TNC Architecture for Interoperability TCG Copyright 2017
Specification Version 2.0
Revision 13 Page 12 of 61
TCG PUBLISHED
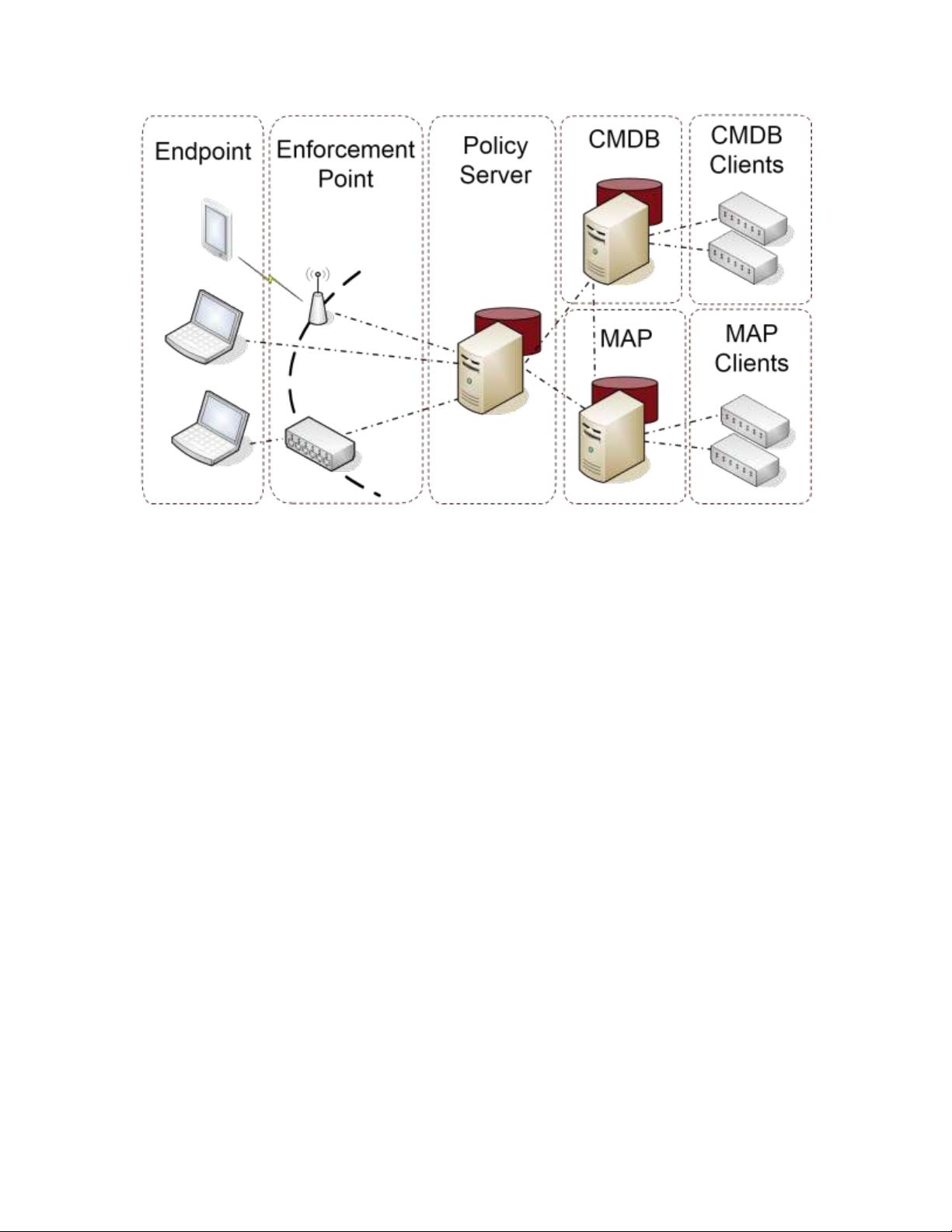
Architecture.
2.2.3 Relationship with IETF NEA
Several TNC endpoint posture-related specifications have been adopted by IETF as the basis for
the IETF Network Endpoint Assessment standards. The IETF NEA Posture Assessment [5],
Posture Broker [6], and Posture Transport [7] [8] protocols are all based on TNC interfaces. See
Section 7.1.1 for a more detailed mapping between TNC and NEA terms and concepts.
2.3 Aim and Purposes
TCG’s Trusted Network Communications (TNC) network security architecture and open
standards enable intelligent policy decisions, dynamic security enforcement, and communication
between security systems. TNC standards facilitate network and endpoint visibility, helping
network managers know who and what is on their network and whether devices are compliant
and secure. TNC standards also enable network-based access control enforcement - granting or
blocking access based on authentication, device compliance, and user behavior - and security
system integration - real-time information sharing enabling dynamic integration of network and
security products.
The aim of the TNC architecture is to provide a framework for the development of standards to
support multi-vendor solutions for:
Endpoint compliance: TNC specifies schema and protocols for standardized endpoint
posture reporting, both self-reporting and by observing parties. TNC-enabled technology
provides systems administrators the ability to know the aggregate endpoint compliance
status of their environment with near-real-time updates, and reduce the fragmentation of
endpoint posture reports in proprietary databases. This allows the data to be shared
across the network, with network and administrative tools and with other TNC
Architecture elements, to support asset management, threat detection, security
automation and vulnerability analysis use cases.
The TNC Architecture facilitates remediation of endpoints which fail posture verification
by assisting in detection of endpoints requiring remediation and providing a transport
mechanism for remediation instructions; however, it does not standardize specific
methods of remediation. See Appendix C: Assessment, Isolation, and Remediation for
details.
Control of access to resources: TNC-enabled technology can serve as a gatekeeper for
endpoints accessing sensitive resources, including but not limited to access to a given
network, particular services on the network, specific applications, and/or information.
TNC enables this control either by dynamic configuration of devices (such as switches
and firewalls) that are specifically intended to allow or deny access to resources based
on policy decisions, or by making information available to specific services, which then
used this provided information to make their own access control decisions. The result is
that TNC facilitates a coordinated, multi-level, and comprehensive approach to ensuring
that sensitive resources and actions are only available to authorized parties. See
Appendix D: Basic Message Flows for Network Admission for details.
Policy enforcement: As noted above, TNC can help prevent unauthorized endpoints and
users from accessing sensitive information and resources. TNC gives administrators a
great deal of power to defined what "unauthorized" means in each case. Decisions as to
whether a given request is authorized can hinge on many factors, including but not
limited to user identity, device identity, the degree to which the endpoint is considered
compliant with policy, time of day, location of the accessing device, type of device (e.g.,
laptop, mobile device, etc.), and other contextual information that sensors and other
parties may have reported about the requesting device and its activities. The criteria for
authorization can be as simple or sophisticated as necessary. Since TNC allows access