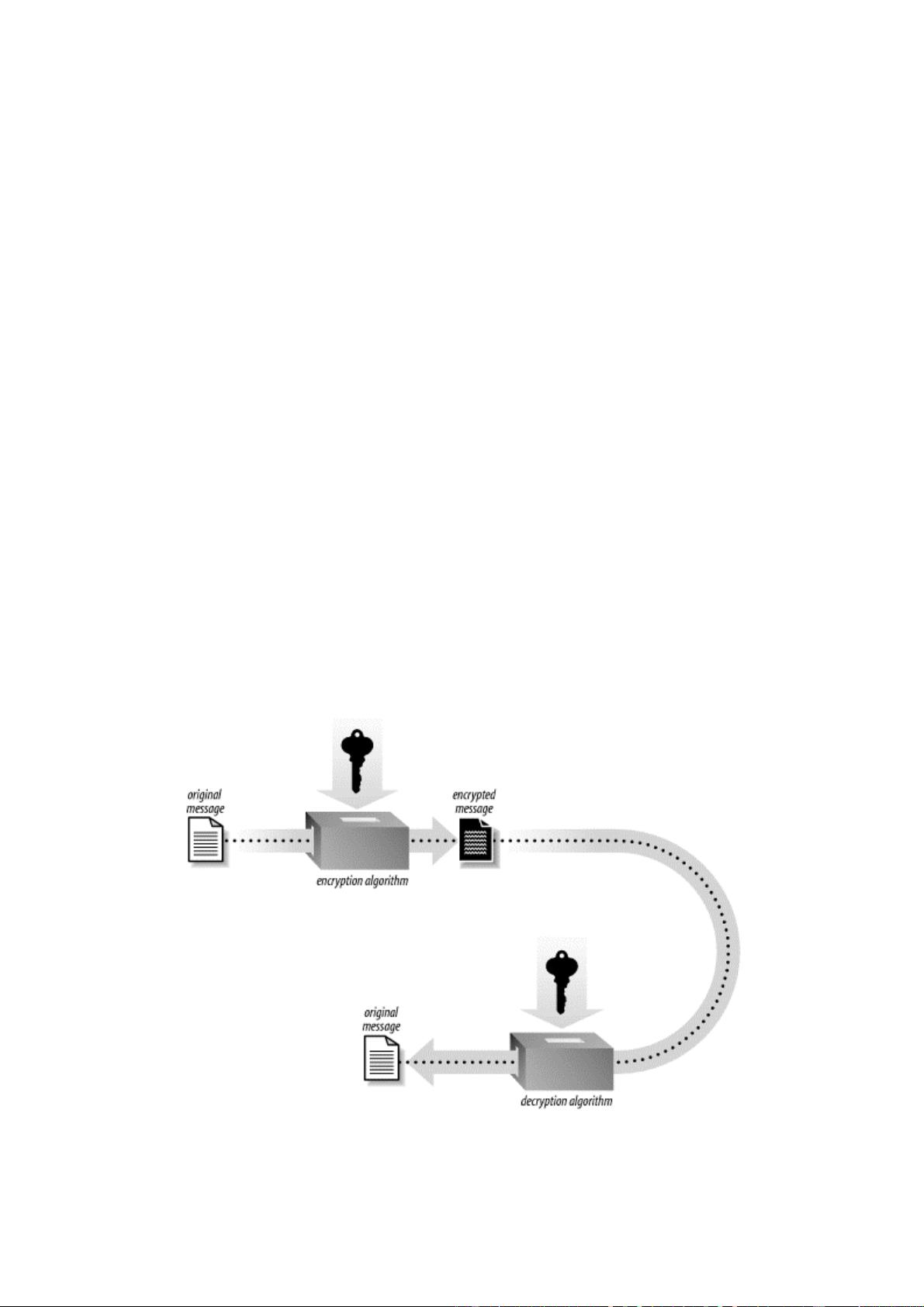
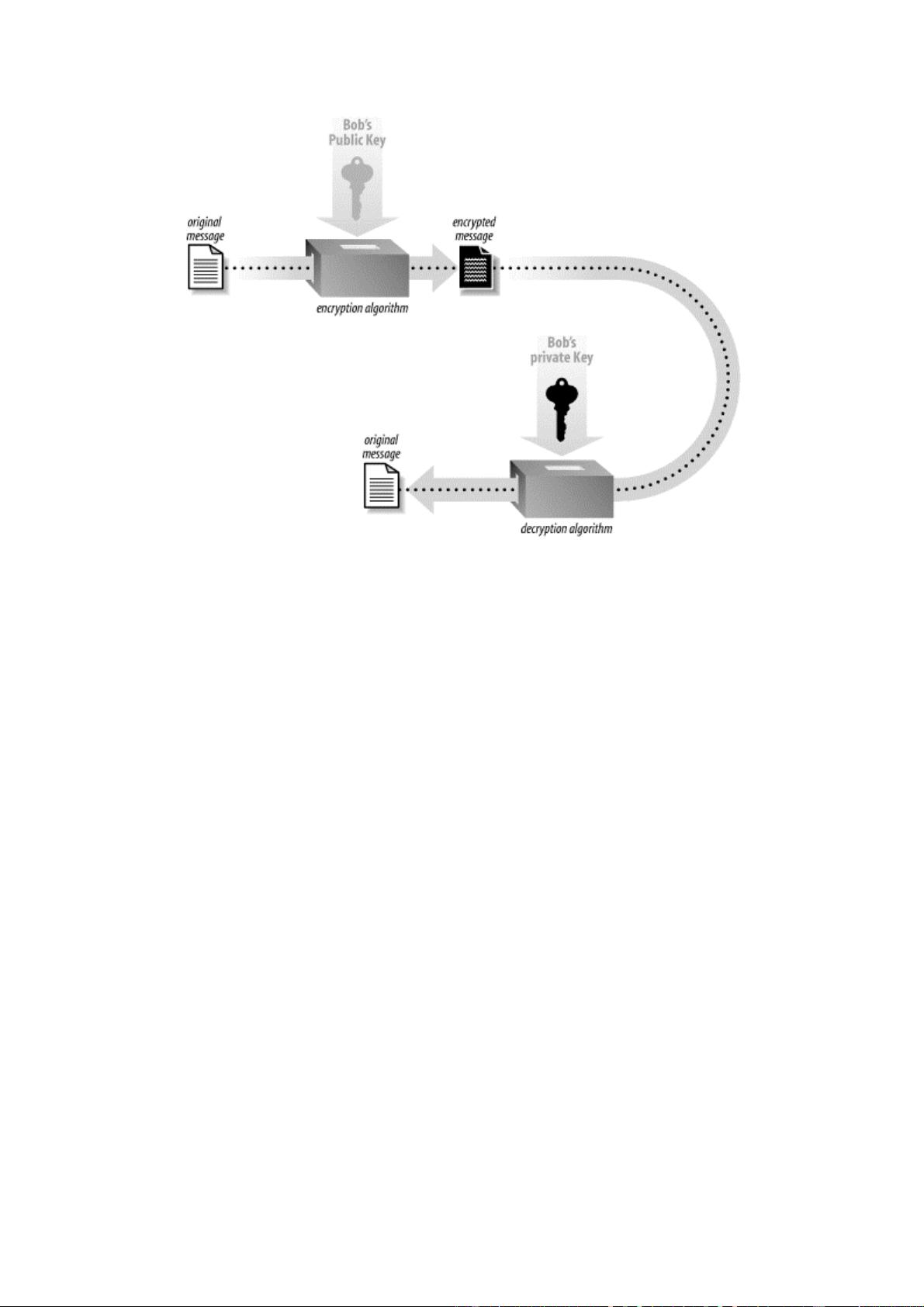
7
potentially need to stay protected for years, then you might want to go ahead and use 2,048-bit
keys.
When selecting key lengths for public key algorithms, you'll usually need to select symmetric key
lengths as well. Recommendations vary, but we recommend using 1,024-bit keys when you are
willing to work with symmetric keys that are less than 100 bits in length. If you're using 3DES or
128-bit keys, we recommend 2,048-bit public keys. If you are paranoid enough to be using 192-bit
keys or higher, we recommend using 4,096-bit public keys.
Requirements for key lengths change if you're using elliptic curve cryptography (ECC), which is a
modification of public key cryptography that can provide the same amount of security using faster
operations and smaller keys. OpenSSL currently doesn't support ECC, and there may be some
lingering patent issues for those who wish to use it. For developers interested in this topic, we
recommend the book Implementing Elliptic Curve Cryptography, by Michael Rosing (Manning).
1.1.2.3 Cryptographic hash functions and Message Authentication Codes
Cryptographic hash functions are essentially checksum algorithms with special properties. You
pass data to the hash function, and it outputs a fixed-size checksum, often called a message digest,
or simply digest for short. Passing identical data into the hash function twice will always yield
identical results. However, the result gives away no information about the data input to the
function. Additionally, it should be practically impossible to find two inputs that produce the same
message digest. Generally, when we discuss such functions, we are talking about one-way
functions. That is, it should not be possible to take the output and algorithmically reconstruct the
input under any circumstances. There are certainly reversible hash functions, but we do not
consider such things in the scope of this book.
For general-purpose usage, a minimally secure cryptographic hash algorithm should have a digest
twice as large as a minimally secure symmetric key algorithm. MD5 and SHA1 are the most
popular one-way cryptographic hash functions. MD5's digest length is only 128 bits, whereas
SHA1's is 160 bits. For some uses, MD5's key length is suitable, and for others, it is risky. To be
safe, we recommend using only cryptographic hash algorithms that yield 160-bit digests or larger,
unless you need to support legacy algorithms. In addition, MD5 is widely considered "nearly
broken" due to some cryptographic weaknesses in part of the algorithm. Therefore, we
recommend that you avoid using MD5 in any new applications.
Cryptographic hash functions have been put to many uses. They are frequently used as part of a
password storage solution. In such circumstances, logins are checked by running the hash function
over the password and some additional data, and checking it against a stored value. That way, the
server doesn't have to store the actual password, so a well-chosen password will be safe even if an
attacker manages to get a hold of the password database.
Another thing people like to do with cryptographic hashes is to release them alongside a software
release. For example, OpenSSL might be released alongside a MD5 checksum of the archive.
When you download the archive, you can also download the checksum. Then you can compute the
checksum over the archive and see if the computed checksum matches the downloaded checksum.
You might hope that if the two checksums match, then you securely downloaded the actual
released file, and did not get some modified version with a Trojan horse in it. Unfortunately, that
isn't the case, because there is no secret involved. An attacker can replace the archive with a
modified version, and replace the checksum with a valid value. This is possible because the
message digest algorithm is public, and there is no secret information input to it.
If you share a secret key with the software distributor, then the distributor could combine the
archive with the secret key to produce a message digest that an attacker shouldn't be able to forge,
since he wouldn't have the secret. Schemes for using keyed hashes, i.e., hashes involving a secret
key, are called Message Authentication Codes (MACs). MACs are often used to provide message