NXP Webinar: Secure-by-Design with OP-TEE in i.MX Processors
需积分: 5 106 浏览量
更新于2024-06-21
收藏 1.84MB PDF 举报
"Secure-by-Design-NXP-Webinar-Series-OP-TEE"
在现代智能设备中,安全性成为了不可或缺的一部分,特别是在物联网(IoT)领域。NXP的"Secure-by-Design"网络研讨会系列重点关注了如何在设计阶段就考虑并实现安全措施。其中,OP-TEE(Trusted Execution Environment)是一个关键的组件,它为基于i.MX处理器的系统提供了额外的安全层。
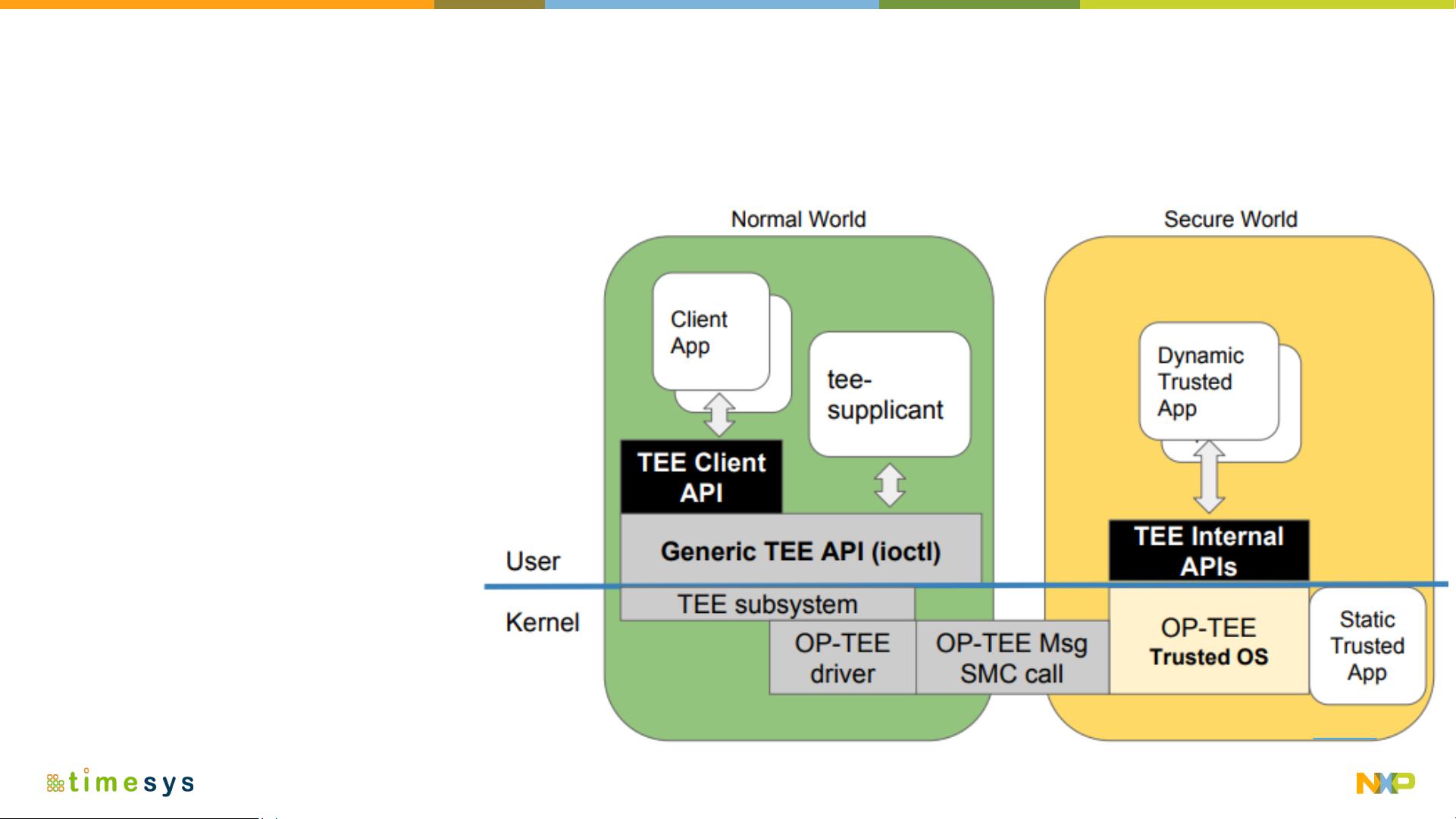
TEE(Trusted Execution Environment)是一个可信执行环境,其主要目的是在主操作系统(如Linux、Android等Rich Execution Environment, REE)之外提供一个隔离的空间,以保护敏感数据和代码的机密性和完整性。这是因为传统的REE可能存在安全漏洞,例如2019年Linux内核报告的265个漏洞。TEE通过硬件支持的机制,如Arm TrustZone,确保即使在REE被攻击的情况下,仍然能保证关键服务的安全运行。
Arm TrustZone是一种硬件级别的安全解决方案,它将系统划分为“安全”和“非安全”两个状态,对内存和I/O进行分区管理,以防止未经授权的访问。在简化硬件视图中,TrustZone会在 Arm SoC 上创建一个L2缓存,区分安全和非安全中断,以及安全和非安全的RAM、外设等。
OP-TEE是开源的TEE实现,特别针对NXP的i.MX处理器进行了优化。OP-TEE OS(Trusted OS)运行在TEE内,与REE并行,为REE上的应用提供可信服务。这些服务可以包括加密、数字签名、密钥管理等,这些操作都在TEE内执行,确保了关键安全操作的隔离和保护。
在OP-TEE中,内存保护机制确保了只有经过授权的组件才能访问特定的数据区域。此外, Trusted Applications (TA) 是在TEE内运行的特定应用程序,它们执行特定的安全功能,且与REE中的应用完全隔离。TA的执行和生命周期管理都受到严格控制,确保了它们的完整性和保密性。
网络研讨会的内容还涵盖了如何启用和测试OP-TEE,以及如何利用增强的OpenSSL引擎来加强安全性能。其他安全考虑因素可能包括固件更新的安全传输、防止调试攻击、以及对硬件后门和侧信道攻击的防护。
OP-TEE通过在硬件支持的隔离环境中提供可信服务,增强了基于NXP i.MX处理器系统的安全性,为物联网设备提供了更为可靠和安全的平台。开发者和系统集成商可以通过理解并应用这些技术,为他们的产品建立坚固的防御体系,抵御日益增长的网络安全威胁。
点击了解资源详情
点击了解资源详情
点击了解资源详情
2021-03-18 上传
2015-09-22 上传
2021-04-19 上传
2021-03-19 上传
2021-10-25 上传
2021-08-21 上传
TrustZone_Hcoco
- 粉丝: 2w+
- 资源: 32
最新资源
- 响应式鲜花全屏网站模板
- doubly_linked_list_lab
- huffmanandprufer:生成用于文件压缩的霍夫曼树并使用Prufner编码霍夫曼树
- phpProyect
- 控制5台电机顺启逆停PLC程序.rar
- SoftUni-CSharp-Entity-Framework-Core:实体框架核心作业和考试
- nwinters13.github.io:课程管家
- LINGO11.rar
- poc-sugar-monitor:血糖监测仪的POC
- SimpleFootie:简单的足球比赛引擎模拟-开源
- 信息104
- 电信设备-基于线性时序逻辑的移动机器人最优巡回路径设定方法.zip
- snailfwd-site-special:snailfwd 特殊项目模板
- 货梯PLC程序.rar
- phone-shop:“梨电话店”出售
- 乌托邦-RESTful:用PHP编写的Utopia Network RESTful API