12 CHAPTER 1 Introduction
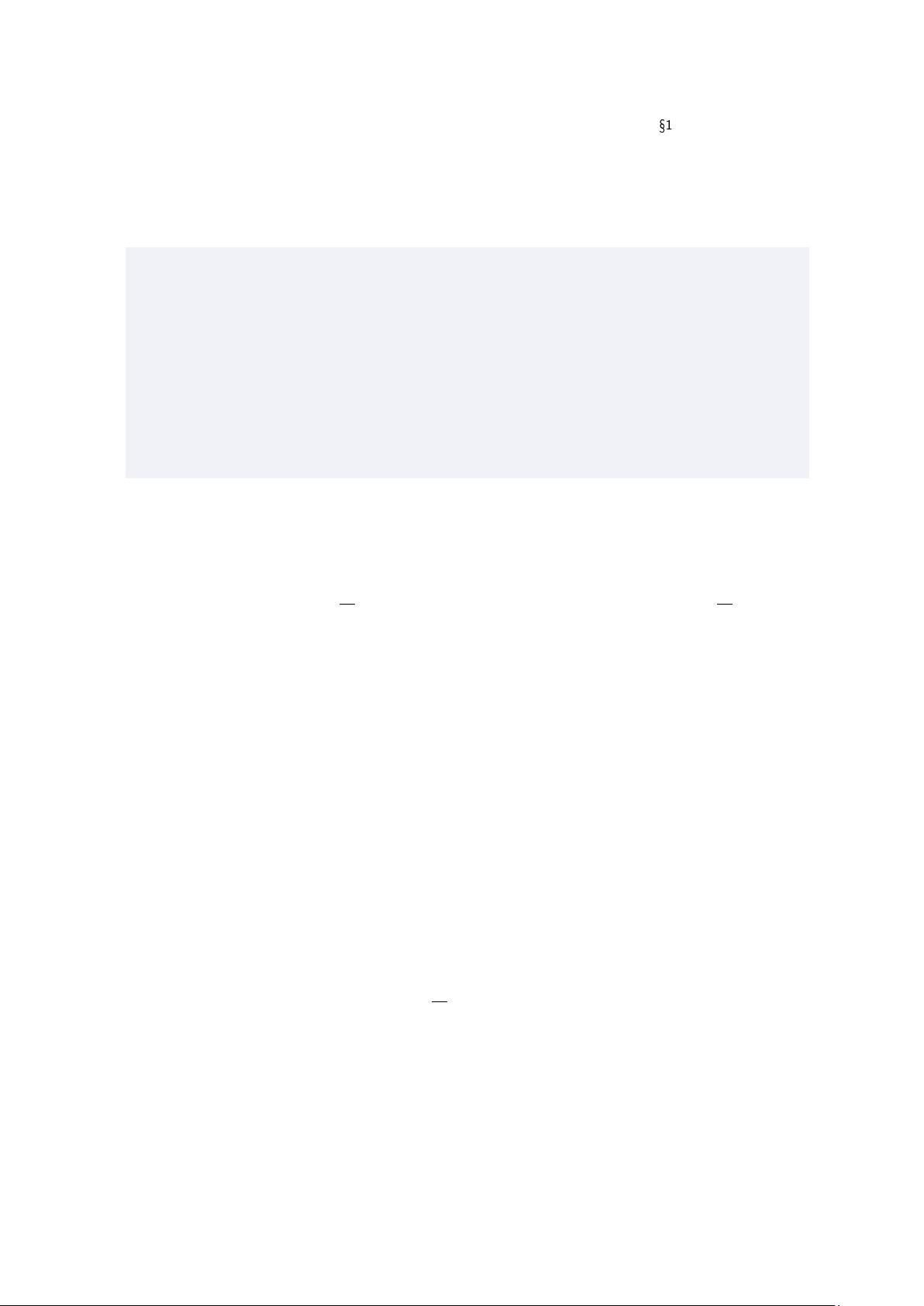
EXERCISE 1.35 Let m be an RSA modulus, as in the previous exercise. Let J
m
= {y ∈ Z
∗
m
:
(y/m) = 1}, the set of all integers in Z
∗
m
with Jacobi symbol 1. The Quadratic Residuosity
(QR) problem is to decide whether a given y ∈ J
m
is a quadratic residue modulo m or not,
that is, whether y ∈ QR
m
, where QR
m
= {y ∈ Z
∗
m
: ∃
x∈Z
∗
m
y = x
2
mod m}. Show that the
QR problem is random self-reducible.
1.3.4 RANDOM ORACLE MODEL
DEFINITION 1.36 A function H : {0, 1}
∗
→ {0, 1}
k
, mapping bit strings of arbitrary length
to bit strings of a fixed length k, k ≥ 0, is called a hash function. Function H is called a
cryptographic hash function, if it is easy to compute H(x) given any string x, and one or
more of the following requirements are satisfied:
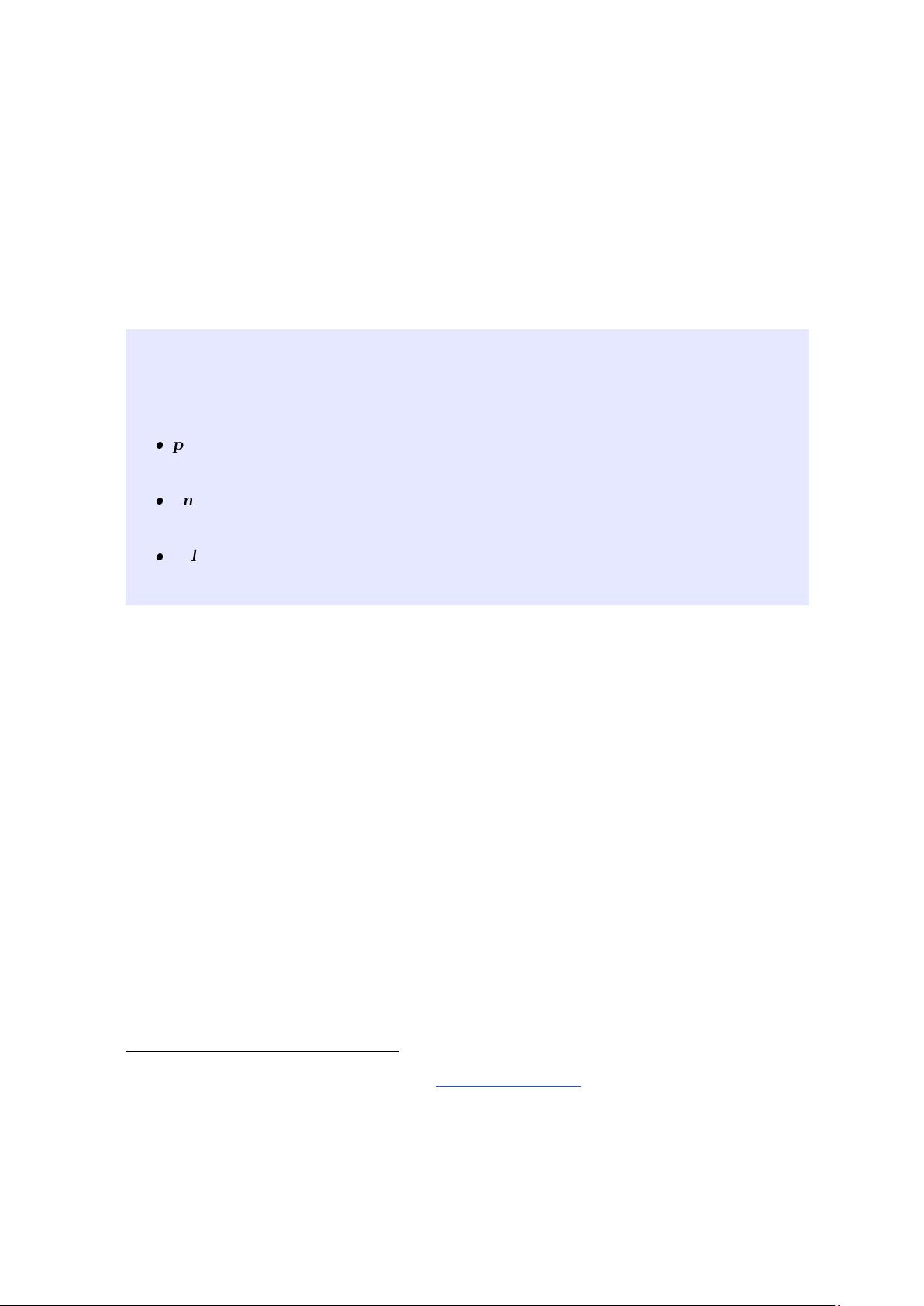
preimage resistance (onewayness): given a k-bit string y, it is hard to find a bit
string x such that H(x) = y.
2nd-preimage resistance (weak collision resistance): given a bit string x, it is
hard to find a bit string x
0
6= x such that H(x
0
) = H(x).
collision resistance (strong collision resistance): it is hard to find a pair of bit
strings (x, x
0
) with x 6= x
0
such that H(x) = H(x
0
).
In general, collision resistance implies 2nd-preimage resistance, but collision resistance need
not imply preimage resistance. In practice, however, cryptographic hash functions usually
satisfy all three requirements.
Practical examples of cryptographic hash functions are MD5, SHA-1, SHA-256, with
output lengths k = 128, k = 160, and k = 256, respectively.
9
If collision resistance is not
required, one may truncate the outputs by discarding, e.g., the last k/2 bits; the resulting
hash function is still preimage resistant.
Many protocols make use of a cryptographic hash function. In order to be able to prove
anything useful on the security of such protocols one commonly uses the so-called random
oracle model. In this model, a cryptographic hash function is viewed as a random oracle,
which when queried will behave as a black box containing a random function H : {0, 1}
∗
→
{0, 1}
k
, say. If the oracle is queried on an input value x, it will return the output value H(x).
As a consequence, if the oracle is queried multiple times on the same input, it will return
the same output value, as H is a function. Moreover, if one observes the distribution of the
output value for different input values, the distribution will be uniform, as H is a random
function.
Note that the use of the random oracle model is a heuristic! If we prove a protocol secure
in the random oracle model, it does not follow that the same protocol using, e.g., SHA-256
as its hash function is secure, since SHA-256 is simply not a random function.
10
Thus, the practical upshot of the random oracle model is that a protocol proved secure
9
In August 2004, collisions for MD5 have (finally) been shown; furthermore, collisions for SHA-0 (a previous
version of SHA-1) have also been found. See this Mathematica notebook for some example collisions.
10
It is even possible to construct protocols that can be proved secure in the random oracle model, but are
insecure when used with some concrete hash function. Yet, these “counterexamples” are not realistic. See also
Exercise 5.22.