perform a broader analysis of potential safety implications and to
define and evaluate first countermeasures. In this section we
summarise the basic principles and results of these tests. While
some aspects of these tests have been described in more detail in
previous publications, some of them have been slightly extended
as a new contribution for this publication, also extended with a
systematic analysis of the incident, violated security aspects and
potential implications in the interplay with safety.
Each of the selected tests could be demonstrated on real,
recent automotive hardware. They could be verified in two
different technical setups, both containing a wiring harness and
different electronic control units (ECUs) from a recent model
(built in 2004 and 2005, respectively) of a big international car
producer. Cars of both series have a similar technical architecture
and use the CAN bus for the communication between the separate
devices. Supported by different bus interfaces, a PC system can be
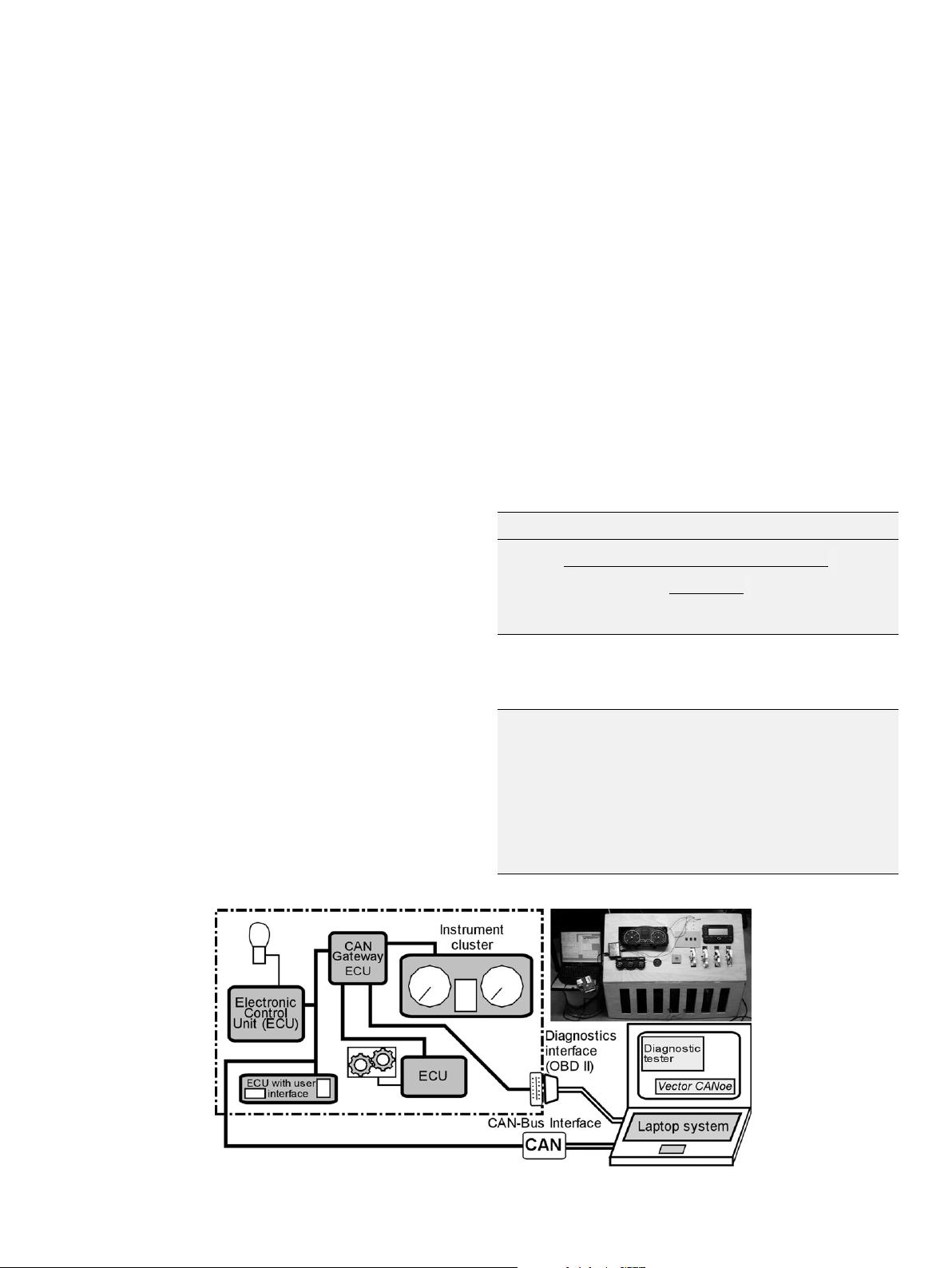
used to interact with or investigate the automotive system. Fig. 1
illustrates the basic concept of the technical setup.
In the following four subsections, the practical examples will be
presented and analysed in the following structure. First, the
implementation of the attack is explained and the results of the
attack are presented. Afterwards, a potential security incident that
could have employed the described attacking technique is discussed
by using the CERT taxonomy [6]. Table 1 shows its main structure.
Incidents are classified by identifying the kind of attackers,thetools
they used as well as the vulnerabilities they exploited. Elementary
actions and their targets are identified together with the unauthorised
results.Alsotheobjectives of the attacker are examined in order to
understand the underlying motivation. As the horizontal bars
indicate, the actual attack and events occurring in its context are
subordinate phases of the entire incident.
Following the CERT classification, each attack scenario is
analysed with respect to the violated security aspects and
potential implications, especially in the interplay with safety.
In this article we use the five central security aspects known from
IT security (confidentiality, integrity, availability, authenticity and
non-repudiation) to identify underlying weaknesses and to analyse
potential countermeasures. In the context of this section, the
violation of security aspects in the four attack scenarios S1–S4 has
been evaluated with a focus on the digital information commu-
nicated via the car’s internal bus networks (see Table 2).
3.1. Scenario S1: analyses on the electric window lift
The first potential attack target we investigated was the
electric window lift system. For early practical tests performed on
this scenario a simulation environment was used. This was a
simplified car environment being part of CANoe, an established
development and simulation software from Vector Informatik
[11] widely used in the automotive industry.
In this test, a few lines of malicious code have been added to an
arbitrary ECU attached to the simulated comfort CAN subnetwork.
Once a predefined condition is met (in this case when the car’s
speed exceeds 200 km/h) the code replays the CAN message
containing the flag for opening the driver window. Although the
real console still sends its messages in the same frequency
indicating that no button is currently pushed, the simulated
window opens and will not close again until the end of the attack.
Even if the driver has a fast reaction and pushes the ‘‘close’’ button
while the window is still opening, it blocks and remains stuck.
More details about this test can be found in [12] (as well as in [4]
and [13]).
Meanwhile, the completion of the aforementioned physical
test setups allowed us to demonstrate similar results on a real
window lifter (being part of the door control modules in our
practical test setup, see Fig. 2) during a student project. After
identifying the CAN messages relevant for triggering the window
Fig. 1. Illustration of the practical test environment of automotive hardware.
Table 1
Main structure of the CERT taxonomy [6].
Incident
Attack
Event
Attackers Tool Vulnerability Action Target Unauthorised
result
Objectives
Table 2
Security aspects mapped to information within automotive bus systems.
Confidentiality Is communicated information read by unauthorised
nodes?
Integrity Is there communicated information which is semantically
incorrect (and potentially processed by unaware nodes)?
Availability Is information, which is to be communicated, accessible
by all requiring nodes? Is an implemented service
applicable?
Authenticity Has the communicated information been created by an
authorised node (i.e. stems from the expected sender)?
Non-repudiation Can a node prove that it did or did not communicate
certain information?
T. Hoppe et al. / Reliability Engineering and System Safety 96 (2011) 11–25 13









