OWASP移动安全测试指南:MSTG英文版
需积分: 5 175 浏览量
更新于2024-07-16
收藏 23.94MB PDF 举报
"OWASP Mobile Security Testing Guide (MSTG) - 英文版"
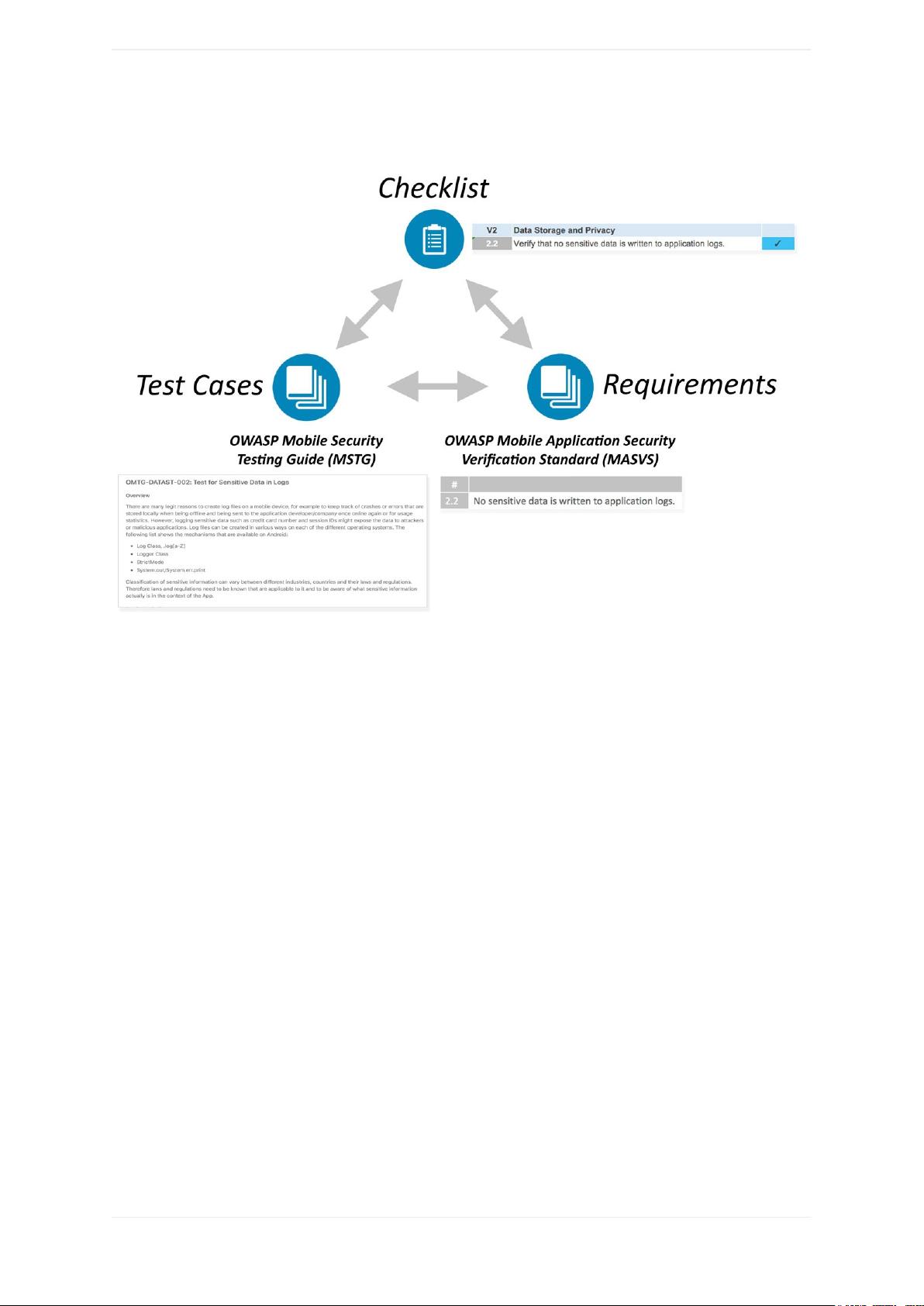
MSTG,即OWASP Mobile Security Testing Guide,是一本全面的手册,专注于移动应用的安全测试和逆向工程。它详细阐述了如何验证OWASP Mobile Application Verification Standard (MASVS)中列出的控制措施。该指南涵盖了多个关键领域,旨在帮助安全专家和开发者确保移动应用程序的安全性。
在手册中,你可以找到以下主要知识点:
1. **概述**:
- 引言:介绍MSTG的目的和重要性,以及它与MASVS的关系。
- 发展历程:展示了MSTG的更新历史。
- 前言:提供了关于移动安全测试的背景信息。
2. **移动应用分类**:
- 对不同类型的移动应用进行了分类,以理解其特定的安全需求。
3. **移动应用安全测试**:
- 一般移动应用测试指南:涵盖了通用的测试方法和流程。
- 移动应用身份验证架构:讨论了各种身份验证模式和最佳实践。
4. **网络通信测试**:
- 检查应用程序如何安全地处理网络通信,包括加密、会话管理等。
5. **移动应用中的加密**:
- 探讨了移动应用中数据保护的重要性,包括加密库和算法的选择。
6. **代码质量测试**:
- 评估代码质量,查找潜在的安全漏洞和反编译风险。
7. **篡改与逆向工程**:
- 讨论如何防止应用被篡改和逆向工程,以及如何测试这些防护措施的有效性。
8. **用户教育**:
- 提供关于提高用户安全意识和最佳实践的测试策略。
9. **平台特定的测试指南**:
- **Android测试指南**:深入到Android平台,包括环境设置、数据存储、加密API、本地认证、网络API和平台API的测试。
- **iOS测试指南**:针对iOS平台,涵盖环境搭建、数据存储、加密API、本地认证、网络API和平台API的测试,以及代码质量和构建设置。
10. **防逆向工程策略**:
- 在Android和iOS平台上探讨了如何实施反逆向工程防御机制。
MSTG是移动应用安全领域的一份宝贵资源,它提供了一套全面的测试方法来确保应用的安全性,涵盖了从基础的编码实践到平台特定的安全测试。无论是开发者、安全工程师还是渗透测试人员,都可以从中受益,提升其在移动安全领域的专业能力。
2020-02-29 上传
2021-01-27 上传
2021-05-25 上传
2021-08-07 上传
2021-06-18 上传
2021-04-29 上传
2021-05-25 上传
2024-12-28 上传
没人不认识我
- 粉丝: 161
- 资源: 33
最新资源
- VC++ Win32俄罗斯方块游戏源码(新)
- Algotrading:为Algotrading项目创建的仓库
- lean-cli:用于在本地和云中运行LEAN引擎的CLI
- suit.zip_单片机开发_Java_
- cutelog:用于记录的GUI
- sandbox:Nette Framework沙箱项目
- BigCommerce Aliexpress Importer-crx插件
- scientific_computing_cookbook:用于科学计算中各种任务的简单配方
- javawebTest01
- svm_cvx:使用CVX进行凸优化的SVM实现
- AndroidX-Jetpack-Practice:本仓库致力于建立最全,最新的AndroidX Jetpack相关组件的实践项目以及组件对应的分析文章(持续更新中)如果对你有帮助,请在右上角star一下,感谢
- SerialTool:跨平台的Serial-PortTCPUDP调试工具
- 参考资料-WI-HJ0105石材养护服务检查标准和考核办法.zip
- Free Visio Viewer (Mac, Windows, Linux)-crx插件
- matlabkalman.zip_matlab例程_Visual_C++_
- 脚本轮椅