空间级Klessydra RISC-V微控制器:首个卫星应用
需积分: 9 85 浏览量
更新于2024-07-17
收藏 1.99MB PDF 举报
"这篇文档是关于首个太空级Klessydra RISC-V微控制器的介绍,该控制器将被用于卫星发射。由罗马Sapienza大学数字系统实验室的研究人员,包括Luigi Blasi、Francesco Vigli等人共同完成。他们讨论了在空间环境下微控制器所面临的挑战,以及为RISC-V处理器核心设计的容错架构,同时展示了Klessydra Fx3x核心家族的结果和未来展望。"
本文档主要涉及以下知识点:
1. **RISC-V架构**:RISC-V是一种开放源代码指令集架构,它在嵌入式和高性能计算领域日益受到关注。Klessydra微控制器采用了RISC-V架构,这意味着它可以利用RISC-V的简洁、高效和模块化设计特性,适应空间应用中的低功耗和高可靠性要求。
2. **太空环境问题**:在太空中,电子设备会面临极端的温度变化、辐射、微小陨石撞击等环境挑战。这些因素可能导致硬件故障,因此对微控制器的设计提出了特殊要求,如辐射硬化和抗单事件效应(如单粒子翻转和单事件锁定)的能力。
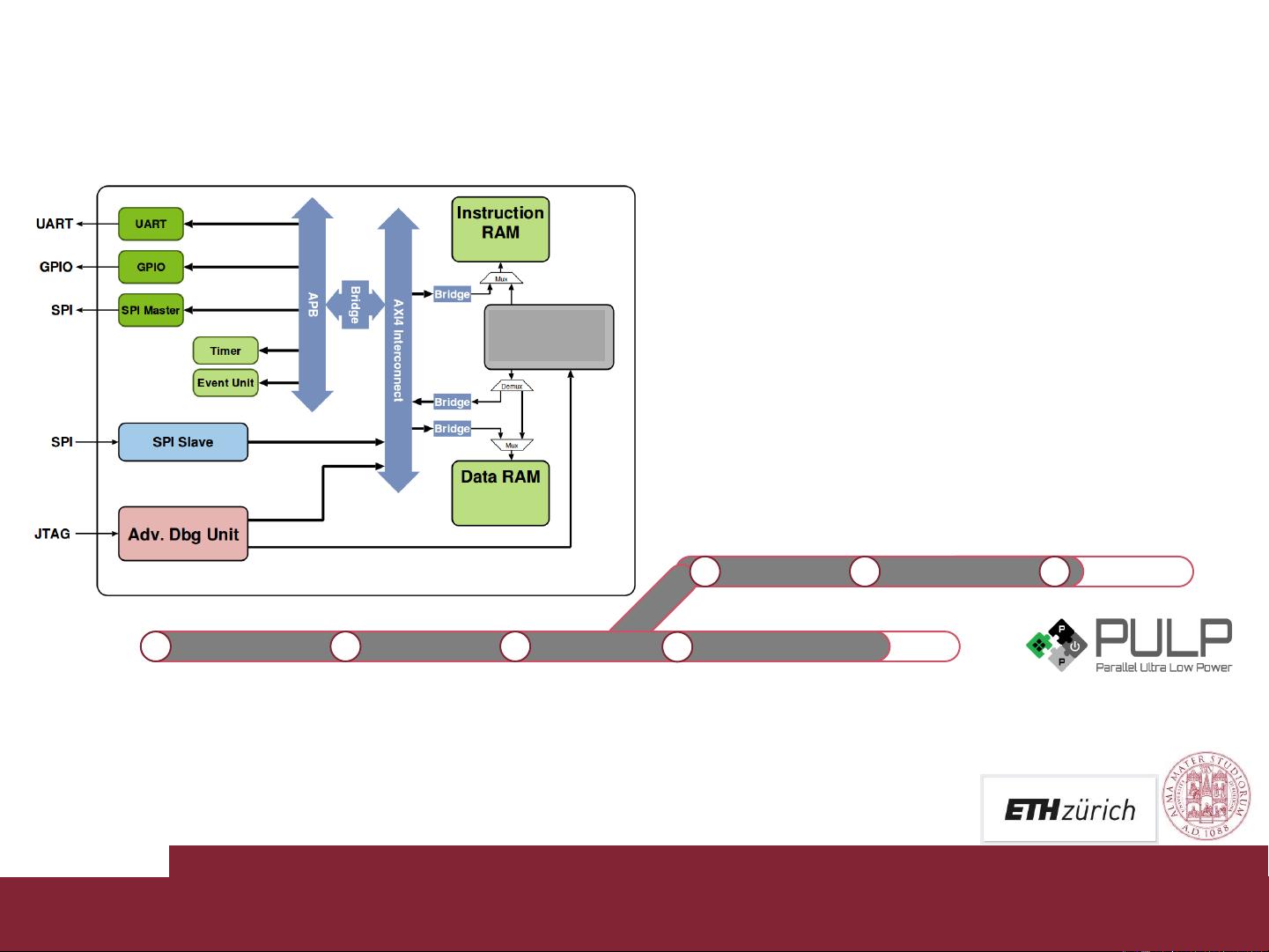
3. **架构级容错**:为了确保在太空环境中的可靠运行,Klessydra微控制器采用了架构级别的容错设计。这可能包括冗余处理单元、错误检测和校正技术,以及能够在硬件故障时切换到备用系统的机制。
4. **Klessydra Fx3x核心家族**:这个核心家族是Klessydra微控制器的核心组成部分,它们可能是针对太空应用定制的RISC-V内核,具有特定的容错特性和优化。每个核心可能包含了多种功能,以适应不同的任务需求和故障场景。
5. **结果与展望**:文档中提到了研究团队的初步结果,并对未来的研发方向进行了展望。这可能涉及到性能提升、功耗优化、更高级别的容错策略,以及如何进一步推广这种技术在太空领域的应用。
6. **学术与商业合作**:由Sapienza大学的研究团队和行业合作伙伴共同开发的Klessydra微控制器,体现了学术研究与工业实践的结合,有助于推动航天技术的创新和商业化进程。
7. **COTS组件的使用**:文中提及在纳米卫星(如CubeSat)中通常使用商用现成(COTS)组件,但必须进行特殊设计以适应太空的极端条件。Klessydra项目就是这样的例子,它将COTS组件的经济性与空间级应用的可靠性相结合。
通过这些深入研究,Klessydra RISC-V微控制器为未来的太空任务提供了新的可能性,特别是在小型卫星和低成本航天器领域,它有望成为一种标准解决方案,促进太空探索和应用的广泛发展。
2018-07-13 上传
2021-03-13 上传
2023-05-02 上传
2023-05-23 上传
2023-04-27 上传
2023-03-31 上传
2023-06-13 上传
2023-03-28 上传
2023-05-31 上传
2023-06-09 上传
Pursue_permanent
- 粉丝: 26
- 资源: 4
最新资源
- C语言快速排序算法的实现与应用
- KityFormula 编辑器压缩包功能解析
- 离线搭建Kubernetes 1.17.0集群教程与资源包分享
- Java毕业设计教学平台完整教程与源码
- 综合数据集汇总:浏览记录与市场研究分析
- STM32智能家居控制系统:创新设计与无线通讯
- 深入浅出C++20标准:四大新特性解析
- Real-ESRGAN: 开源项目提升图像超分辨率技术
- 植物大战僵尸杂交版v2.0.88:新元素新挑战
- 掌握数据分析核心模型,预测未来不是梦
- Android平台蓝牙HC-06/08模块数据交互技巧
- Python源码分享:计算100至200之间的所有素数
- 免费视频修复利器:Digital Video Repair
- Chrome浏览器新版本Adblock Plus插件发布
- GifSplitter:Linux下GIF转BMP的核心工具
- Vue.js开发教程:全面学习资源指南