802.1X端口认证:网络访问控制技术解析
"802.1X端口认证是一种网络访问控制概念,它在设备被允许与网络上的其他设备通信之前对其进行评估。该技术通过扩展认证协议(EAP)在局域网(LAN)上运行,具体过程称为EAPOL(扩展认证协议在局域网上)。802.1X标准提供了对这一概念的应用及其对当今大多数计算机网络的影响的探讨。书中对基于端口的认证进行了入门级的概述,包括802.1X端口认证的描述、标准的历史和技术文档的发布详情,以及网络中的三个组件(客户端、认证设备和认证服务器)之间的连接细节。内容侧重于802.1X及其在网络实施中涉及的相关协议和组件的技术方面,特别是针对Cisco设备的深入讨论。书中的例子来源于802.1X的实际应用,并解决了在Cisco环境中遇到的故障排除问题。每章都包含主题概述,采用理论与实践相结合的方法,力求用易于理解的语言解释这个复杂的概念,并探讨了该网络协议在现代计算机网络中的各种应用。"
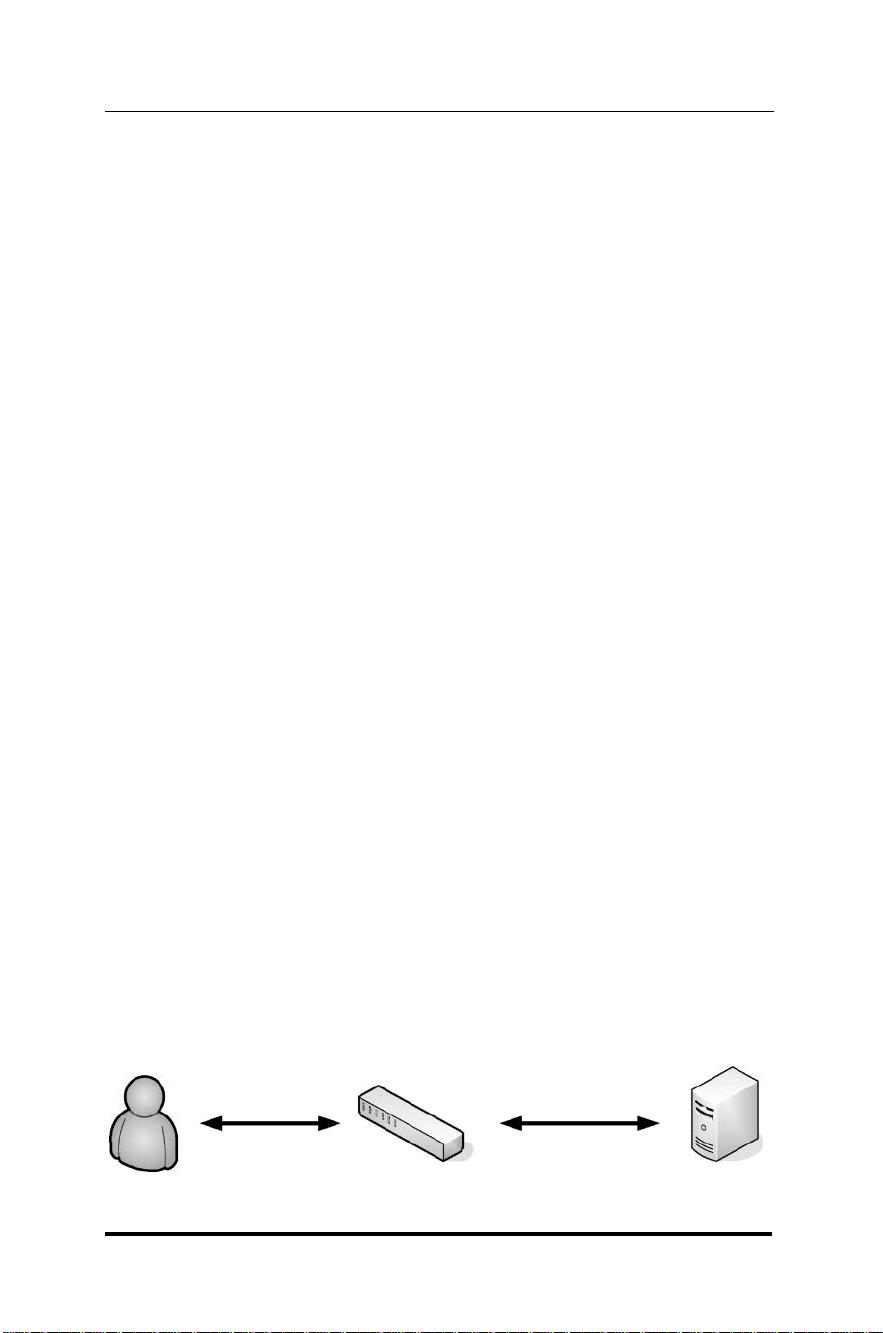
802.1X认证是网络安全领域的一个关键组成部分,它确保只有经过身份验证的设备才能接入网络。这种认证机制基于端口状态,未认证的设备只能与认证服务器通信,直到通过身份验证后才能完全访问网络资源。EAP(Extensible Authentication Protocol)是802.1X的核心,它允许使用多种不同的认证方法,如密码、智能卡或证书,以适应不同环境的安全需求。
标准的发展历程和相关技术文档是理解802.1X的重要背景。这些文档定义了协议的规范,包括EAPOL,它规定了在以太网链路上如何传输EAP报文。网络的三个关键组件——客户端(通常是指网络设备,如PC或移动设备)、认证设备(通常是指交换机或接入点)和认证服务器(处理实际的身份验证过程)之间的交互是801.1X实施的关键部分。
在实施802.1X时,必须考虑网络设计和配置,特别是在使用特定厂商设备(如Cisco)的情况下。书中的例子和故障排除指南有助于读者理解如何在实际环境中部署和维护802.1X。此外,书中还探讨了不同应用情况,展示了802.1X如何在今天的网络环境中提供安全保障,防止未经授权的设备接入,从而增强整体网络安全。
通过遵循清晰的结构,先介绍主题,然后详细阐述,最后总结要点,本书旨在为读者提供全面的802.1X端口认证知识,无论他们是对网络技术有基础了解还是寻求更深入的理解。作者以技术专家的角度,结合理论与实践,使复杂的技术概念变得易于理解和应用。
307 浏览量
2010-03-19 上传
152 浏览量
113 浏览量
点击了解资源详情
178 浏览量
2010-05-09 上传
2021-10-18 上传
224 浏览量
simboda
- 粉丝: 0
最新资源
- 经典J2ME坦克对战游戏:回顾与介绍
- ZAProxy自动化工具集合:提升Web安全测试效率
- 破解Steel Belted Radius 5.3安全验证工具
- Python实现的德文惠斯特游戏—开源项目
- 聚客下载系统:体验极速下载的革命
- 重力与滑动弹球封装的Swift动画库实现
- C语言控制P0口LED点亮状态教程及源码
- VB6中使用SQLite实现列表查询的示例教程
- CMSearch:在CraftMania服务器上快速搜索玩家的Web应用
- 在VB.net中实现Code128条形码绘制教程
- Java SE Swing入门实例分析
- Java编程语言设计课程:自动机的构建与最小化算法实现
- SI9000阻抗计算软件:硬件工程师的高频信号分析利器
- 三大框架整合教程:S2SH初学者快速入门
- PHP后台管理自动化生成工具的使用与资源分享
- C#开发的多线程控制台贪吃蛇游戏源码解析