没有合适的资源?快使用搜索试试~ 我知道了~
首页《802.11无线网络权威指南》:全面探讨无线网络部署与安全
《802.11无线网络权威指南》:全面探讨无线网络部署与安全
《802.11无线网络权威指南》第二版是一本深度解析无线网络技术的专业书籍,由美国作者MattheW S.Gast撰写,中文版ISBN: 9787564110062,由东南大学出版社出版,于2007年12月发行。该书针对严谨的系统管理员和网络管理员设计,旨在帮助读者理解和解决无线网络部署和维护中的复杂问题。
首先,书的开头部分介绍了无线网络的基本概念,强调了无线网络带来的便利性和背后的复杂性。它探讨了如何构建移动用户友好的网络,扩展无线覆盖范围,以及处理无线网络的安全问题,包括早期的WEP标准及其局限,以及后续的发展如动态WEP、802.1X和802.11i安全标准。书中特别关注了网络安全,这是网络管理员必须重视的重要任务,书中还提供了使用Ethereal等网络分析工具进行故障排除的方法。
其次,书中详细解读了802.11协议族,涵盖了802.11b、11a、g以及即将成为标准的802.11n协议,重点在于网络规划、移动性管理、频谱管理和功率控制等方面。作者还强调了如何评估无线网络性能并优化其性能,使之满足预期的用户需求并应对增加的用户负载。
此外,书中还包括对无线网卡配置、操作系统(如Linux、Windows和MAC OS X)与接入点设置的指导,以及实用的理论知识和实际操作建议的结合,使得读者能够将理论知识转化为实际操作技能。
最后,MattheW S.Gast丰富的行业经验和专业背景体现在他对身份管理、身份认证协议、联盟网络和动态授权等领域深入的理解,这些知识对于维护现代无线网络环境至关重要。他在Interop Labs的工作经历和全球研讨会的参与,使他能分享最新的网络安全协议和技术。
《802.11无线网络权威指南》第二版不仅提供了全面的802.11协议和技术知识,还强调了安全性、网络管理和实践操作,是任何负责无线网络管理的专业人员不可或缺的参考书籍。
16
Extended service areas are the highest-level abstraction supported by 802.11 networks. Access points
in an ESS operate in concert to allow the outside world to use a single MAC address to talk to a station
somewhere within the ESS. In Figure 2-5
, the router uses a single MAC address to deliver frames to a
mobile station; the access point with which that mobile station is associated delivers the frame. The
router remains ignorant of the location of the mobile station and relies on the access points to deliver
the frame.
2.2.2 The Distribution System, Revisited
With an understanding of how an extended service set is built, I'd like to return to the concept of the
distribution system. 802.11 describes the distribution system in terms of the services it provides to
wireless stations. While these services will be described in more detail later in this chapter, it is worth
describing their operation at a high level.
The distribution system provides mobility by connecting access points. When a frame is given to the
distribution system, it is delivered to the right access point and relayed by that access point to the
intended destination.
The distribution system is responsible for tracking where a station is physically located and delivering
frames appropriately. When a frame is sent to a mobile station, the distribution system is charged with
the task of delivering it to the access point serving the mobile station. As an example, consider the
router in Figure 2-5
. The router simply uses the MAC address of a mobile station as its destination.
The distribution system of the ESS pictured in Figure 2-5
must deliver the frame to the right access
point. Obviously, part of the delivery mechanism is the backbone Ethernet, but the backbone network
cannot be the entire distribution system because it has no way of choosing between access points. In
the language of 802.11, the backbone Ethernet is the distribution system medium, but it is not the entire
distribution system.
To find the rest of the distribution system, we need to look to the access points themselves. Most
access points currently on the market operate as bridges. They have at least one wireless network
interface and at least one Ethernet network interface. The Ethernet side can be connected to an existing
network, and the wireless side becomes an extension of that network. Relaying frames between the
two network media is controlled by a bridging engine.
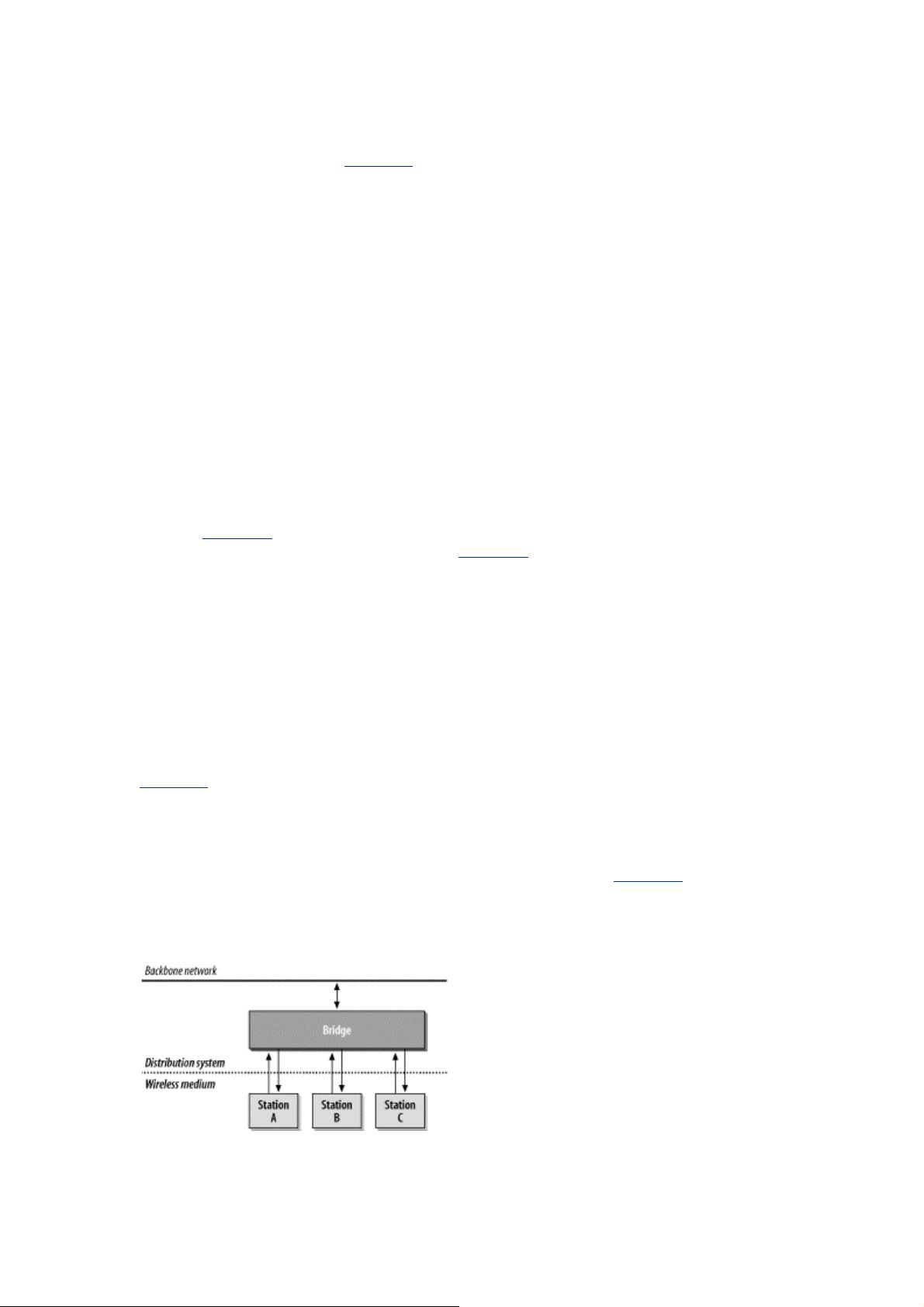
Figure 2-6
illustrates the relationship between the access point, backbone network, and the distribution
system. The access point has two interfaces connected by a bridging engine. Arrows indicate the
potential paths to and from the bridging engine. Frames may be sent by the bridge to the wireless
network; any frames sent by the bridge's wireless port are transmitted to all associated stations. Each
associated station can transmit frames to the access point. Finally, the backbone port on the bridge can
interact directly with the backbone network. The distribution system in Figure 2-6 is composed of the
bridging engine plus the wired backbone network..
Figure 2-6. Distribution system in common 802.11 access point implementations
Every frame sent by a mobile station in an infrastructure network must use the distribution system. It is
easy to understand why interaction with hosts on the backbone network must use the distribution
17
system. After all, they are connected to the distribution system medium. Wireless stations in an
infrastructure network depend on the distribution system to communicate with each other because they
are not directly connected to each other. The only way for station A to send a frame to station B is by
relaying the frame through the bridging engine in the access point. However, the bridge is a
component of the distribution system. While what exactly makes up the distribution system may seem
like a narrow technical concern, there are some features of the 802.11 MAC that are closely tied to its
interaction with the distribution system.
2.2.2.1 Inter-access point communication as part of the distribution system
Included with this distribution system is a method to manage associations. A wireless station is
associated with only one access point at a time. If a station is associated with one access point, all the
other access points in the ESS need to learn about that station. In Figure 2-5
, AP4 must know about all
the stations associated with AP1. If a wireless station associated with AP4 sends a frame to a station
associated with AP1, the bridging engine inside AP4 must send the frame over the backbone Ethernet
to AP1 so it can be delivered to its ultimate destination. To fully implement the distribution system,
access points must inform other access points of associated stations. Naturally, many access points on
the market use an inter-access point protocol (IAPP) over the backbone medium. There is, however,
no standardized method for communicating association information to other members of an ESS.
Proprietary technology is giving way to standardization, however. One of the major projects in the
IEEE 802.11 working group is the standardization of the IAPP.
2.2.2.2 Wireless bridges and the distribution system
Up to this point, I have tacitly assumed that the distribution system was an existing fixed network.
While this will often be the case, the 802.11 specification explicitly supports using the wireless
medium itself as the distribution system. The wireless distribution system configuration is often called
a "wireless bridge" configuration because it allows network engineers to connect two LANs at the link
layer. Wireless bridges can be used to quickly connect distinct physical locations and are well-suited
for use by access providers. Most 802.11 access points on the market now support the wireless bridge
configuration, though it may be necessary to upgrade the firmware on older units.
2.2.3 Network Boundaries
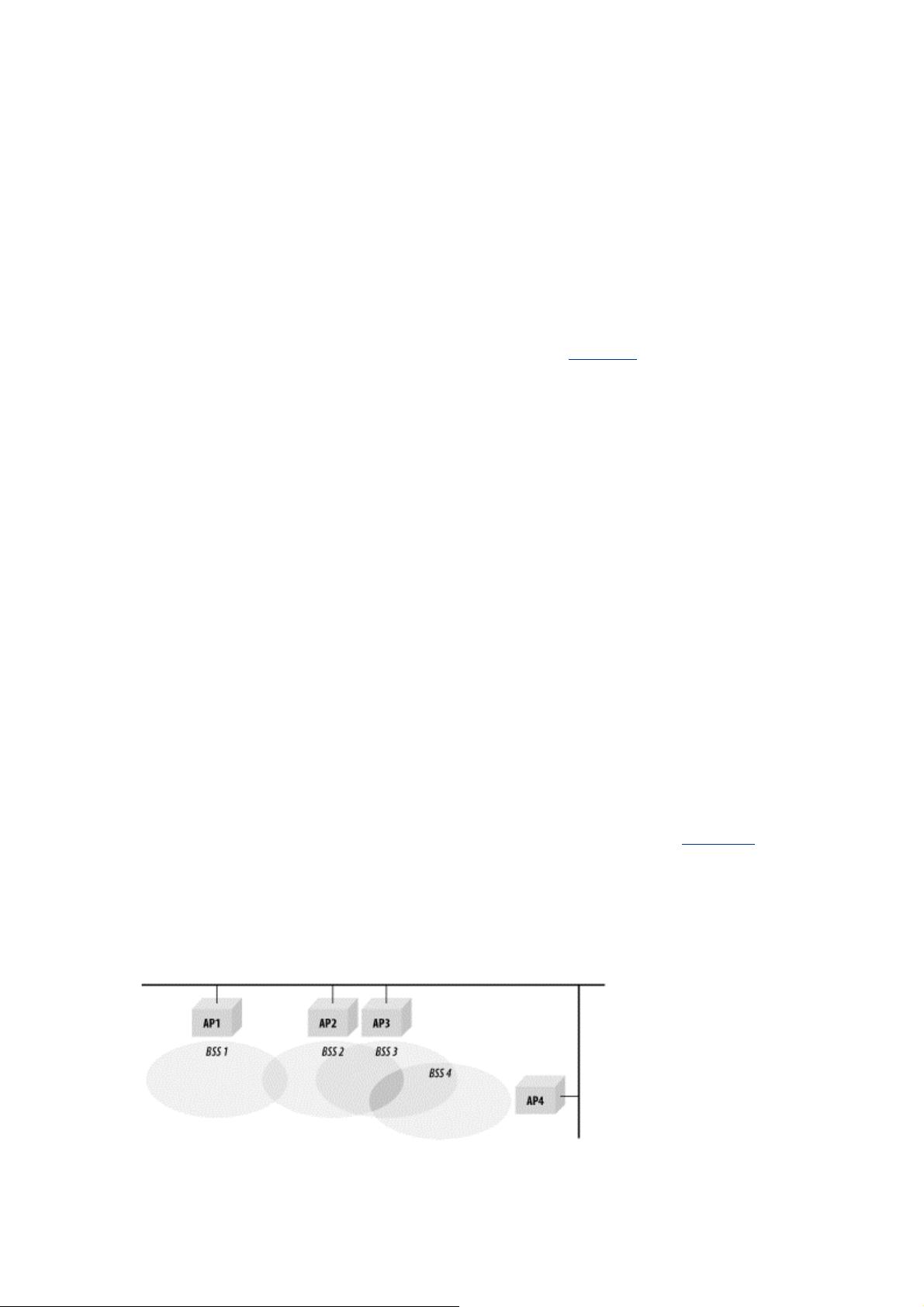
Because of the nature of the wireless medium, 802.11 networks have fuzzy boundaries. In fact, some
degree of fuzziness is desirable. As with mobile telephone networks, allowing basic service areas to
overlap increases the probability of successful transitions between basic service areas and offers the
highest level of network coverage. The basic service areas on the right of Figure 2-7
overlap
significantly. This means that a station moving from BSS2 to BSS4 is not likely to lose coverage; it
also means that AP3 (or, for that matter, AP4) can fail without compromising the network too badly.
On the other hand, if AP2 fails, the network is cut into two disjoint parts, and stations in BSS1 lose
connectivity when moving out of BSS1 and into BSS3 or BSS4.
Figure 2-7. Overlapping BSSs in an ESS
18
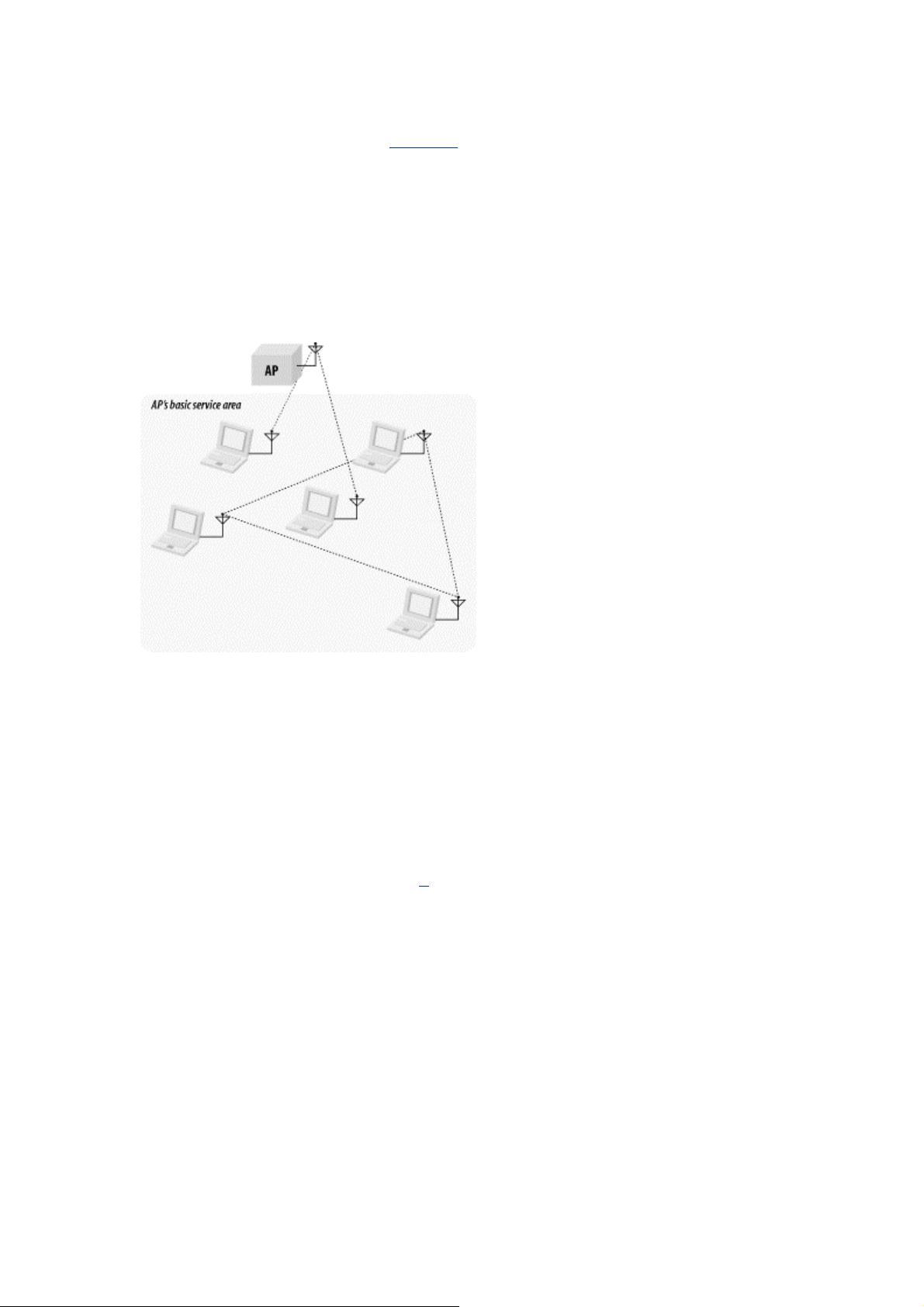
Different types of 802.11 networks may also overlap. Independent BSSs may be created within the
basic service area of an access point. Figure 2-8
illustrates spatial overlap. An access point appears at
the top of the figure; its basic service area is shaded. Two stations are operating in infrastructure mode
and communicate only with the access point. Three stations have been set up as an independent BSS
and communicate with each other. Although the five stations are assigned to two different BSSs, they
may share the same wireless medium. Stations may obtain access to the medium only by using the
rules specified in the 802.11 MAC; these rules were carefully designed to enable multiple 802.11
networks to coexist in the same spatial area. Both BSSs must share the capacity of a single radio
channel, so there may be adverse performance implications from co-located BSSs.
Figure 2-8. Overlapping network types
2.3 802.11 Network Operations
From the outset, 802.11 was designed to be just another link layer to higher-layer protocols. Network
administrators familiar with Ethernet will be immediately comfortable with 802.11. The shared
heritage is deep enough that 802.11 is sometimes referred to as "wireless Ethernet."
The core elements present in Ethernet are present in 802.11. Stations are identified by 48-bit IEEE 802
MAC addresses. Conceptually, frames are delivered based on the MAC address. Frame delivery is
unreliable, though 802.11 incorporates some basic reliability mechanisms to overcome the inherently
poor qualities of the radio channels it uses.
[4]
[4]
I don't mean "poor" in an absolute sense. But the reliability of wireless transmission is
really not comparable to the reliability of a wired network.
From a user's perspective, 802.11 might just as well be Ethernet. Network administrators, however,
need to be conversant with 802.11 at a much deeper level. Providing MAC-layer mobility while
following the path blazed by previous 802 standards requires a number of additional services and more
complex framing.
2.3.1 Network Services
One way to define a network technology is to define the services it offers and allow equipment
vendors to implement those services in whatever way they see fit. 802.11 provides nine services. Only
three of the services are used for moving data; the remaining six are management operations that allow
the network to keep track of the mobile nodes and deliver frames accordingly.

19
The services are described in the following list and summarized in Table 2-1:
Distribution
This service is used by mobile stations in an infrastructure network every time they send data.
O
nce a frame has been accepted by an access point, it uses the distribution service to deliver
the frame to its destination. Any communication that uses an access point travels through the
distribution service, including communications between two mobile stations associated with
the same access point.
Integration
Integration is a service provided by the distribution system; it allows the connection of the
distribution system to a non-IEEE 802.11 network. The integration function is specific to the
distribution system used and therefore is not specified by 802.11, except in terms of the
services it must offer.
Association
Delivery of frames to mobile stations is made possible because mobile stations register, or
associate, with access points. The distribution system can then use the registration information
to determine which access point to use for any mobile station. Unassociated stations are not
"on the network," much like workstations with unplugged Ethernet cables. 802.11 specifies
the function that must be provided by the distribution system using the association data, but it
does not mandate any particular implementation.
Reassociation
When a mobile station moves between basic service areas within a single extended service
area, it must evaluate signal strength and perhaps switch the access point with which it is
associated. Reassociations are initiated by mobile stations when signal conditions indicate that
a different association would be beneficial; they are never initiated by the access point. After
the reassociation is complete, the distribution system updates its location records to reflect the
reachability of the mobile station through a different access point.
Disassociation
To terminate an existing association, stations may use the disassociation service. When
stations invoke the disassociation service, any mobility data stored in the distribution system
is removed. Once disassociation is complete, it is as if the station is no longer attached to the
network. Disassociation is a polite task to do during the station shutdown process. The MAC
is, however, designed to accommodate stations that leave the network without formally
disassociating.
Authentication
Physical security is a major component of a wired LAN security solution. Network attachment
points are limited, often to areas in offices behind perimeter access control devices. Network
equipment can be secured in locked wiring closets, and data jacks in offices and cubicles can
be connected to the network only when needed. Wireless networks cannot offer the same level
of physical security, however, and therefore must depend on additional authentication routines
to ensure that users accessing the network are authorized to do so. Authentication is a
necessary prerequisite to association because only authenticated users are authorized to use
the network. (In practice, though, many access points are configured for "open-system"
authentication and will authenticate any station.)
20
Deauthentication
Deauthentication terminates an authenticated relationship. Because authentication is needed
before network use is authorized, a side effect of deauthentication is termination of any
current association.
Privacy
Strong physical controls can prevent a great number of attacks on the privacy of data in a
wired LAN. Attackers must obtain physical access to the network medium before attempting
to eavesdrop on traffic. On a wired network, physical access to the network cabling is a subset
of physical access to other computing resources. By design, physical access to wireless
networks is a comparatively simpler matter of using the correct antenna and modulation
methods. To offer a similar level of privacy, 802.11 provides an optional privacy service
called Wired Equivalent Privacy (WEP). WEP is not ironclad security—in fact, it has been
proven recently that breaking WEP is easily within the capabilities of any laptop (for more
information, see Chapter 5
). Its purpose is to provide roughly equivalent privacy to a wired
network by encrypting frames as they travel across the 802.11 air interface. Depending on
your level of cynicism, you may or may not think that WEP achieves its goal; after all, it's not
that hard to access the Ethernet cabling in a traditional network. In any case, do not assume
that WEP provides more than minimal security. It prevents other users from casually
appearing on your network, but that's about all.
[5]
[5]
One of O'Reilly's offices had a strange situation in which apparent "interlopers"
appeared on the network. They eventually discovered that their ESS overlapped
a company in a neighboring office building, and "foreign" laptops were simply
associating with the access point that had the strongest signal. WEP solves
problems like this but will not withstand a deliberate attack on your network.
MSDU delivery
Networks are not much use without the ability to get the data to the recipient. Stations provide
the MAC Service Data Unit (MSDU) delivery service, which is responsible for getting the
data to the actual endpoint.
Table 2-1. Network services
Service
Station or distribution
service?
Description
Distribution Distribution
Service used in frame delivery to determine
destination
address in infrastructure networks
Integration Distribution
Frame delivery to an IEEE 802 LAN outside the wireless
network
Association Distribution
Used to establish the AP which serves as the gateway to a
particular mobile station
Reassociation Distribution
Used to change the AP which serves as the gateway to a
particular mobile station
Disassociation Distribution Removes the wireless station from the network
Authentication Station Establishes identity prior to establishing association
Deauthentication Station
Used to terminate authentication, and by extension,
association
Privacy Station Provides protection against eavesdropping
MSDU delivery Station Delivers data to the recipient
剩余334页未读,继续阅读
zhoujiajia
- 粉丝: 1
- 资源: 16
上传资源 快速赚钱
 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助

最新资源
- JavaScript实现的高效pomodoro时钟教程
- CMake 3.25.3版本发布:程序员必备构建工具
- 直流无刷电机控制技术项目源码集合
- Ak Kamal电子安全客户端加载器-CRX插件介绍
- 揭露流氓软件:月息背后的秘密
- 京东自动抢购茅台脚本指南:如何设置eid与fp参数
- 动态格式化Matlab轴刻度标签 - ticklabelformat实用教程
- DSTUHack2021后端接口与Go语言实现解析
- CMake 3.25.2版本Linux软件包发布
- Node.js网络数据抓取技术深入解析
- QRSorteios-crx扩展:优化税务文件扫描流程
- 掌握JavaScript中的算法技巧
- Rails+React打造MF员工租房解决方案
- Utsanjan:自学成才的UI/UX设计师与技术博客作者
- CMake 3.25.2版本发布,支持Windows x86_64架构
- AR_RENTAL平台:HTML技术在增强现实领域的应用
安全验证
文档复制为VIP权益,开通VIP直接复制
 信息提交成功
信息提交成功