Proceedings of the Asia-Pacific Microwave Conference 2016
978-1-5090-1592-4/16/$31.00 ©2016 IEEE
Malicious User Detection for Wide-band
Cognitive Radio Networks
Hongxing Wu
#1
,
Xuekang Sun
#2
,
Caili Guo
*3
,
Shiyu Ren
*4
#
School of Network Education,
Beijing University of Posts and Telecommunications, Beijing, China
1
wuhongxing@bupt.edu.cn
2
Xuekang6395@126.com
*
School of Information and Communication Engineering,
Beijing University of Posts and Telecommunications, Beijing, China
3
guocaili@bupt.edu.cn
4
rsy@bupt.edu.cn
Abstract- In cooperative spectrum sensing (CSS), malicious
user (MU) sends tampered sensing result in spectrum sensing to
pose threats to cognitive radio networks (CRN), which is called
spectrum sensing data falsification (SSDF) attack. Many existing
MU detection schemes are designed for the narrow-band
environment. However, Research on MU detection schemes for
compressive sensing (CS), which has some huge advantages in
sensing wide-band spectrum, is just beginning. Because of the
high complex of reconstruction algorithms, it's necessary to
identify potential MU and then exclude the MU before
reconstructing the original signal in CS. In this paper, we
consider attack and defense behavior in CS and propose a
density-based MU detection (DBMUD) with a trusted user to
distinguish MU precisely. DBMUD maintains reliability even if
MUs are a majority. Simulation results demonstrate that
DBMUD performs well in fighting against SSDF attack
.
I. I
NTRODUCTION
Secondary user (SU) employs spectrum sensing to discover
a vacant frequency band for transmissions without causing
interference to Primary User (PU) in CRN. CS can sense
wide-band signals by using sub-Nyquist sampling technique.
According to [1], a discrete-time sparse signal can be
completely captured by a few samples over a random matrix
and reconstructed from these random samples. Meanwhile,
CSS can resist noise and shadowing in CRN. Fusion center
(FC) receives and reconstructs all sensing results to achieve
better performance than single SU [2]. CSS is vulnerable to
the threats by MU, since MU sends tampered sensing result to
FC to pose serious damage on the reliability of CSS when
launching SSDF attack.
MU detection in CSS has been surveyed in [3]. Approaches
based on Machine learning (ML) have attracted much
attention in [4]- [6] as they provide effective solutions to fight
against SSDF attack. In previous work [4], k-proximity
algorithm is employed to MU detection. Ref. [5] proves k-
means clustering with the kernel method is efficient in fighting
against SSDF attacks. A Hidden Markov Model based
approach is proposed to find MU in [6]. Although MU
detection for narrow-band has been extensively discussed,
This work is supported by Chinese National Nature Science Foundation
(61372116).
research on attack and defense in wide-band CSS has just
begun. In this paper, we discuss attack and defense strategies
in CS based on SSDF attack model in wide-band environment.
Because of high complex of reconstruction algorithm in CS,
we propose a MU detection named DBMUD to eliminate MUs
in FC before signal reconstruction. DBMUD is built on
compressive sensing matrix theory in CS and density
clustering in ML. Trusted user plays an important part in
detecting MU.
This paper is organized as follows. Section
Ⅱ
gives the
system model and preliminaries. Section
Ⅲ
presents attack
strategies in CS. Section
Ⅳ
presents DBMUD based on
density-based clustering and trusted user theorem. In section
Ⅴ
, simulation results are delivered to prove the effectiveness
of our method. Conclusion is drawn in Section
Ⅵ
.
II. S
YSTEM MODEL
&
PRELIMINARIES
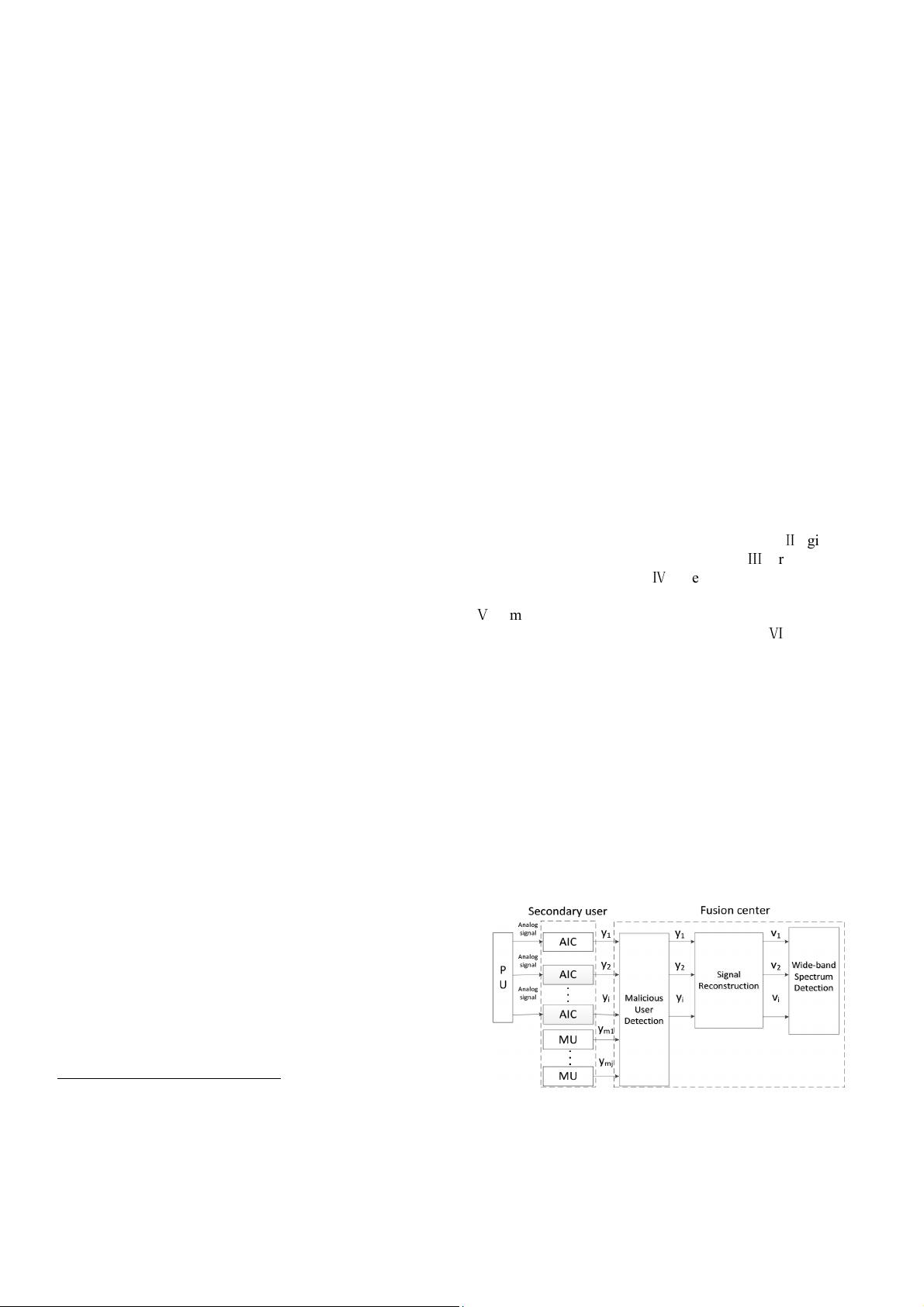
A. System model
The system model is shown in Fig.1. At first, the analog-to-
information converter (AIC) in [1] is a linear system that maps
analog signal to a discrete sequence of samples y
i
for i-th
honest SU. y
mj
is a tampered sensing result for j-th MU.
Then FC collects compressed sensing results from honest
SUs and falsified results from MUs. To deal with the security
threat, MU detection is located before signal reconstruction.
The advantage of the scheme is given below:
1. MU detection can save computing resources when CRN
suffer with SSDF attack. If FC consumes a lot of time and
memory to recover useless signals, MUs launch a successful
Figure 1. Structure of cooperative spectrum sensing with SSDF attack.









