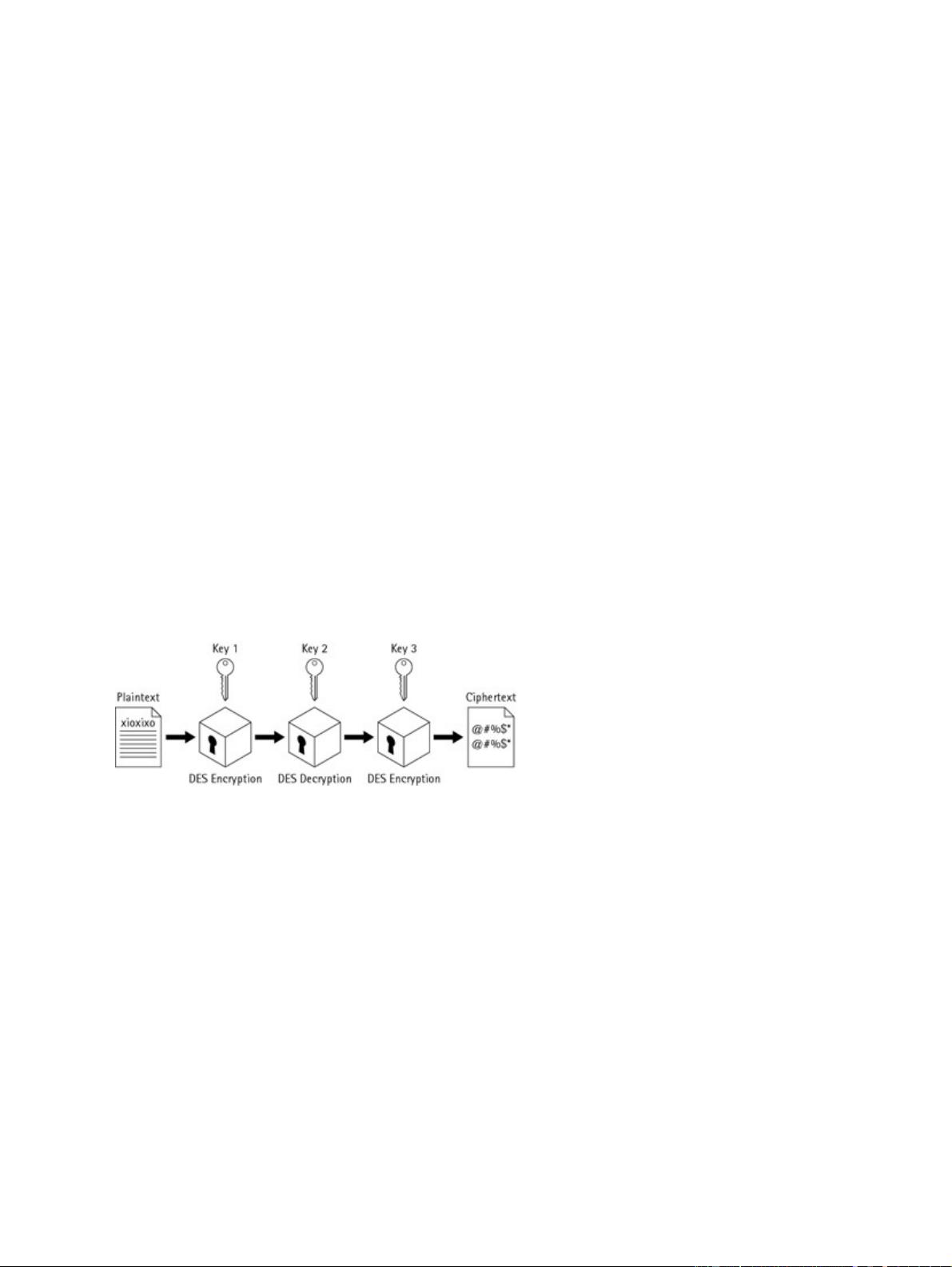
Note Refer to RFCs 1827 and 2144 for more information on DES.
DES is still surrounded by controversy. This controversy was originally fueled by the following facts:
The key length used by this algorithm was reduced to 56 bits by the U.S. government, although the
original design called for a key length of 128 bits, leading to a compromise on security. Although the
algorithm for DES was published, the rationale for the design was never published.
•
DES became widely available to the U.S. public and to approved users in other countries. However,
DES was excluded by the U.S. government from protection of any of its own classified information.
•
The major weaknesses and attacks that are faced by DES are described below.
Brute Force Attack The simplest attack to decipher a DES key is the brute force attack. The brute force
attack on the DES algorithm is feasible because of the relatively small key length (56 bit) and ever−increasing
computational power of the computers. Until the mid−1990s, brute force attacks were beyond the capabilities
of hackers because the cost of computers that were capable of hacking was extremely high and unaffordable.
With the tremendous advancement in the field of computing, high−performance computers are relatively
cheaper and, therefore, affordable. In fact, general purpose PCs today can be successfully used for brute force
attacks. Many hackers today are using more powerful techniques, such as Field Programmable Gate Array
(FPGA) and Application−Specific Integrated Circuits (ASIC) technology that provide faster and cheaper
means of hacking.
You can break through any cipher by trying all keys that possibly exist. However, in brute force attacks, the
time taken to break a cipher is directly proportional to the length of the key. In a brute force attack, keys are
randomly generated and applied to the ciphertext until the legitimate key is generated. This key decrypts the
data into its original form. Therefore, the encryption key length is a major factor that needs to be considered
while choosing a key. The longer the encryption keys, the stronger the security. For example, in case of a
32−bit long key, the number of steps required to break the cipher are about 2
32
or 10
9
. Similarly, a 40−bit key
requires about 2
40
steps. This is something which can be achieved in one week by anyone sitting on his
personal computer. A 56−bit key is known to have been broken by professionals and governments by using
special hardware in a few months time. Today, 128−bit encryption is considered to be the safest and most
reliable means of encrypting messages.
Note On January 19, 1999, a group of computer enthusiasts from all over the world formed a coalition to
decipher a DES encrypted ciphertext and as a result recovered the key in a record−breaking time of 22
hours and 15 minutes. This coalition was known as Distributed.Net. Its members worked with DES
Cracker and a worldwide network of nearly 100,000 PCs on the Internet to recover the key. The DES
Cracker machine was specially designed for this purpose.
Note For more information on brute force attacks, refer to RFCs 2228 and 2557.
Differential Cryptanalysis Attack The differential cryptanalysis attack looks specifically at pairs of
ciphertexts whose plaintext have some specific differences. It analyzes these differences as the plaintext
propagates through the various rounds of DES when they are encrypted with the same key.
This technique chooses pairs of plaintext with a fixed difference. Two plaintexts can be chosen at random, as
long as they satisfy specific difference conditions. Then, using the differences in the resulting ciphertexts,
different probabilities can be assigned to different keys. As more and more ciphertext pairs are analyzed, one
key emerges, as the most probable candidate key.
Note For more information on differential cryptanalysis attack, refer to RFC 2144.
The Basics of Cryptography
14