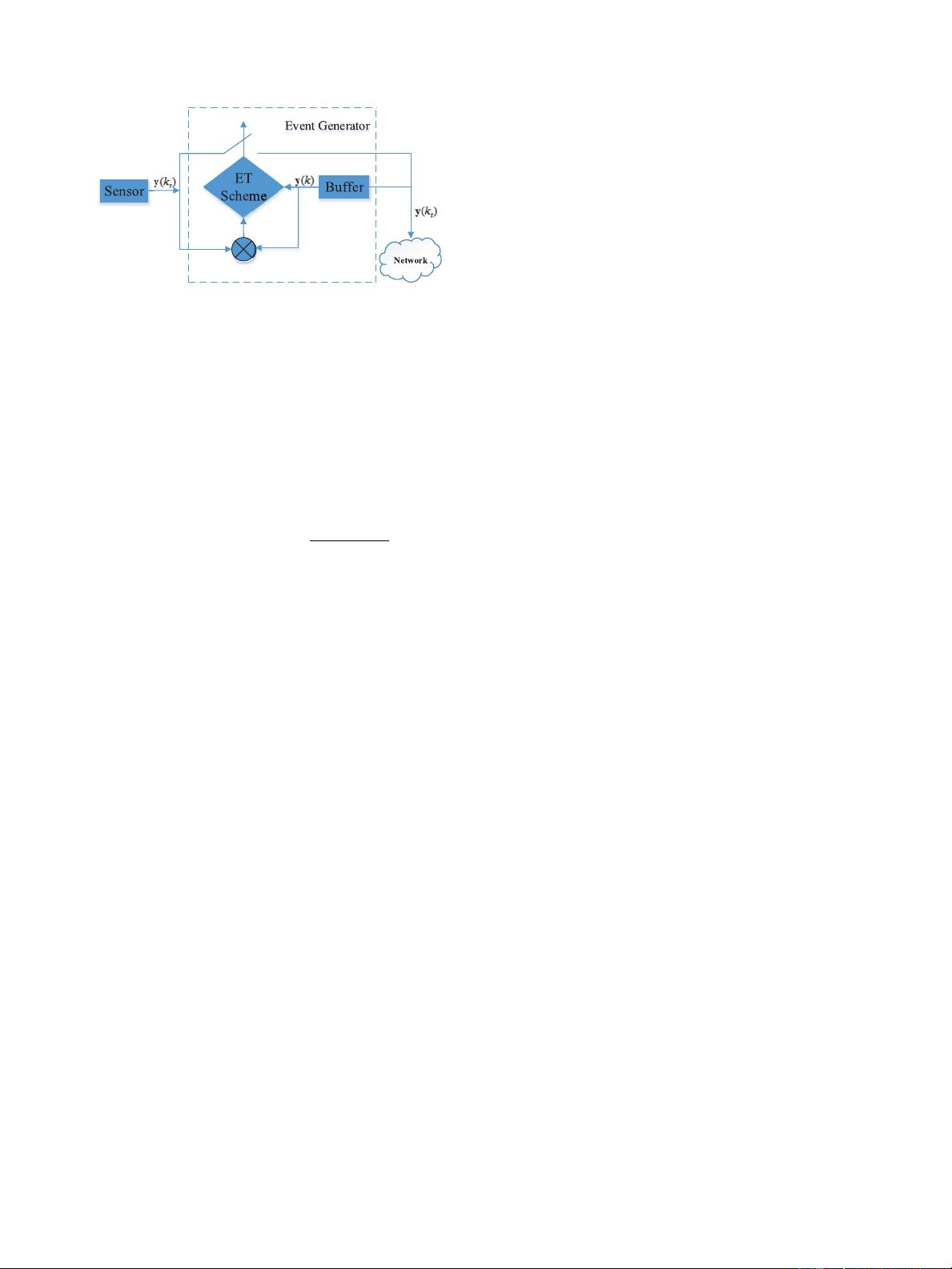
Fig. 1. Transmitting-data generator.
the noise input signal, respectively, which are considered
to belong to
2
[0, ∞),fori ∈ S {1, 2,...,r}, r is the
number of IF–THEN rules; μ
i1
,...,μ
ip
are the fuzzy sets;
θ(k)=[θ
1
(k),θ
2
(k),...,θ
p
(k)] are the premise variables vec-
tor; and ψ(k) stands for the initial condition. A
i
, B
i
, C
i
,
D
i
, and E
i
are appropriately dimensioned matrices, which
are known constant matrices in advance, and h
2
is a pos-
itive integer, which represents the maximum bounds of the
delay caused by network-induced delays. The fuzzy basis
functions are given by h
i
(θ(k))
ν
i
(θ(k ))
r
i =1
ν
i
(θ(k ))
,ν
i
(θ(k))
p
j=1
μ
ij
(θ
j
(k)), with μ
ij
(θ
j
(k)) standing for the grade of
membership of θ
j
(k) in μ
ij
. Thus, we obtain
ν
i
θ(k)
0,h
i
θ(k)
0,i∈ S,
r
i=1
h
i
θ(k)
=1.
Assume that the input variables u(k) cannot effect the premise
variables θ(k). Given a pair of
x(k),u(k)
, the above discrete-
time fuzzy model is given in the following compact form:
x(k +1)= A(k)x(k)+B(k)u(k)+D(k)w(k)+E(k)f(k)
y(k)= C(k)x(k) (2)
where
⎧
⎪
⎨
⎪
⎩
A(k)
r
i=1
h
i
θ(k)
A
i
,B(k)
r
i=1
h
i
θ(k)
B
i
C(k)
r
i=1
h
i
θ(k)
C
i
,D(k)
r
i=1
h
i
θ(k)
D
i
E(k)
r
i=1
h
i
θ(k)
E
i
.
Event-Triggered Scheme:
To reduce data transmissions and save the network bandwidth
resources, we propose an ETS in this part, which determines
whether the system output y(k) should be transmitted over the
communication links or not. As shown in Fig. 1, the updated
sampled state is sent out by comparing the latest transmitted
data y(k
t
) at the triggering instant k
t
with the current data y(k)
at the current sampling instant k. Thus, once y(k
t
) is sent, the
next triggered time is determined by
k
t+1
=inf
k
k>k
t
y(k) − y(k
t
)
T
Ω
y(k) − y(k
t
)
>σ
α
σ
β
y
T
(k
t
)Ωy(k
t
)
(3)
where Ω is a symmetric positive-definite matrix to be determined
later, and σ
α
and σ
β
are given parameters.
Remark 1: Suppose that σ
α
is chosen as σ
α1
and σ
α2
with
σ
α1
<σ
α2
, while σ
β
is selected as σ
β 1
and σ
β 2
with σ
β 1
>σ
β 2
.
The selection criteria for σ
α1
, σ
α2
, σ
β 1
, and σ
β 2
are determined
by the following discussion: if the network bandwidth utilization
rate is below a predefined value δ% with δ ∈
0, 100
, σ
α
is
selected as σ
α1
; otherwise, σ
α
is selected as σ
α2
; for a specified
value ε ∈
0, 1
greater than the fault occurrence probability, σ
β
is selected as σ
β 1
; otherwise, σ
β
is selected as σ
β 2
. Therefore,
compared with the existing ETS, the proposed event-triggered
mechanism considering the adjustable parameters σ
α
and σ
β
introduces more flexibility.
Hence, for any k ∈
k
t
,k
t+1
− 1
, the above event-triggering
condition in (3) can be formulated as
y(k) − y(k
t
)
T
Ω
y(k) − y(k
t
)
σ
α
σ
β
y
T
(k
t
)Ωy(k
t
).
(4)
Remark 2: Note that the event-triggering condition in [10] is
x(k) − x(k
s
)
T
W
x(k) − x(k
s
)
σx
T
(k)Wx(k)
while the condition in [32] is described as
x(k) − x(s
l
)
T
Φ
i
x(k) − x(s
l
)
ε
i
x
T
(k)Φ
i
x(k).
Compared with the event-triggering conditions in [10] and
[32], the event-triggering condition (4) in our work only
calculates the threshold value at each triggered moment,
namely, σ
α
σ
β
y
T
(k
t
)Ωy(k
t
) in (4) is constant on the inter-
val k ∈
k
t
,k
t+1
− 1
. Relatively, σx
T
(k)Wx(k) in [10] and
ε
i
x
T
(k)Φ
i
x(k) in [32] are computed at every sampling instant.
Obviously, the event-triggering condition in ( 4) simplifies the
computation, while ensuring that the burden of the network
communication is reduced and the bandwidth resources are
saved. Furthermore, this method can also be used in the wire-
less network to save the transmission energy and increase the
battery lifespan. Especially, when σ
α
=0or σ
β
=0, the ETS
is changed into the time-triggered mechanism.
To detect the occurrence of the faults by generating the resid-
ual signal, the fuzzy fault detector and controller is constructed
as the following form.
Fault Detector and Controller:
Rule j: IF θ
1
(k
t
) is μ
j1
and θ
2
(k
t
) is μ
j2
and ··· and θ
p
(k
t
)
is μ
jp
,THEN
x
f
(k +1)= A
fj
x
f
(k)+B
fj
ˆy(k)+D
fj
x
fn
(k)
y
f
(k)= C
fj
x
f
(k)
u(k)= K
j
x
f
(k)
r(k)= y
f
(k) − f(k) (5)
where j ∈ S, x
f
(k) denotes the fault detector state, y
f
(k) is the
measurement output of the fault detector, u(k) represents the
controller output, ˆy(k) is the event-triggering vector effected by
network-induced delays and packet dropouts, x
fn
(k) is illus-
trated in (11) by artificial construction, and r(k) is the residual
signal. A
fj
, B
fj
, C
fj
, D
fj
, and K
j
are the detector and con-
troller parameters to be designed subsequently.
Authorized licensed use limited to: SOUTH CHINA UNIVERSITY OF TECHNOLOGY. Downloaded on March 28,2020 at 13:25:20 UTC from IEEE Xplore. Restrictions apply.









