Hidden-Token Searchable Public-Key Encryption
Cong Zuo
†
, Jun Shao
†∗
, Zhe Liu
‡
, Yun Ling
†
and Guiyi Wei
†
†
School of Computer and Information Engineering, Zhejiang Gongshang University, Hangzhou, China
Email: zuocong10@gmail.com, chn.junshao@gmail.com, yling@zjgsu.edu.cn, weigy@zjgsu.edu.cn
‡
APSIA, Interdisciplinary Centre for Security, Reliability and Trust (SnT), University of Luxembourg, Luxembourg
Email: sduliuzhe@gmail.com
Abstract—In this paper, we propose a variant of searchable
public-key encryption named hidden-token searchable public-key
encryption with two new security properties: token anonymity
and one-token-per-trapdoor. With the former security notion,
the client can obtain the search token from the data owner
without revealing any information about the underlying keyword.
Meanwhile, the client cannot derive more than one token from
one trapdoor generated by the data owner according to the latter
security notion. Furthermore, we present a concrete hidden-
token searchable public-key encryption scheme together with the
security proofs in the random oracle model.
Index Terms—Searchable Encryption, Public-Key, Hidden-
Token, Random Oracle Model
I. INTRODUCTION
In recent years, the development and deployment of Inter-
net of Things (IoT) have gained substantial attention in the
industry and research community since it enables people to
collect data everywhere including environment, infrastructures
and businesses. However, it is not easy to store this huge
amount of information locally. The popular solution nowadays
is to outsource these data to a third party (e.g. the cloud).
While these data are the assets of the one who implemented
the devices of IoT, they should be encrypted before outsource,
which at the same time jeopardizes the usefulness of these
data, such as searchability.
To solve this dilemma between usefulness and confidential-
ity of data, many research efforts have been proposed, e.g.
Oblivious RAM (ORAM) [1], [2], Private Information Re-
trieval (PIR) [3], [4] and Searchable Encryption (SE) [5], [6],
[7], [8]. Among these, searchable encryption, which enables
searchability on ciphertexts, is the most promising technique.
For instance, the SE scheme in [8] allows many data sources
to generate encrypted index of the data and the data owner
to delegate the searchability by giving search trapdoors to
the clients. By using this SE scheme, the devices of IoT can
encrypt the collected data, and upload the resulting ciphertexts
with the index generated by using this SE scheme to the cloud
directly. Meanwhile, the data owner can generate the search
trapdoor according to the query from the client, who can later
use the search token generated from the trapdoor to ask the
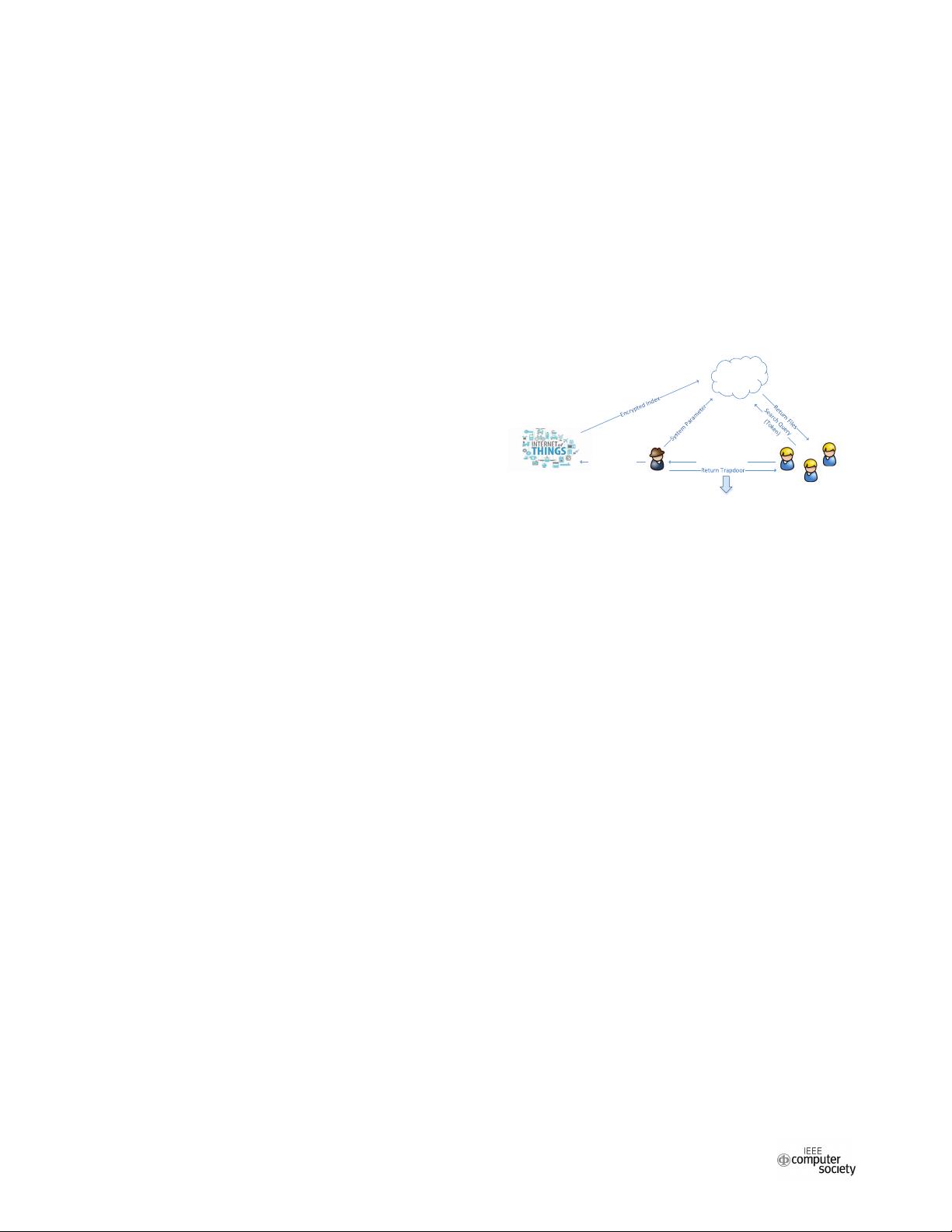
cloud do the search on the index. The high level description
of the above framework is given in Fig. 1.
∗
Corresponding author.
Cloud
Query for TrapdoorSystem Parameter
Data
Owner
IoT
Clients
The Data Owner has no idea about
the underlying keyword!
1a
1b
2
6
5
3
4
Fig. 1. Architecture of our framework
In most of the existing SE schemes, the data owner is
usually considered as trusted, while the cloud and the client
are considered as malicious. They focus on how to protect the
confidentiality of the trapdoor and the corresponding keyword,
while the privacy of the client is always ignored. However, in
some situations, the way how the client deals with the data
could be considered as an asset. For example, the information
of stock market and how to deal with the information are both
valuable. Hence, the keyword corresponding to the trapdoor
should be also protected. Once the client privacy (keyword
hidden) is considered, the benefit of the data owner could be
hurt. For example, without knowing the underlying keyword of
the trapdoor, the client could trick the data owner to generate
one trapdoor corresponding to many tokens. It is not good for
the data owner especially when the payment of data service
is based on how many tokens the client obtains.
To address the above challenges, in this paper, we pro-
pose a variant of searchable encryption, named hidden-token
searchable encryption. One of the important security properties
of hidden-token searchable encryption is to protect the client
privacy, i.e., the data owner cannot deduce the keyword corre-
sponding to the queried trapdoor. Besides, we also guarantee
the benefit of the data owner when the client privacy is under
protection, i.e., one trapdoor can derive only one token. The
contributions of this paper can be summarized as follows.
• To protect the client privacy while guaranteeing the ben-
efit of the data owner, we propose the concept of hidden-
token searchable encryption, including its definitions and
security models.
• We present the first concrete hidden-token searchable
encryption scheme along with its security analysis.
2017 IEEE Trustcom/BigDataSE/ICESS
2324-9013/17 $31.00 © 2017 IEEE
DOI 10.1109/Trustcom/BigDataSE/ICESS.2017.244
248









