3
M1
B
M2
U2U1
M1-U1
U1-B B-U2
U2-M2
M1-U1 U1-B
M1-U1 + U1-B
U1-B
U1-B + U2-M2
U2-M2
R.1
U.1
R.2
U.2
(a) (b)
TS1 TS2
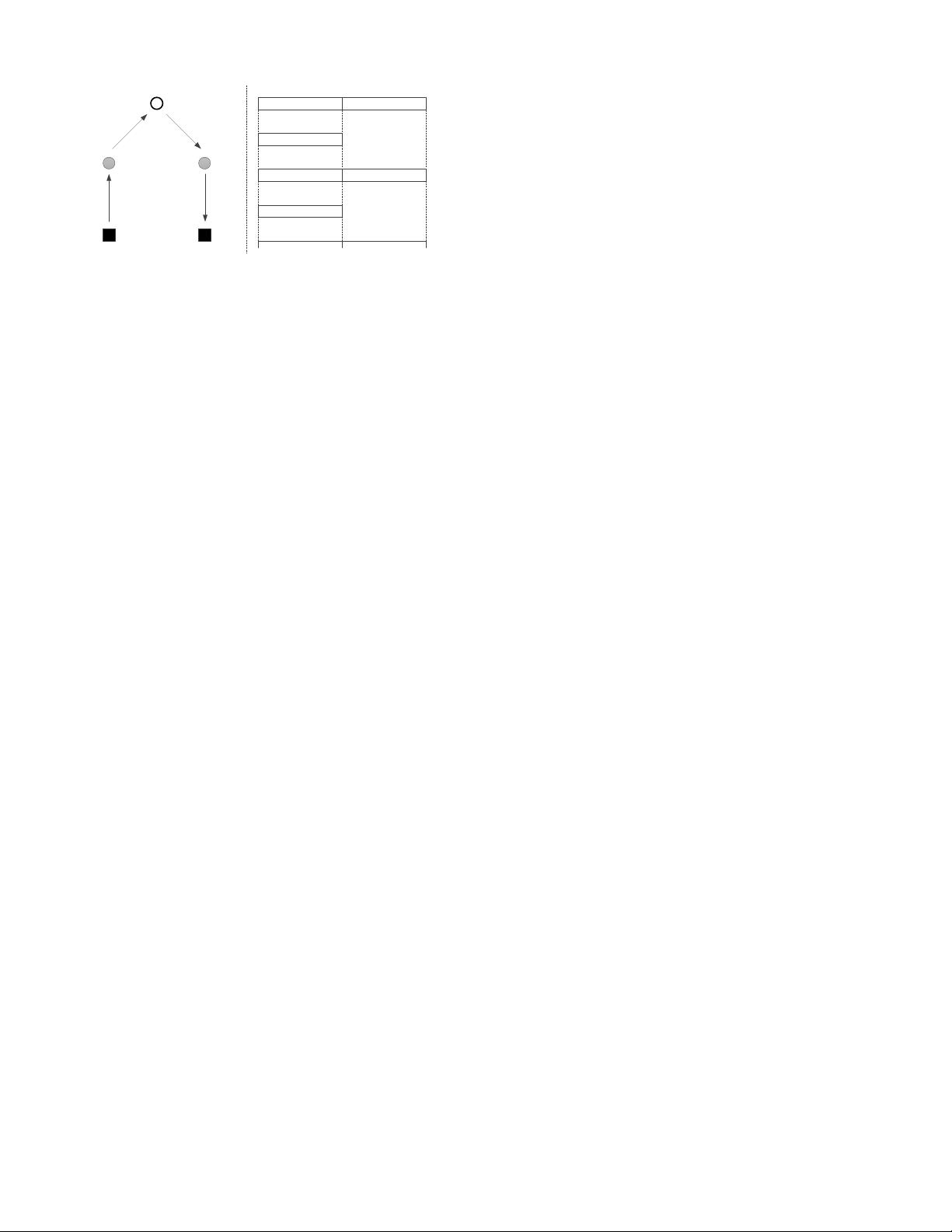
Fig. 2. System model. (a) the four possible information flows; (b) The
coupling and respective reference schemes duration in number of time slots.
III. SYSTEM MODEL
Figure 2(a) shows the network topology that captures the
quintessential example of the transmission schemes proposed
in this paper. The links will be denoted by X-Y, where it is
understood that X is the transmitter and Y is the receiver. All
nodes are half-duplex, i. e. a node cannot transmit and receive
at the same time. These network nodes are characterized as
follows:
• A Base Station (B) capable of adapting the transmission
rate and multipacket reception through Opportunistic
Interference Cancellation (OIC) [5];
• Two normal devices (U1 and U2) capable of adapting the
transmission rate and multipacket reception through OIC;
and
• Two MTDs M1, M2 with low complexity, unable to per-
form advanced processing, such as multipacket reception.
They use low power and a low, fixed rate R
M
.
The main ingredient of the proposed scheme is the underlay-
ing i. e. simultaneous activation of the links M1-U1 and B-U2.
Clearly, the underlaying would work regardless whether the
transmission B-U1 carries data for U1 only or it also contains
data that needs to be relayed over the link U2-M2 at a future
point. Another underlaying occurs between the links U1-B and
U2-M2. If the data sent from U2 is only relayed data that has
been previously received from B, then the signal transmitted by
U2 is completely known by B and can be canceled, such that B
can receive the transmission from U1 over a “clean channel”.
Such schemes have been treated in [44]–[49]. However, here
we leave the opportunity that U2 sends to M2 data that may
have originated at U2 or at another MTD connected to U2,
such that the signal sent by U2 cannot be assumed a priori
known by B. Therefore, B should try to decode the signal from
U2 if it needs to cancel this interference.
We propose a network-assisted underlaying solution that,
based on the collected Channel State Information (CSI) and
machine link outage requirements, selects the transmission
power and maximal rate of the transmitters at cellular links
U1-B and B-U2. The links M1-U1 and U2-M2 are where
the MTC occur. Any transmission to/from MTD is done over
a D2D link and at a fixed rate R
M
, with a requirement on
the maximal outage probability of P
Out
. On the other hand,
the links U1-B and B-U2 adapt the rate/power to the channel
conditions.
Fig. 2(b) shows the proposed underlayed transmissions and
the respective reference schemes, along with the required num-
ber of Time Slots (TS). The total duration in time slots of each
of these schemes is denoted as a scheduling epoch. In the ref-
erence schemes the underlaying of a link with another does not
take place. All the transmissions have normalized bandwidth
of 1 Hz, therefore the duration of a time slot can be measured
in terms of the number of symbols N . The analysis here is
done by considering that all communications are performed
using capacity-achieving Gaussian codebooks. Furthermore, at
most two simultaneous transmissions are considered over the
multiple access channel, the other transmissions are modeled
as noise. The receivers that apply OIC are aware of the
codebooks used by the transmitters. We note that for MTC,
the assumptions of sufficient large N and Gaussian codebooks
may not hold, since the MTC messages can be very short and
therefore finite block length theory should be used instead in
their characterization [50]. In that sense, the results shown in
this paper are optimistic, but the approach is valid and the
follow-up work can rely on the finite block length theory.
The underlaying (U.x) and respective reference schemes
(R.x) are differentiated as follows:
• (R.1): Due to the absence of underlaying, outage in the
link M1-U1 occur only due to deep fades that render R
M
undecodeable;
• (U.1): The link M1-U1 underlays B-U2. An outage can
occur both due to a deep fade on M1-U1 as well as due
to the interference from B’s transmission to U2. Device
U1 can use OIC to cancel out the interference from B-U2
and thus decode M1-U1;
• (R.2) - similar to (R.1), outage occurs only due to a deep
fade on U2-M2 and undecodeability of R
M
;
• (U.2) - the link U2-M2 underlays the link U1-B. An
outage can occur both due to deep fade on U2-M2 as well
as due to the interference from the transmission from U1
to B. The Base Station B can use OIC to cancel out the
interference from U2-M2 and afterward decode U1-B;
The rate/power applied on the links U1-B and B-U2 are
decided at the network infrastructure side; therefore the term
network-assisted. In this particular example, we consider that
the decision is made at B and communicated to the network
nodes using the appropriate signaling, but the details of it
are outside the scope of this work. Therefore B needs to
know the CSI of possibly all communication links. This
information can be available in the form of instantaneous CSI
or statistical/average CSI. Here we consider two different cases
regarding the CSI availability. Fig. 3(a) denotes full channel
state information (F-CSI), where B is aware of the instan-
taneous channel realizations for all links. Fig. 3(b) denotes
partial CSI (P-CSI), where B is aware of the instantaneous
realization of the channel for the links between B and U1 and
U2, while for each of the links between Mi-Ui, Mi-Uj, B it
knows the average SNRs
2
.
2
We note that the implementation of a signaling procedure that enables
F-CSI is expensive in terms of the required signaling overhead. Nevertheless,
we do consider it here as it provides a stepping stone to obtain the P-CSI
underlaying procedure.









