没有合适的资源?快使用搜索试试~ 我知道了~
首页cisco nexus7K qinq配置
资源详情
资源评论
资源推荐

CHAPTER
Send document comments to nexus7k-docfeedback@cisco.com
9-1
Cisco Nexus 7000 Series NX-OS Interfaces Configuration Guide, Release 5.x
OL-23435-03
9
Configuring Q-in-Q VLAN Tunnels
This chapter describes how to configure IEEE 802.1Q-in-Q (Q-in-Q) VLAN tunnels and Layer 2
protocol tunneling on Cisco NX-OS devices.
This chapter includes the following sections:
• Information About Q-in-Q Tunnels, page 9-1
• Information About Layer 2 Protocol Tunneling, page 9-4
• Licensing Requirements for Q-in-Q Tunnels, page 9-6
• Guidelines and Limitations, page 9-6
• Configuring Q-in-Q Tunnels and Layer 2 Protocol Tunneling, page 9-7
• Verifying the Q-in-Q Configuration, page 9-15
• Configuration Examples for Q-in-Q and Layer 2 Protocol Tunneling, page 9-15
• Feature History for Q-in-Q Tunnels and Layer 2 Protocol Tunneling, page 9-16
Information About Q-in-Q Tunnels
A Q-in-Q VLAN tunnel enables a service provider to segregate the traffic of different customers in their
infrastructure, while still giving the customer a full range of VLANs for their internal use by adding a
second 802.1Q tag to an already tagged frame.
This section includes the following topics:
• Q-in-Q Tunneling, page 9-1
• Native VLAN Hazard, page 9-3
Q-in-Q Tunneling
Business customers of service providers often have specific requirements for VLAN IDs and the number
of VLANs to be supported. The VLAN ranges required by different customers in the same
service-provider network might overlap, and traffic of customers through the infrastructure might be
mixed. Assigning a unique range of VLAN IDs to each customer would restrict customer configurations
and could easily exceed the VLAN limit of 4096 of the 802.1Q specification.
Send document comments to nexus7k-docfeedback@cisco.com
9-2
Cisco Nexus 7000 Series NX-OS Interfaces Configuration Guide, Release 5.x
OL-23435-03
Chapter 9 Configuring Q-in-Q VLAN Tunnels
Information About Q-in-Q Tunnels
Note Q-in-Q is supported on port channels and vPC. To configure a port channel as an asymmetrical link, all
ports in the port channel must have the same tunneling configuration.
Using the 802.1Q tunneling feature, service providers can use a single VLAN to support customers who
have multiple VLANs. Customer VLAN IDs are preserved and traffic from different customers is
segregated within the service-provider infrastructure even when they appear to be on the same VLAN.
The 802.1Q tunneling expands VLAN space by using a VLAN-in-VLAN hierarchy and tagging the
tagged packets. A port configured to support 802.1Q tunneling is called a tunnel port. When you
configure tunneling, you assign a tunnel port to a VLAN that is dedicated to tunneling. Each customer
requires a separate VLAN, but that VLAN supports all of the customer’s VLANs.
Customer traffic tagged in the normal way with appropriate VLAN IDs come from an 802.1Q trunk port
on the customer device and into a tunnel port on the service-provider edge switch. The link between the
customer device and the edge switch is an asymmetric link because one end is configured as an 802.1Q
trunk port and the other end is configured as a tunnel port. You assign the tunnel port interface to an
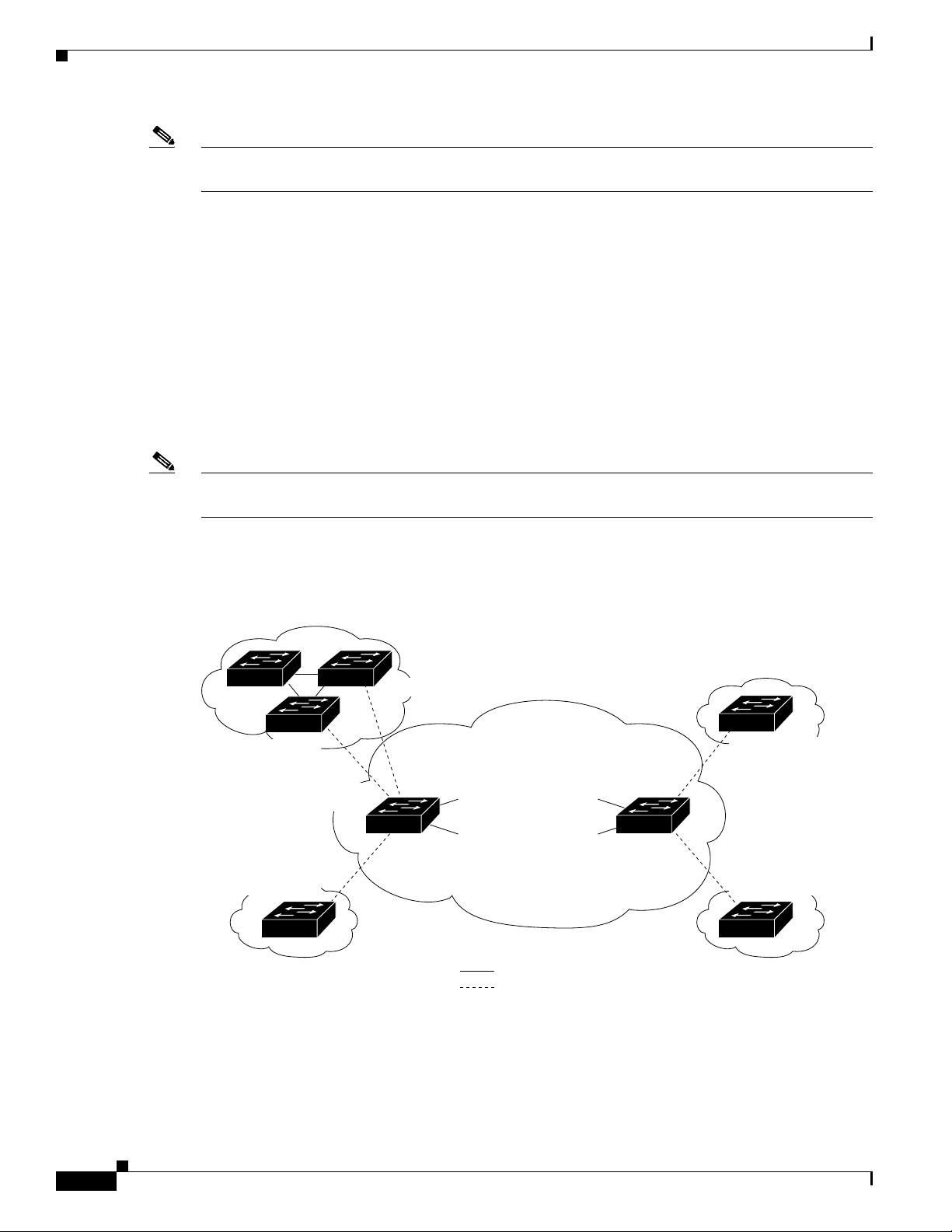
access VLAN ID unique to each customer. See Figure 9-1.
Note Selective Q-in-Q tunneling is not supported. All frames entering the tunnel port will be subject to Q-in-Q
tagging.
Figure 9-1 802.1Q-in-Q Tunnel Ports
Packets entering the tunnel port on the service-provider edge switch, which are already 802.1Q-tagged
with the appropriate VLAN IDs, are encapsulated with another layer of an 802.1Q tag that contains a
VLAN ID unique to the customer. The original 802.1Q tag from the customer is preserved in the
encapsulated packet. Therefore, packets that enter the service-provider infrastructure are double-tagged.
The outer tag contains the customer’s access VLAN ID (as assigned by the service provider), and the
Customer A
VLANs 1 to 100
Customer B
VLANs 1 to 200
Customer B
VLANs 1 to 200
Customer A
VLANs 1 to 100
Tunnel port
VLAN 40
Tunnel port
VLAN 30
Trunk
ports
Trunk
ports
Tunnel port
VLAN 30
Tunnel port
VLAN 40
Service
provider
802.1Q trunk port
802.1Q trunk port
802.1Q trunk port
802.1Q trunk port
802.1Q trunk port
74016
Trunk
Asymmetric link
Tunnel port
VLAN 30
802.1Q trunk port
802.1Q trunk port
802.1Q trunk port
802.1Q trunk port
Send document comments to nexus7k-docfeedback@cisco.com
9-3
Cisco Nexus 7000 Series NX-OS Interfaces Configuration Guide, Release 5.x
OL-23435-03
Chapter 9 Configuring Q-in-Q VLAN Tunnels
Information About Q-in-Q Tunnels
inner VLAN ID is the VLAN of the incoming traffic (as assigned by the customer). This double tagging
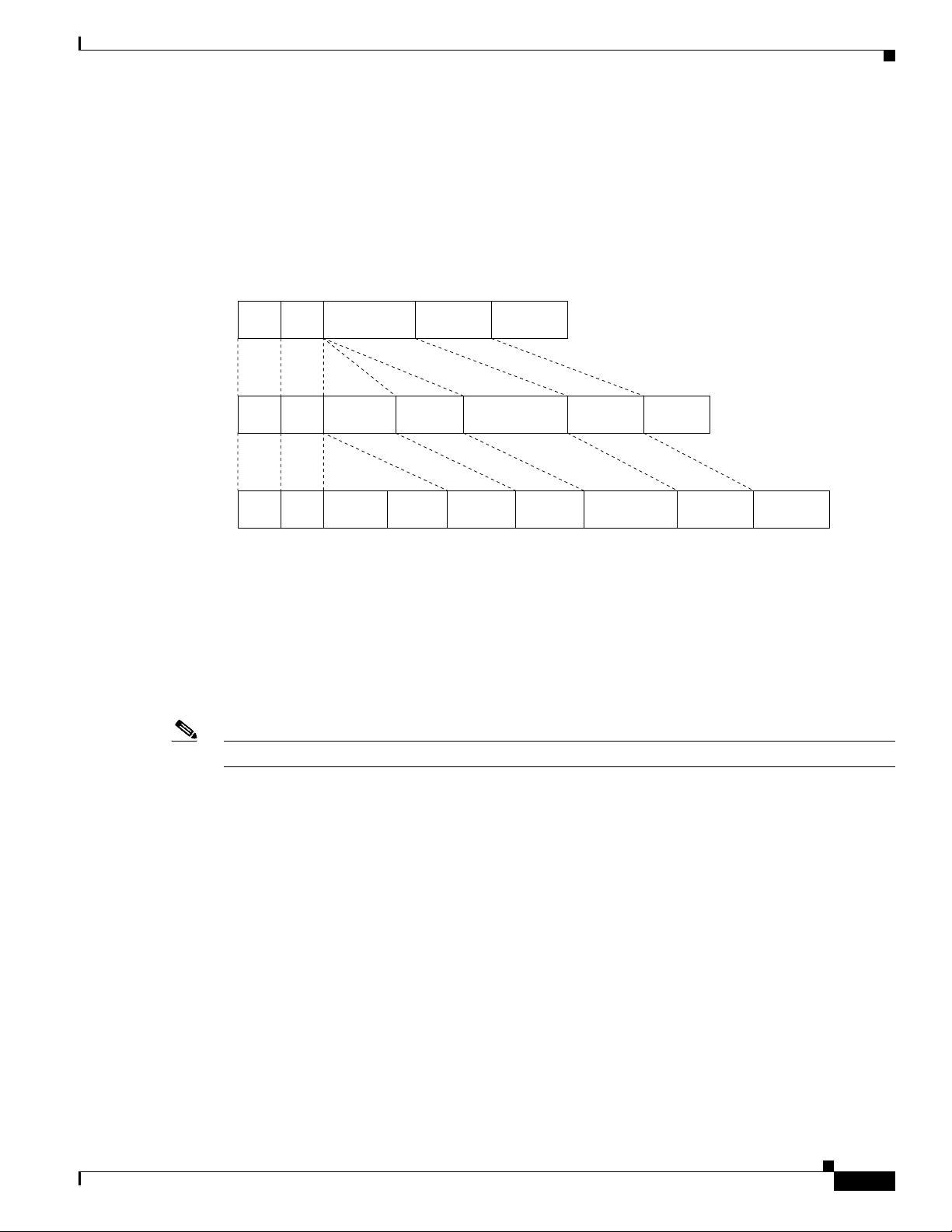
is called tag stacking, Double-Q, or Q-in-Q as shown in Figure 9-2.
Figure 9-2 Untagged, 802.1Q-Tagged, and Double-Tagged Ethernet Frames
By using this method, the VLAN ID space of the outer tag is independent of the VLAN ID space of the
inner tag. A single outer VLAN ID can represent the entire VLAN ID space for an individual customer.
This technique allows the customer’s Layer 2 network to extend across the service provider network,
potentially creating a virtual LAN infrastructure over multiple sites.
Note Hierarchical tagging, that is multi-level dot1q tagging Q-in-Q, is not supported.
Native VLAN Hazard
When configuring 802.1Q tunneling on an edge switch, you must use 802.1Q trunk ports for sending out
packets into the service-provider network. However, packets that go through the core of the
service-provider network might be carried through 802.1Q trunks, ISL trunks, or non-trunking links.
When 802.1Q trunks are used in these core switches, the native VLANs of the 802.1Q trunks must not
match any native VLAN of the dot1q-tunnel port on the same switch because traffic on the native VLAN
is not tagged on the 802.1Q transmitting trunk port.
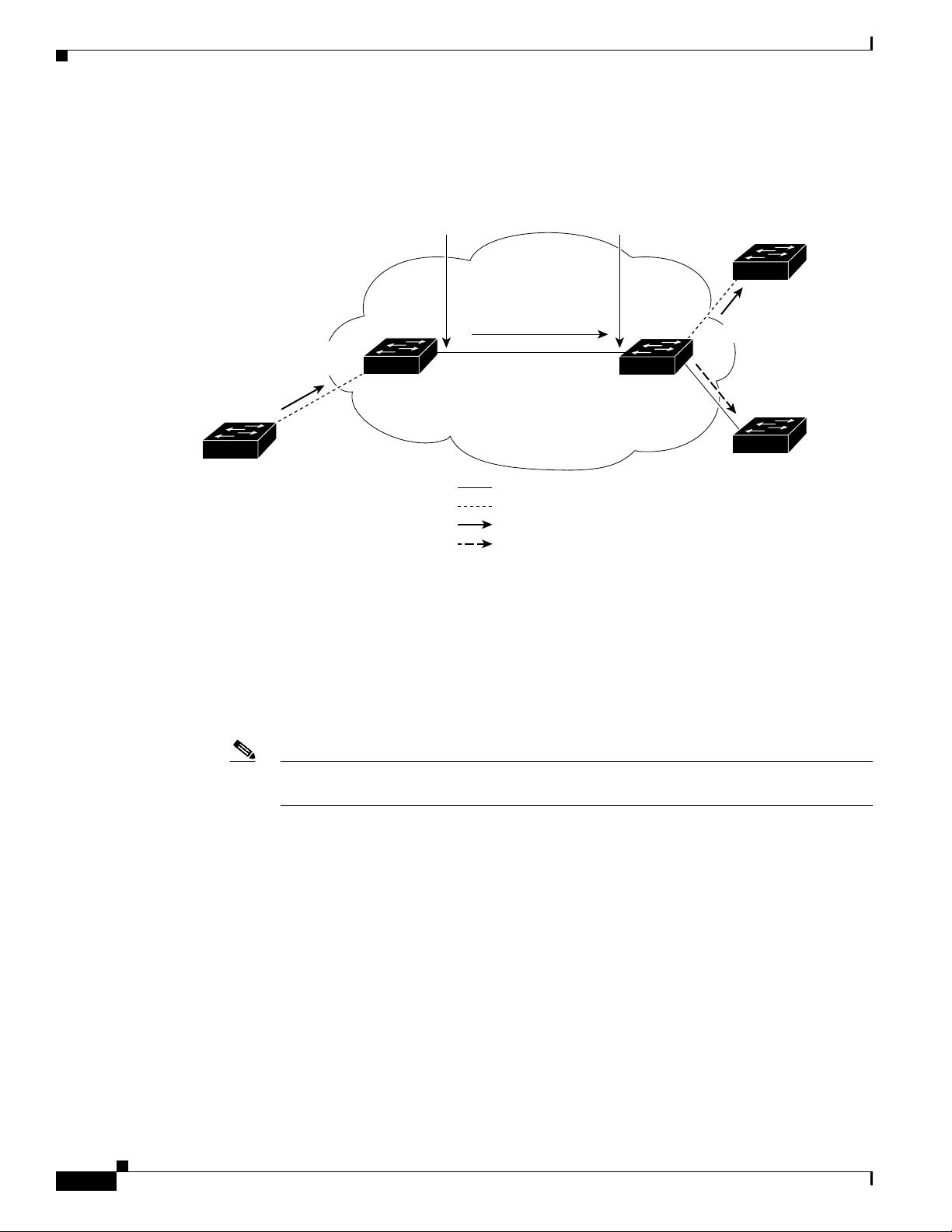
In Figure 9-3, VLAN 40 is configured as the native VLAN for the 802.1Q trunk port from Customer X
at the ingress edge switch in the service-provider network (Switch B). Switch A of Customer X sends a
tagged packet on VLAN 30 to the ingress tunnel port of Switch B in the service-provider network
belonging to access VLAN 40. Because the access VLAN of the tunnel port (VLAN 40) is the same as
the native VLAN of the edge-switch trunk port (VLAN 40), the 802.1Q tag is not added to tagged packets
that are received from the tunnel port. The packet carries only the VLAN 30 tag through the
service-provider network to the trunk port of the egress-edge switch (Switch C) and is misdirected
through the egress switch tunnel port to Customer Y.
Double-tagged
frame on trunk
links between
service provider
network devices
802.1Q frame from
customer network
Original Ethernet frame
Destination
address
Length/
EtherType
Frame Check
Sequence
Source
address
SADA Len/Etype Data FCS
SADA Len/Etype DataEtype Tag FCS
SADA Len/Etype DataEtype Tag Etype Ta g FCS
79831
Send document comments to nexus7k-docfeedback@cisco.com
9-4
Cisco Nexus 7000 Series NX-OS Interfaces Configuration Guide, Release 5.x
OL-23435-03
Chapter 9 Configuring Q-in-Q VLAN Tunnels
Information About Layer 2 Protocol Tunneling
Figure 9-3 Native VLAN Hazard
These are a couple ways to solve the native VLAN problem:
• Configure the edge switch so that all packets going out an 802.1Q trunk, including the native VLAN,
are tagged by using the vlan dot1q tag native command. If the switch is configured to tag native
VLAN packets on all 802.1Q trunks, the switch accepts untagged packets but sends only tagged
packets.
Note The vlan dot1q tag native command is a global command that affects the tagging behavior
on all trunk ports.
• Ensure that the native VLAN ID on the edge switch trunk port is not within the customer VLAN
range. For example, if the trunk port carries traffic of VLANs 100 to 200, assign the native VLAN
a number outside that range.
Information About Layer 2 Protocol Tunneling
Customers at different sites connected across a service-provider network need to run various Layer 2
protocols to scale their topology to include all remote sites, as well as the local sites. The spanning Tree
Protocol (STP) must run properly, and every VLAN should build a proper spanning tree that includes the
local site and all remote sites across the service-provider infrastructure. Cisco Discovery Protocol (CDP)
must be able to discover neighboring Cisco devices from local and remote sites, and the VLAN Trunking
Protocol (VTP) must provide consistent VLAN configuration throughout all sites in the customer
network.
802.1Q
trunk port
VLANs 30-40
Native VLAN 40
Tunnel port
Access VLAN 30
Tunnel port
Service
provider
Tag not added
for VLAN 40
Tag
removed
VLANs 5-50
Switch D
Customer X
VLANs 30-40
Native VLAN 40
Switch B Switch C
QQ
Switch E
Customer Y
Switch A
Customer X
Native
VLAN 40
101820
Trunk
Asymmetric link
Correct path for traffic
Incorrect path for traffic due to
misconfiguration of native VLAN
by sending port on Switch B
Q = 802.1Q trunk ports
Tunnel port
Access VLAN 40
Packet tagged
for VLAN 30
VLAN 40
剩余15页未读,继续阅读
豆逗乐
- 粉丝: 0
- 资源: 3
上传资源 快速赚钱
 我的内容管理
收起
我的内容管理
收起
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助

会员权益专享
最新资源
- RTL8188FU-Linux-v5.7.4.2-36687.20200602.tar(20765).gz
- c++校园超市商品信息管理系统课程设计说明书(含源代码) (2).pdf
- 建筑供配电系统相关课件.pptx
- 企业管理规章制度及管理模式.doc
- vb打开摄像头.doc
- 云计算-可信计算中认证协议改进方案.pdf
- [详细完整版]单片机编程4.ppt
- c语言常用算法.pdf
- c++经典程序代码大全.pdf
- 单片机数字时钟资料.doc
- 11项目管理前沿1.0.pptx
- 基于ssm的“魅力”繁峙宣传网站的设计与实现论文.doc
- 智慧交通综合解决方案.pptx
- 建筑防潮设计-PowerPointPresentati.pptx
- SPC统计过程控制程序.pptx
- SPC统计方法基础知识.pptx
资源上传下载、课程学习等过程中有任何疑问或建议,欢迎提出宝贵意见哦~我们会及时处理!
点击此处反馈



安全验证
文档复制为VIP权益,开通VIP直接复制
 信息提交成功
信息提交成功
评论0