SEMI E4-0699 © SEMI 1980, 1999 4
3.3 Data Rate — The supported data rates on signal
pins shall be 9600, 4800, 2400, 1200, and 300 baud.
The same data rate shall apply for data sent to and from
the equipment. The data rate shall be controlled to
better than 0.5%. (See RS-269-B and RS-334.) Optional
rates of 19,200 and 150 baud may be supplied if
desired.
3.4 Physical Medium — The connection with the host
may involve any medium that provides the required RS-
232-C quality, signal levels and data rate at the equip-
ment connector. The quality of signal should be such
that the effective bit error rate is less than 1 × 10
-6
. This
rate can be achieved easily with hardwired systems.
The distance limits specified in RS-232-C apply only to
systems using the wiring technique described in RS-
232-C. Since any method may be used in SECS-I as
long as RS-232-C signals are supplied at the connector,
the distance and isolation is dependent upon the design
of the physical medium which is external to the SECS-I
standard. (See Related Information R1-2.)
4 Character Structure
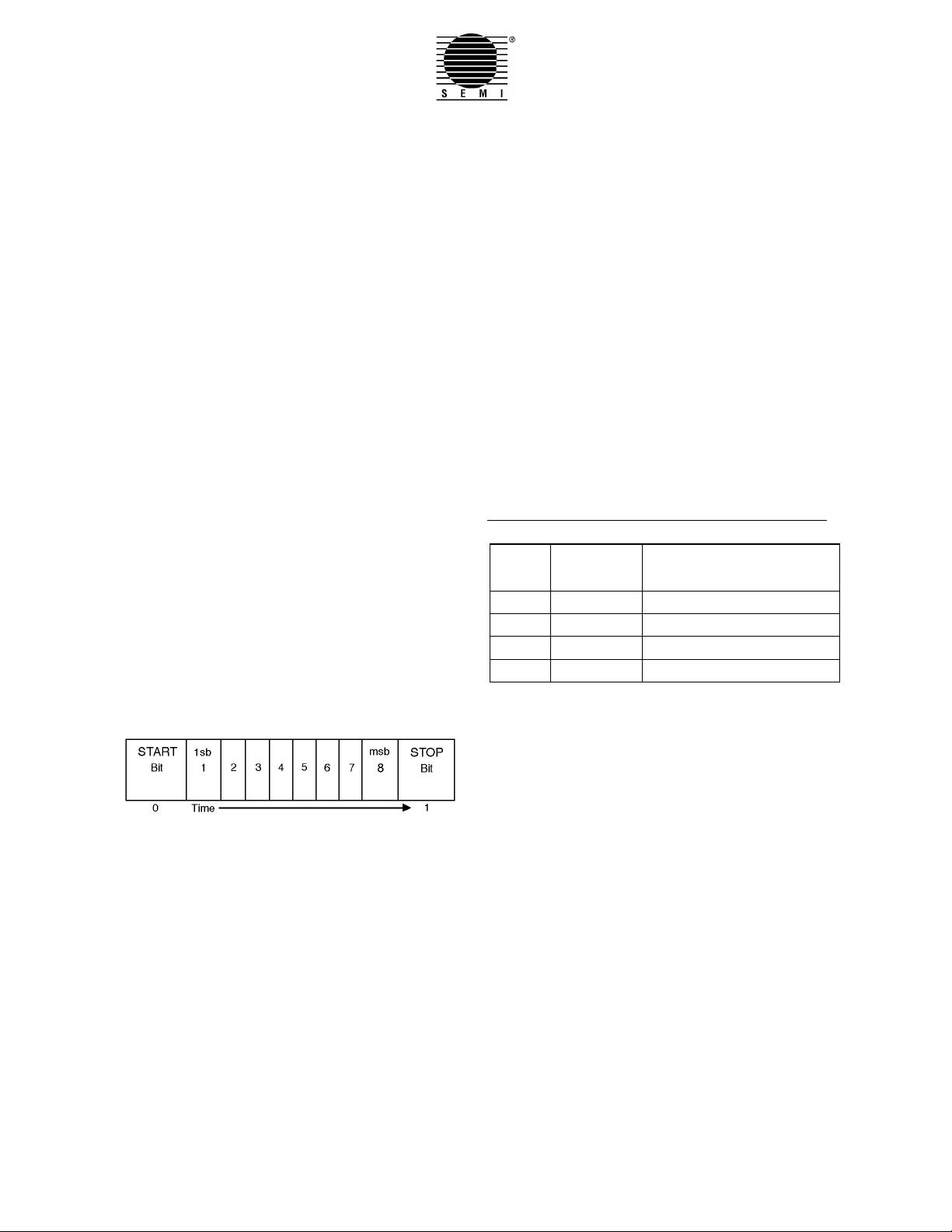
4.1 Characters — Data will be transmitted or received
in a serial bit stream of 10 bits per character at one of
the specified data rates. The standard character has one
start bit (0), 8 data bits and one stop bit (1). All bit
transmissions are of the same duration. The 8 data bits
are numbered from 1 to 8 in the order sent (see Figure
1). The timing between characters is asynchronous with
respect to the data rate. The 8 data bits may be any
arbitrary code. The eight data bits will hereafter be
referred to as a byte.
Figure 1
Character Structure
4.2 Weighted Codes — For bytes having weighted
codes, bit one is the least significant and bit eight is the
most significant. The most common weighted code is
binary.
4.3 Non-Weighted Codes — For codes without
numeric value such as ASCII, the bit numbers will be
used as the entry into a standard code table for
interpretation of the code. SECS-I performs no parity or
other verification of the contents of individual bytes.
5 Block Transfer Protocol
5.1 The procedure used by the serial line to establish
the direction of communication and provide the
environment for passing message blocks is called the
block transfer protocol. Most of the protocol is
accomplished with a handshake of single bytes. When
both ends of the line try to send at the same time, a
condition known as line contention exists. The protocol
resolves contention by forcing one end of the line,
designated as the slave (always the host), to postpone
its transmission and enter the receive mode.
Retransmission of blocks is used to correct
communication errors. The block transfer protocol is
shown in flow chart form in Figure 2, and described
below. Additional information is also contained in
Related Information R1-3 and R1-4.
5.2 Handshake Bytes — The four standard handshake
codes used in the block transfer protocol are shown in
Table 2. The three letter names, ENQ, EOT, ACK, and
NAK correspond to the ASCII code having the same
pattern.
Table 2 Handshake Codes
Name Codeb8
b7.........b1
Function
ENQ 00000101 Request to Send
EOT 00000100 Ready to Receive
ACK 00000110 Correct Reception
NAK 00010101 Incorrect Reception
5.3 Timeout Parameters — Timeouts are used to de-
tect communications failures. A timeout occurs when
the measured time between two events exceeds a pre-
determined limit. Generally, the length of time that
must pass before it can be assumed that an error has oc-
curred depends upon the particular systems involved.
The time required in one situation might be excessively
long in another. Thus, the timeout values must be
"tuned" to meet the application. In the block transfer
protocol, there are two situations requiring timeout val-
ues. The two timeout values are called parameters T1
and T2.
5.3.1 Inter-Character Timeout, T1 — The inter-
character timeout, T1, limits the time between receipt of
characters within a block after the length byte has been
received and until the receipt of the second checksum
byte.
5.3.2 Protocol Timeout, T2 — The protocol timeout,
T2, limits the time between sending ENQ and receiving
EOT, sending EOT and receiving the length byte, and
sending the second checksum byte and receiving any
character.









