1089-7798 (c) 2018 IEEE. Personal use is permitted, but republication/redistribution requires IEEE permission. See http://www.ieee.org/publications_standards/publications/rights/index.html for more information.
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change prior to final publication. Citation information: DOI 10.1109/LCOMM.2018.2820072, IEEE
Communications Letters
1
Thwarting Worm Spread in Heterogeneous Networks with
Diverse Variant Placement
Jianjian Ai, Zehua Guo and Hongchang Chen
Abstract—Many existing works assign diverse variants to
routing nodes in the network to prevent security threat (e.g.,
worm attack). However, the works assume that no common vul-
nerabilities among diverse variants, which is not always satisfied
in real world. In this paper, we consider that some variants have
common vulnerabilities and propose the common vulnerability-
aware diverse variant placement problem. We formulate the
problem as an integer programming optimization problem with
NP-hard complexity based on a new metric named Infected
Ratio Expectation (IRE). Furthermore, we devise algorithms
to solve the problem for the static network and the network
for extension. The simulation results show that compared with
baseline algorithms, our algorithms effectively restrain the worm
spread by about 42%.
Index Terms—Routing infrastructure, worm, diversity, simu-
lated annealing.
I. INTRODUCTION
In conventional networks, routing infrastructure exhibit high
homogeneity due to some practical consideration [1] (e.g., sim-
plifying network operation and maintenance, unifying operator
training, reducing complexity, and enhancing interoperability).
However, such a routing infrastructure could suffer from
serious security threats. For instance, an attacker can simply
send a router worm to compromise the entire network [2]. In
order to prevent worm propagation, research focus on mod-
eling worm propagation [3] and investigating the optimized
countermeasures based on the models [4].
Recently, diversity has been widely used in new scenarios
such as cloud computing security [5], Moving Target De-
fense (MTD) [6] and network routing [7]. Some research
have investigated the technique of diversity to prevent worm
propagation [8]. The existing solutions of the diverse variant
placement problem place heterogeneous variants on adjacent
nodes to achieve a good defense performance. The existing
works [1][8][9] assume no common vulnerabilities among
heterogeneous variants. However, the assumption is not al-
ways valid. The heterogeneous variants could have common
vulnerabilities since different router vendors could reuse the
same code (e.g., a third-party library containing vulnerabilities
[1]) in different devices. In this case, worms can continue
propagating even though the adjacent nodes are placed with
heterogeneous variants.
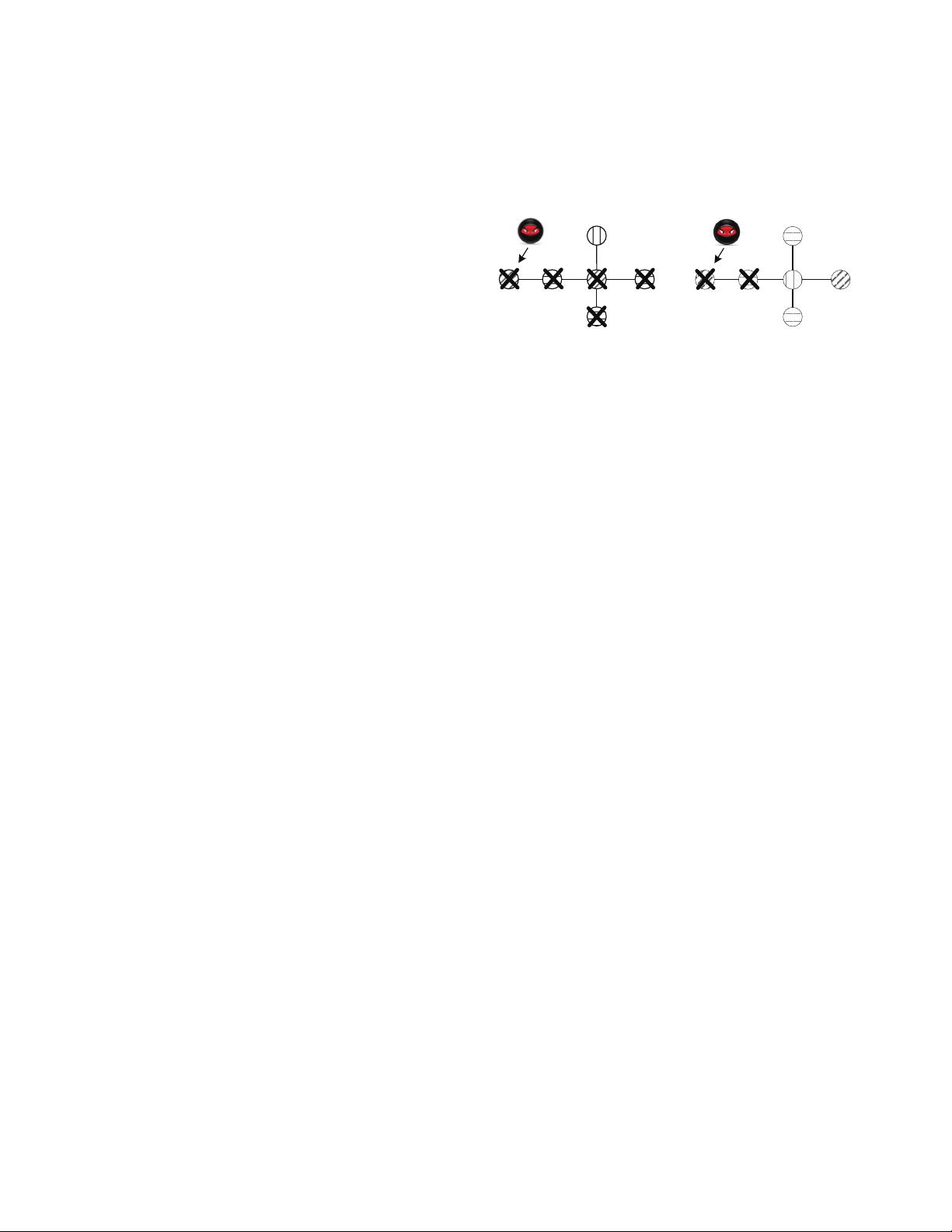
We exemplify this problem using Fig. 1, a simple network
with 6 nodes and 3 different variants. In the figure, the initial
injected node is node 1, and variants A and B have common
Manuscript received ***; revised *** and accepted ***. This work was
supported by Foundation for Innovative Research Groups of the National
Natural Science Foundation of China (61521003), National Key Research
and Development Plan (2016YFB0800101) and National Natural Science
Foundation of China (61602509). Jianjian Ai and Hongchang Chen are
with National Digital Switching System Engineering & Technology Research
Center, Zhengzou, Henan, China. Zehua Guo is with University of Minnesota
Twin Cities, Minneapolis, MN, USA. Zehua Guo is the corresponding author
(guolizihao@hotmail.com).
(a) The placement of Variant Flipping
(b) The placement considering com-
mon vulnerabilities among variants
Fig. 1. Worm spread under different diverse variant placement algorithms. A
circle denotes a node, a circle with a cross indicates an infected node, and
circles with different filling patterns indicate nodes with different variants.
Left slash indicates variant A, horizontal line indicates variant B and vertical
line indicates variant C.
vulnerabilities. Fig. 1(a) shows the result of an existing diverse
variant placement−Variant Flipping [9]: variant A is assigned
to nodes 1 and 3, variant B is assigned to nodes 2, 4 and 5, and
variant C is assigned to node 6. Since Variant Flipping does
not consider common vulnerabilities among variants, a worm
can contaminate nodes 1-5 under such a placement. Fig. 1(b)
shows the result of a common vulnerability-aware solution:
variant A is assigned to nodes 1 and 4, variant B is assigned
to nodes 2, 5 and 6, and variant C is assigned to node 3. Under
this placement, the worm only contaminates nodes 1 and 2.
Thus, the common vulnerability-aware solution achieves better
performance in terms of thwarting worm spread.
In this paper, we devise a common vulnerability-aware
solution that effectively places diverse variants to routing
nodes to restrain worm spread. First, we devise a metric named
Infected Ratio Expectation (IRE) to quantitatively measure the
impact of worm spread on the network. Then, we formulate
the common vulnerability-aware diverse variant placement
problem as an integer programming optimization problem
using the proposed IRE. Due to the problem complexity of NP-
hardness, we devise a simulating annealing-based algorithm to
solve the problem. We also consider the case that the network
could add extra routing nodes to improve its processing ability
and propose a local network topology-based algorithm to
achieve the tradeoff between the defense performance and
the placement cost. The simulation results show that the
proposed algorithms can effectively restrain worm spread with
a reasonable placement cost.
II. SOLUTION OVERVIEW
Fig. 2 shows the workflow of our proposed solution. In step
1, we periodically obtain network information from the routing
infrastructure and measure IRE based on the network informa-
tion. In step 2, we formulate the common vulnerability-aware
diverse variant placement problem as an integer programming
problem using the IRE and the network information. In step
3, we solve the problem for two different scenarios. If the









