A Security Protocol for Mobile E-Service Oriented Architecture
(MSOA): Design and Implementation
Mingjun Xin, Zhangwei Huang and Quan Qian
School of Computer Science, Shanghai University, Shanghai 200072, China
{xinmj, velen,qqian}@shu.edu.cn
Abstract—In this paper, it first analyzes the present
security protocol for mobile communications.
Furthermore, a security framework for the mobile
E-Service is proposed. In the mean time, using the
inherent security and expansibility of J2ME, we design
a security message flow model to support
communication protocol for the Mobile E-Service
Oriented Architecture (MSOA), which emphasizes the
authentication and the security of information
transmission to the cooperative mobile users. Finally,
under the background application of county-level
mobile E-Service platform, we validate the security and
feasibility of the communication protocol, thus
providing firm and satisfactory technical support for
the county-level mobile E-Government system.
Keywords-Mobile E-Service; MSOA; security
communications protocol
I. INTRODUCTION
In recent years, with the integration of wireless
network with internet, the E-Service and applications
based on mobile terminals has been widely exploited,
thus much more attention has been pay on the security
for mobile communications than before[1]. As, on
one hand, people needs to secure the information both
for storage and transmission in order to effectively
resist the various internal and external attacks.
Including listening, interception, stealing, crack and
other passive attacks, moreover, alternation, forging,
destruction, fake, virus spreading and other initiative
attacks. On the other hand, the ability of processing
and storage for mobile terminals, was found to be
inferior to traditional computer terminals, thus, it is
difficult to apply the network security protocol to
mobile terminals, which is based on Internet.
At present, many communication protocols that
adopted by mobile E-Service platform, namely, do
not have the integrated ability to anti-replay or
anti-deny, which cannot guarantee confidentiality.
Moreover, for the complex communications process,
the system load is raised, while the efficiency is
reduced consequently. Based on the above
considerations, and combination with the related
business from county-level merchants, this paper
presents a secure communications protocol for mobile
E-Service oriented architecture based on J2ME
(JAVA2 Platform Micro Edition, J2ME), which
mainly serves for various business processing of the
county-level investment service department. The
above business includes all kinds of enterprise
management in industrial district, and the related
business oriented to enterprises to government,
individual to government, of course, also including
the internal departments of government [2].
II. A
SECURITY FRAMEWORK FOR MSOA
A. A security architecture for mobile E-Service
The Mobile E-Service Oriented Architecture
(MSOA) works as a transfer station, which connects
to the internal E-Service network, and receives all the
forthcoming released news. Then, it transfers the
information which is going to be released to mobile
terminal devices through E-Service server.
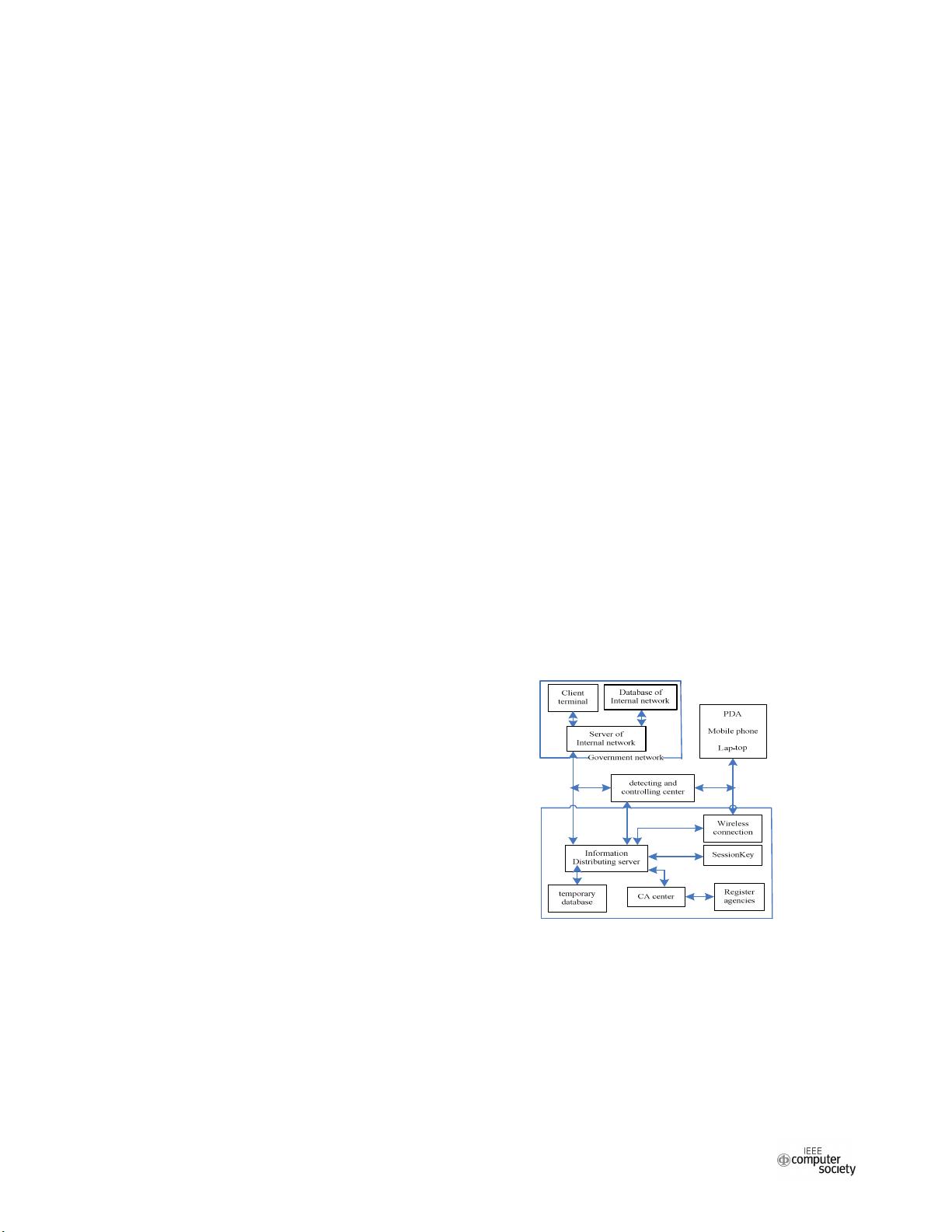
As shown in Figure 1, it constructs a security
architecture that supported MSOA, to make the
mobile information transmission service more secure,
using J2ME technology. The MSOA adopts the
wireless public key infrastructure (WPKI), of which
including the user's operating commission, visiting
state, information integration for mobile terminals and
the resistance towards network attacks[3].
Figure 1. A security framework for mobile E-service
This architecture sets up the user’s validation
gateway, the security monitoring of data transmission
among client terminals, the PDA mobile terminals
and the information distributing servers (IDS) through
deploying a detecting and controlling center. In
addition, the security strategy for wireless network
communications is mainly carried out by digital
certificates, symmetric encryption algorithms and
digital signatures. The CA certificate center will give
each user a digital certificate, which is used to identity
2009 International Conference on Networks Security, Wireless Communications and Trusted Computing
978-0-7695-3610-1/09 $25.00 © 2009 IEEE
DOI 10.1109/NSWCTC.2009.252
477
2009 International Conference on Networks Security, Wireless Communications and Trusted Computing
978-0-7695-3610-1/09 $25.00 © 2009 IEEE
DOI 10.1109/NSWCTC.2009.252
477









