NIST SP800-46:远程办公与宽带通信安全指南
需积分: 9 70 浏览量
更新于2024-07-16
收藏 3.69MB PDF 举报
NIST SP800-46《远程工作与宽带通信安全指南》是由美国国家标准与技术研究院(National Institute of Standards and Technology, NIST)发布的特别出版物,主要目的是为远程工作的用户、系统管理员和管理层提供关于宽带通信安全和政策、家庭办公室系统安全以及中央办公室系统管理员考虑因素的初步信息。这份文档旨在帮助理解如何选择、部署和管理远程工作用户的宽带通信,而不旨在强制实施严格的远程或家庭办公环境的通信框架,而是提出针对该领域的建议性措施。
首先,它涵盖了以下几个核心知识点:
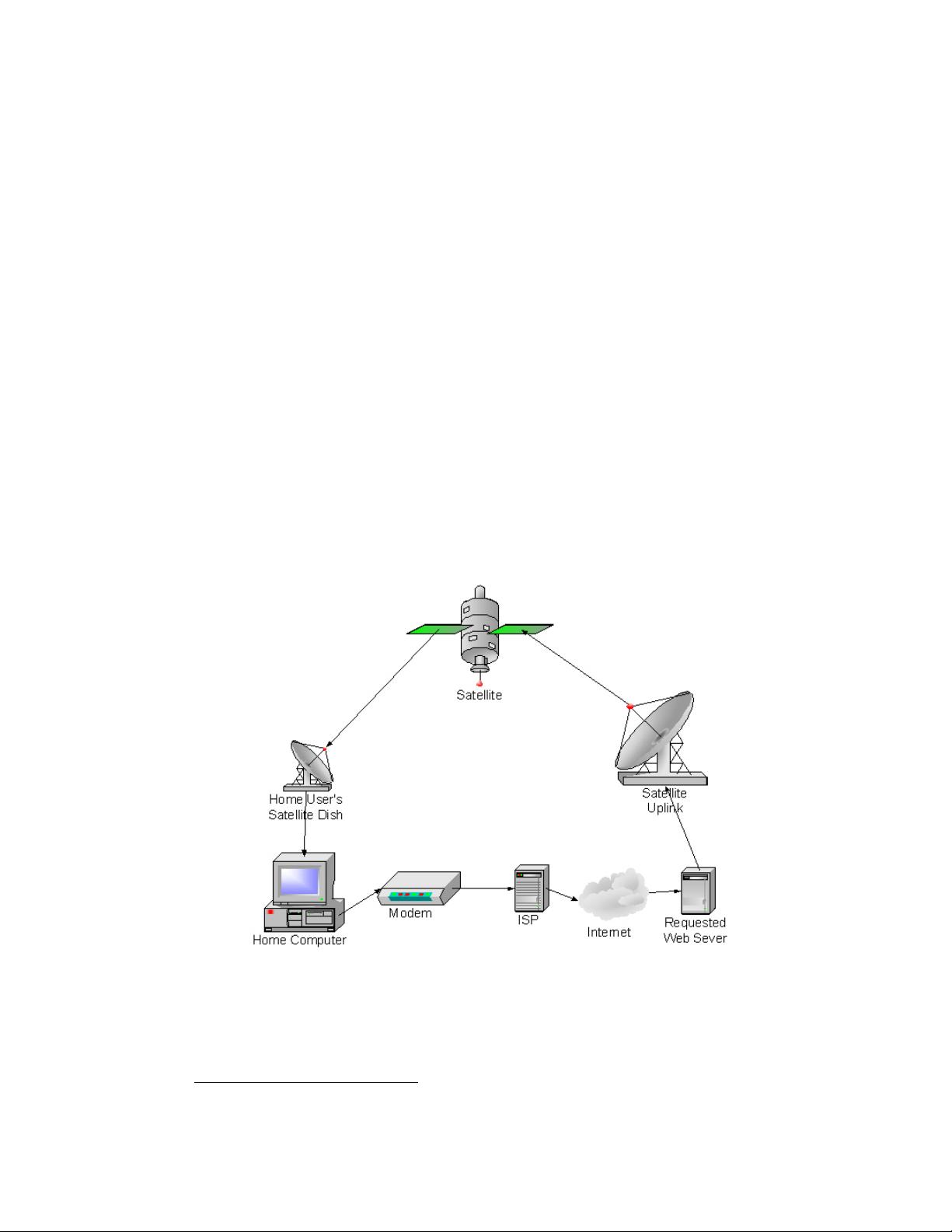
1. **远程工作安全**:文档强调了对于远程工作者,尤其是通过互联网进行通信时,如何确保数据隐私、身份验证和访问控制的重要性。它提倡实施强密码策略、使用加密技术和安全软件,以防止未经授权的访问和信息泄露。
2. **宽带通信政策**:提供了关于制定适应远程工作的宽带通信政策的指导,包括网络使用规定、设备管理和网络安全培训,以确保组织内的信息安全标准一致性。
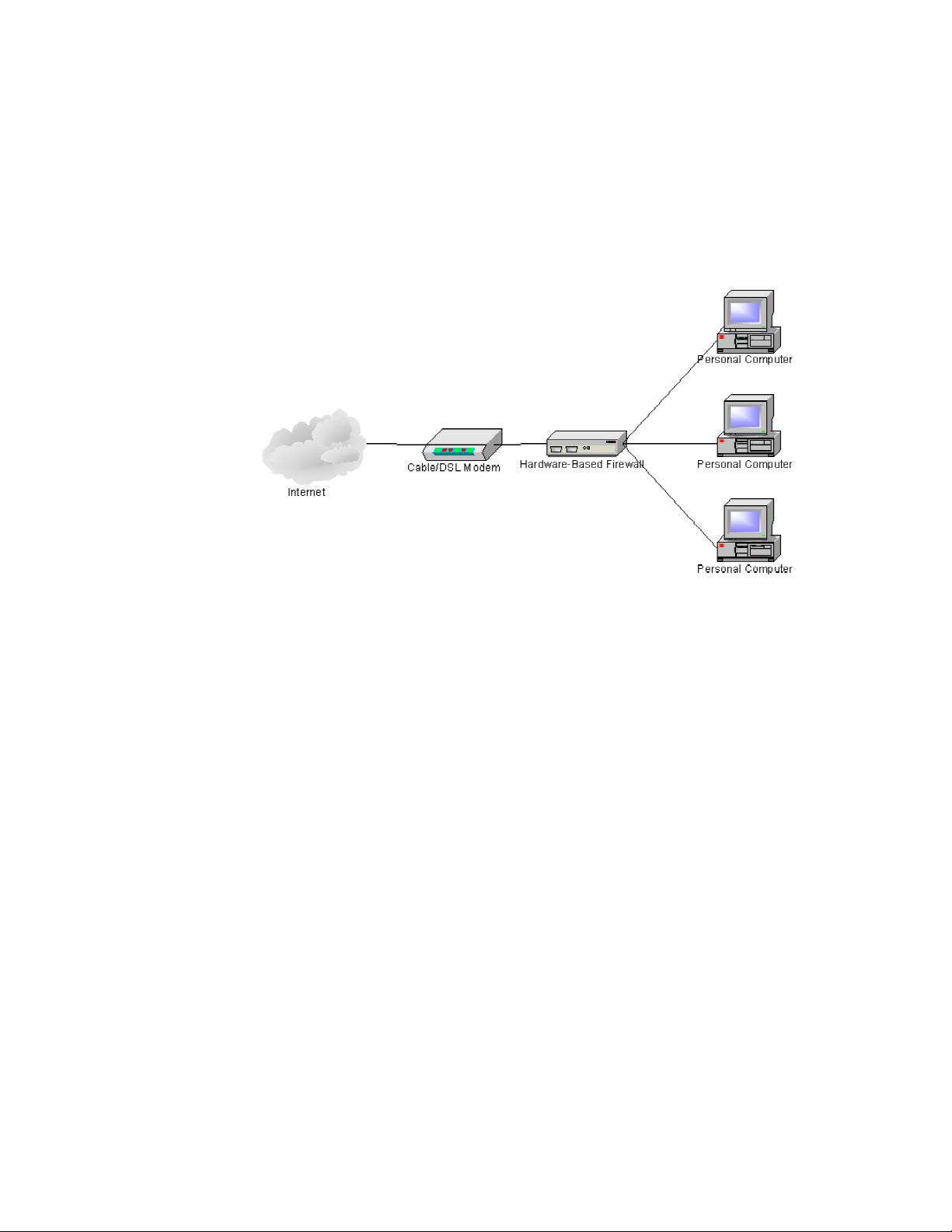
3. **家庭办公室系统安全**:着重讨论了家庭办公环境下的网络安全问题,如物理安全(如防火墙和防病毒保护)、设备隔离、以及网络连接设备的安全配置。
4. **系统管理员的角色**:明确了中央办公室系统管理员在远程工作环境中应如何监控和维护网络安全性,包括定期更新、故障排查和应急响应策略。
5. **技术参考和测试**:NIST SP800-46还引用了相关的技术测试和方法,以便管理员和技术人员评估和优化远程工作的网络安全性能。
6. **国家技术基础设施支持**:文档背景中提到,NIST的信息技术实验室(ITL)通过提供测量和标准基础设施的技术领导力,推动美国经济和公共福利的发展。
NIST SP800-46是一份实用性很强的文档,它结合了理论与实践,为远程工作环境中的信息安全提供了实用指导,帮助组织和个人有效地应对日益增长的远程办公趋势带来的安全挑战。阅读这份报告,不仅有助于提升远程工作环境下的网络安全意识,还能确保数据传输过程中的合规性和有效性。
117 浏览量
300 浏览量
174 浏览量
2020-02-18 上传
312 浏览量
2020-02-13 上传
2020-02-28 上传
2020-02-18 上传
143 浏览量
艾米的爸爸
- 粉丝: 800
- 资源: 314
最新资源
- ZPM:基于premake5的C ++软件包管理器
- hymenoptera_data.zip
- 经销商管理——经销商如何在厂商交易中立于不败之地
- kafka-stream-money-deserialization:一个用于研究Spring Kafka Streams的序列化反序列化问题的演示项目
- 初级java笔试题-my-study-tracking-list:我的学习跟踪列表
- gRPC节点:使用Node JS的gRPC演示
- google_maps_webservice
- 白酒高端产品选择经销商的误区
- git-count:计算您的提交
- 初级java笔试题-interview-prep-guide:面试准备指南
- Keil 软件最新版.rar
- wasm-udf-example
- 初级java笔试题-code-tasks:从@jwasham克隆-我的学习仪表板
- 红色状态::chart_increasing:齿轮创建者的正常运行时间监控器和状态页面,由@upptime提供支持
- vue-monoplasty-slide-verify:Vue幻灯片验证在线预览
- JDK8版本jdk-8u202-linux-arm32-vfp-hflt.tar(gz).zip