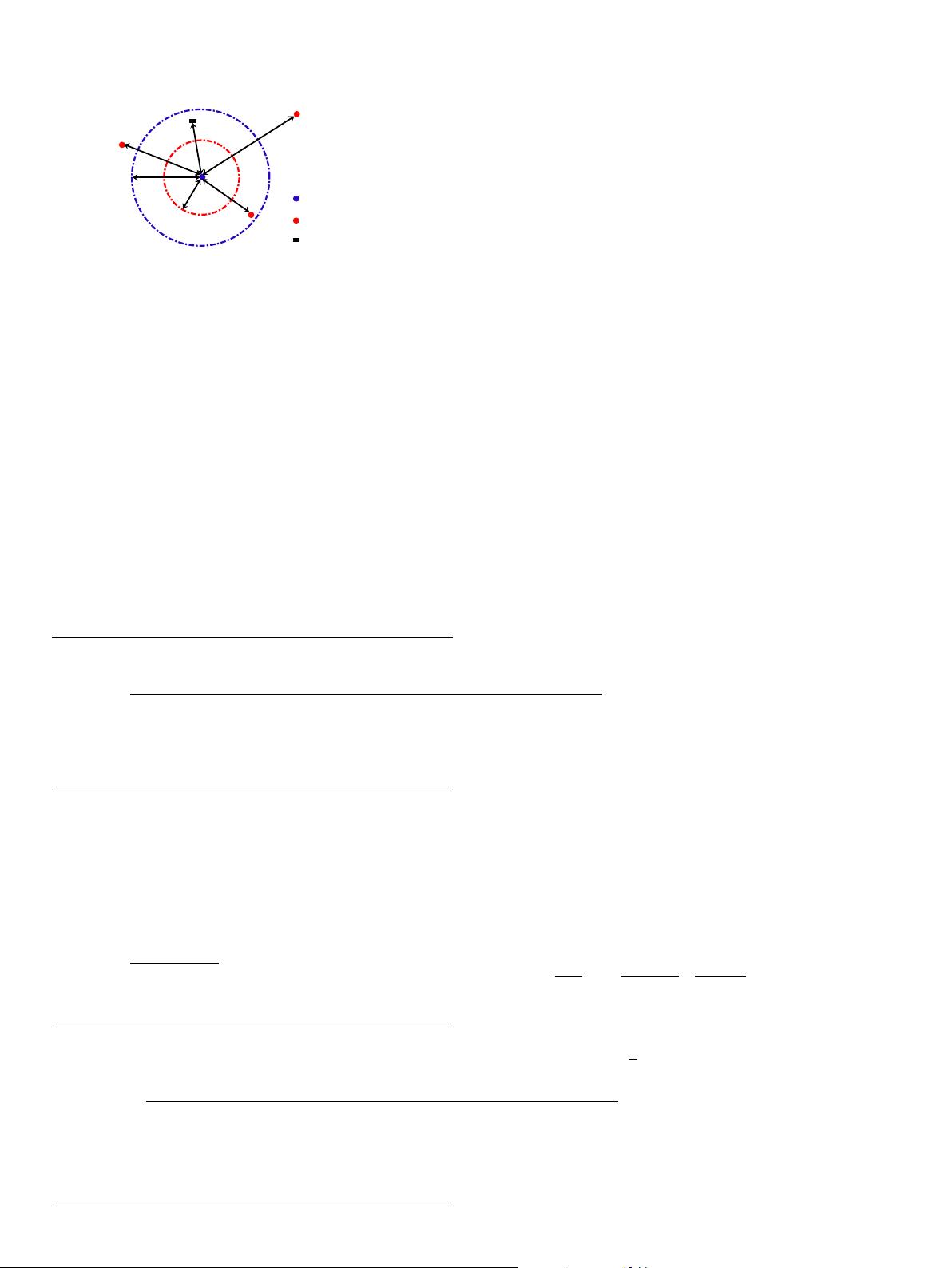
tag identification means that r
max,i
is larger than the distance x be-
tween the desired reader R
i
and the target tag T. On the other hand,
the effective interrogation radius of R
i
decreases to r
i
(marked as a
red dashed-line circle) seriously due to the interferences from the
other N
Reader
1 interfering readers operating at the same time. In
this case, the total interference signal from other readers is so strong
as to make the interrogation radius r
i
smaller than x; hence, R
i
cannot
detect this target tag successfully. Therefore, only those tags satisfy-
ing x 6 r
i
can be identified by the desired reader R
i
.
3. RFID reader-to-reader anti-collision model
For the reader-to-reader collision problem described in Fig. 1,
our research motivation is to firstly establish a comprehensive
scheduling-based model for readers with respect to frequency
channels, time slots, power and physical locations, and then find
an effective computational method to solve this model.
Let’s assume that N
Reader
readers are deployed in the rectangular
working space (WS) with the length of L
1
and the width of L
2
and
(x
i
, y
i
) denotes the location of the ith reader R
i
. There are N
Freq
fre-
quency channels and N
Slot
time slots available for these readers.
Each reader has the maximum transmitting power of P
max
. As far
as this multiple-reader scenario to be concerned, R
i
can communi-
cate with and identify the target tag T at the kth time slot success-
fully only if the signal-to-interference-plus-noise ratio (SINR
i
)ofR
i
is greater than a desired minimum value SINR
min
. That is to say,
SINR
i
(k, x) must satisfy the following formula
SINR
i
ðk; xÞ¼
BP
i
ðk; xÞ
I
i
ðk; xÞþNoise
i
P SINR
min
; ð1Þ
where x is the distance between R
i
and the target tag T, BP
i
(k, x)is
the backscatter signal power received by R
i
, I
i
(k, x) is the total inter-
ference power from the other N
Reader
1 readers operating at the
kth time slot simultaneously and Noise
i
is the noise power of R
i
.In
Physics, BP
i
(k, x) can be defined as
BP
i
ðk; xÞ¼
a
b
x
E
tag
P
i
ðkÞG
T
G
R
ðP
0
x
c
Þ
2
: ð2Þ
where,
a
b
x
is the normalized spectrum power, E
tag
is the effective
power reflection coefficient, P
i
(k) is the signal power of R
i
at the
kth time slot, G
T
and G
R
is the transmitting antenna gain and the
receiving antenna gain, respectively, P
0
is the reference path loss
at the distance of 1 m and
c
is the path-loss exponent. On the other
hand, the total interference power I
i
(k, x) can be determined by
I
i
ðk;xÞ¼
X
N
Reader
j¼1;j–i
x
j
ðkÞI
j;i
ðkÞd
j;i
¼
X
N
Reader
j¼1;j–i
hP
j
ðkÞG
T
G
R
x
j
ðkÞb
mask
ð
D
CH
j:i
ÞP
0
d
c
j;i
;
and
D
CH
j:i
¼jCH
i
ðkÞCH
j
ðkÞj:
ð3Þ
where,
x
j
(k) is a two-valued variable (i.e.,
x
j
(k) = 1 means that R
j
operates at the kth time slot while
x
j
(k) = 0 means no operation),
h is the fading coefficient, P
j
(k) is the signal power of R
j
at the kth
time slot, and b
mask
() is the spectrum-mask level which is a func-
tion of the frequency separation between two readers. Known from
the propagation path of radio signals, the distance d
j,i
between R
i
and R
j
can be measured by Euclidean distance as
d
j;i
¼
ffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffi
ðx
i
x
j
Þ
2
þðy
i
y
j
Þ
2
q
; s:t: 0 6 x
i
; x
j
6 L
1
; 0 6 y
i
; y
j
6 L
2
:
ð4Þ
By integrating Eqs. (1)–(4), SINR
i
(k, x) can be completely formulated
as
Suppose that r
i
(k) is the effective interrogation radius of R
i
at the kth
time slot, which can be solved by
r
i
ðkÞ¼arg max
x
SINR
i
ðk; xÞ P SINR
min
: ð6Þ
However, the effective interrogation radius of R
i
cannot be greater
than its maximum interrogation radius r
max,i
(k)
r
max;i
ðkÞ¼
k
i
ðkÞ
4
p
ffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffi
P
i
ðkÞG
T
G
R
P
min
1 m
4
ð1 þ mÞ
2
s
; ð7Þ
R
i
(x
i
,y
i
)
R
2
(x
2
,y
2
)
R
j
(x
j
,y
j
)
R
1
(x
1
,y
1
)
T
d
j,i
r
max,i
r
i
x
d
2,i
d
1,i
Interfering reader
Desired reader
Target tag
Fig. 1. Reader-to-reader collision problem with multiple readers.
r
i
ðkÞ¼min
a
b
x
E
tag
P
i
ðkÞG
T
G
R
ðP
0
x
c
Þ
2
hG
T
G
R
X
N
Reader
j¼1;j–i
x
j
ðkÞP
j
ðkÞb
mask
ðjCH
i
ðkÞCH
j
ðkÞjÞP
0
ððx
i
x
j
Þ
2
þðy
i
y
j
Þ
2
Þ
c
þ Noise
i
0
B
B
B
B
B
@
1
C
C
C
C
C
A
1
2
c
; r
i: max
ðkÞ
0
B
B
B
B
B
B
@
1
C
C
C
C
C
C
A
;
s:t:
8i 2 NR; 8k 2 NS; CH
i
ðkÞ2CH; P
i
ðkÞ2½0; P
max
; ðx
i
; y
i
Þ; ðx
j
; y
j
Þ2WS; ð8Þ
SINR
i
ðk; xÞ¼
a
b
x
E
tag
P
i
ðkÞG
T
G
R
ðP
0
x
c
Þ
2
hG
T
G
R
X
N
Reader
j¼1;j–i
x
j
ðkÞP
j
ðkÞb
mask
ðjCH
i
ðkÞCH
j
ðkÞjÞP
0
ððx
i
x
j
Þ
2
þðy
i
y
j
Þ
2
Þ
c
þ Noise
i
;
s:t:
8i 2 NR; 8k 2 NS; CH
i
ðkÞ2CH; P
i
ðkÞ2½0; P
max
; 0 6 x
i
; x
j
6 L
1
; 0 6 y
i
; y
j
6 L
2
: ð5Þ
4800 Z. Li et al. / Expert Systems with Applications 41 (2014) 4798–4810









