16 CHAPTER 1. INTRODUCTION
during the same cycle. cipher inter thus takes as many cycles as cycle to be exe-
cuted, but computes two ciphertexts instead of one. Overall, encrypt blocks inter
is thus twice faster than encrypt blocks.
1.0.3 The Case for Usuba
Implementing high-throughput cryptographic primitives, or securing primitives against
side-channel attacks are complicated and tedious tasks. Both are hard to get right and
tend to obfuscate the code, thus hindering code maintenance. Trying to achieve both at
the same time, performance and side-channel protection, is a formidable task.
Instead, we propose Usuba [212, 211], a domain-specific programming language de-
signed to write symmetric cryptographic primitives. Usuba is a high-level program-
ming language, enjoying a straightforward formal semantics, allowing to easily reason
on program correctness. Usuba programs are constant-time by construction, and thus
protected against timing attacks. Furthermore, Usuba can automatically insert counter-
measures, such as Boolean masking, to protect against power-based side-channels. Fi-
nally, Usuba compiles to high-performance C code, exploiting SIMD extensions of mod-
ern CPUs when available (SSE, AVX, AVX512 on Intel), thus performing on par with
hand-tuned implementations.
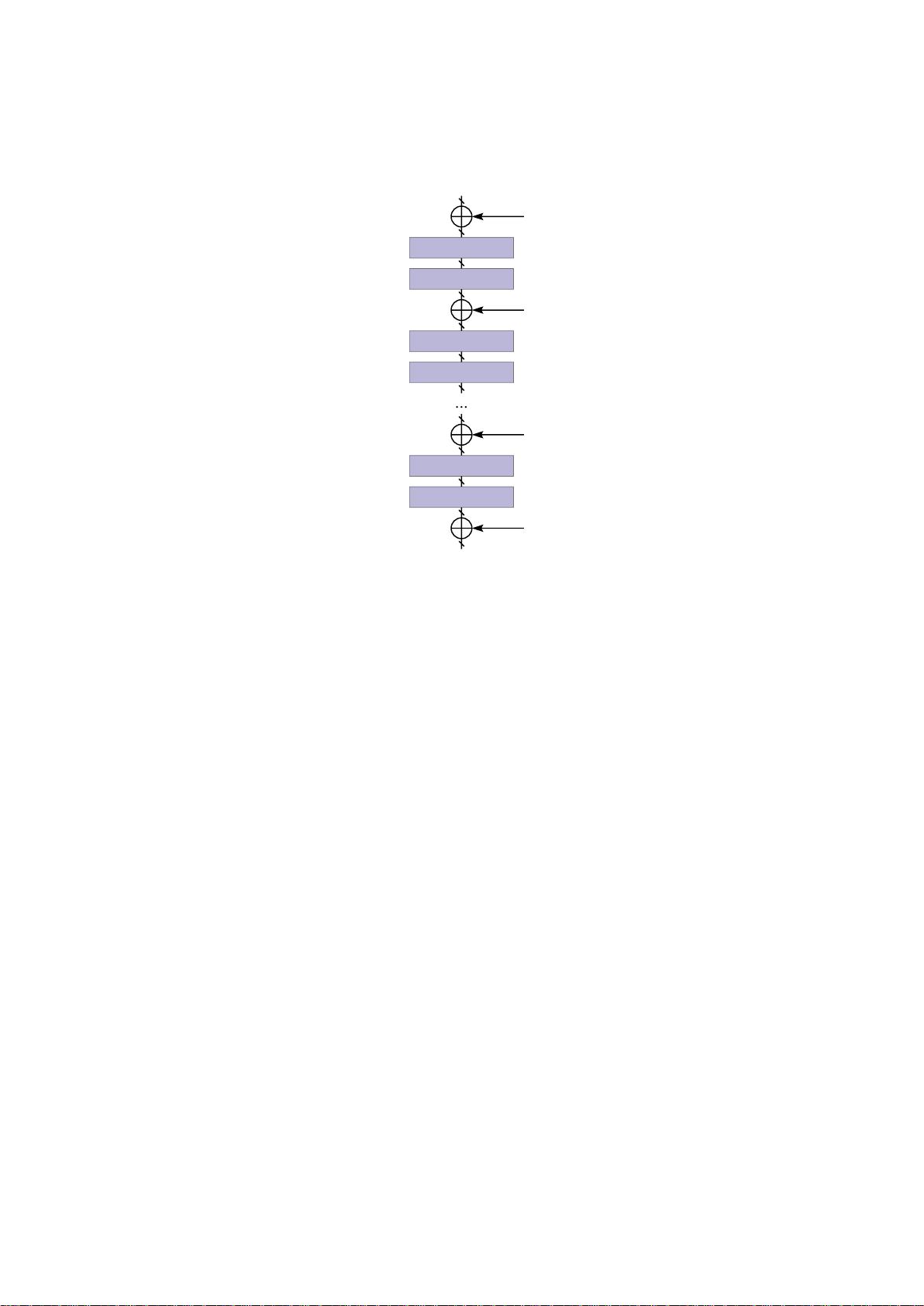
The design of Usuba is largely driven by the structure of block ciphers. A block
cipher typically uses bit-permutations, bitwise operations, and sometimes arithmetic op-
erations, and can therefore be seen as a stateless circuit. These basic operations are com-
bined to form a round, and a block cipher is defined as n (identical) rounds, each of them
taking the output of the previous round as well as a key as input. For instance, the
RECTANGLE [309] block cipher takes as input a 64-bit plaintext and 25 64-bit keys, and
produces the ciphertext through 24 rounds, each doing a xor, and calling two auxiliary
functions: SubColumn (a lookup table), and ShiftRows (a permutation). Figure 1.1a rep-
resents RECTANGLE using a circuit.
Usuba aims at providing a way to write an implementation of a cipher which is
as close to the specification (i.e., the circuit) as possible. As such, RECTANGLE can be
straightforwardly written in Usuba in just a few lines of code, as shown in Figure 1.1b.
The code should be self-explanatory: the main function Rectangle takes as input the
plaintext as a tuple of 4 16-bit elements, and the key as a 2D vector, and computes 25
rounds, each calling the functions ShiftRows, described as 3 left-rotations, and SubColumn,
which computes a lookup in a table. This code is simple, and as close to the specifica-
tion as can be. Yet, it compiles to a C code which is about 20% faster than the reference
implementation (Section 5.1), while being much simpler and more portable: whereas the
reference implementation explicitly uses SSE and AVX SIMD extensions, Usuba is not
bound to a specific SIMD extension.
One of the other main benefits of Usuba is that the code it generates is constant-time
by construction. To write constant-time code with traditional languages (e.g., C) is to fight
an uphill battle against compilers [27], which may silently rewrite one’s carefully crafted
program into one vulnerable to timing attacks, and against the underlying architecture
itself [216], whose undocumented, proprietary micro-architectural features may leak se-
crets through timing or otherwise. For instance, the assembly generated by Clang 9.0 for
the following C implementation of a multiplexer:
bool mux(bool x, bool y, bool z) {
return (x & y) | (˜x & z);
}
0
使用cmove指令,该指令不能保证是常量时间[259]。同样,一些整数乘法指令已知不是常量时间
,导致库出现问题