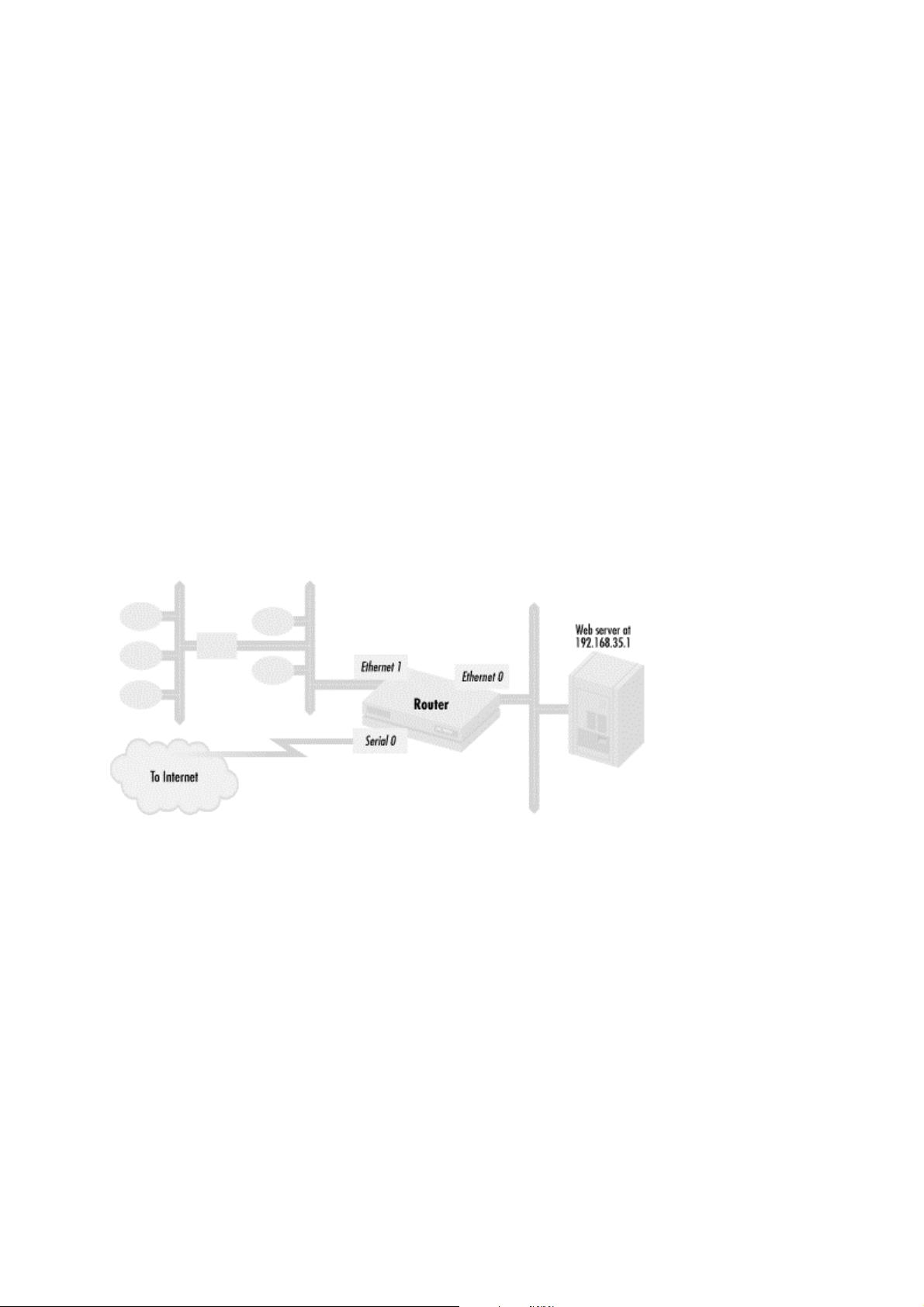
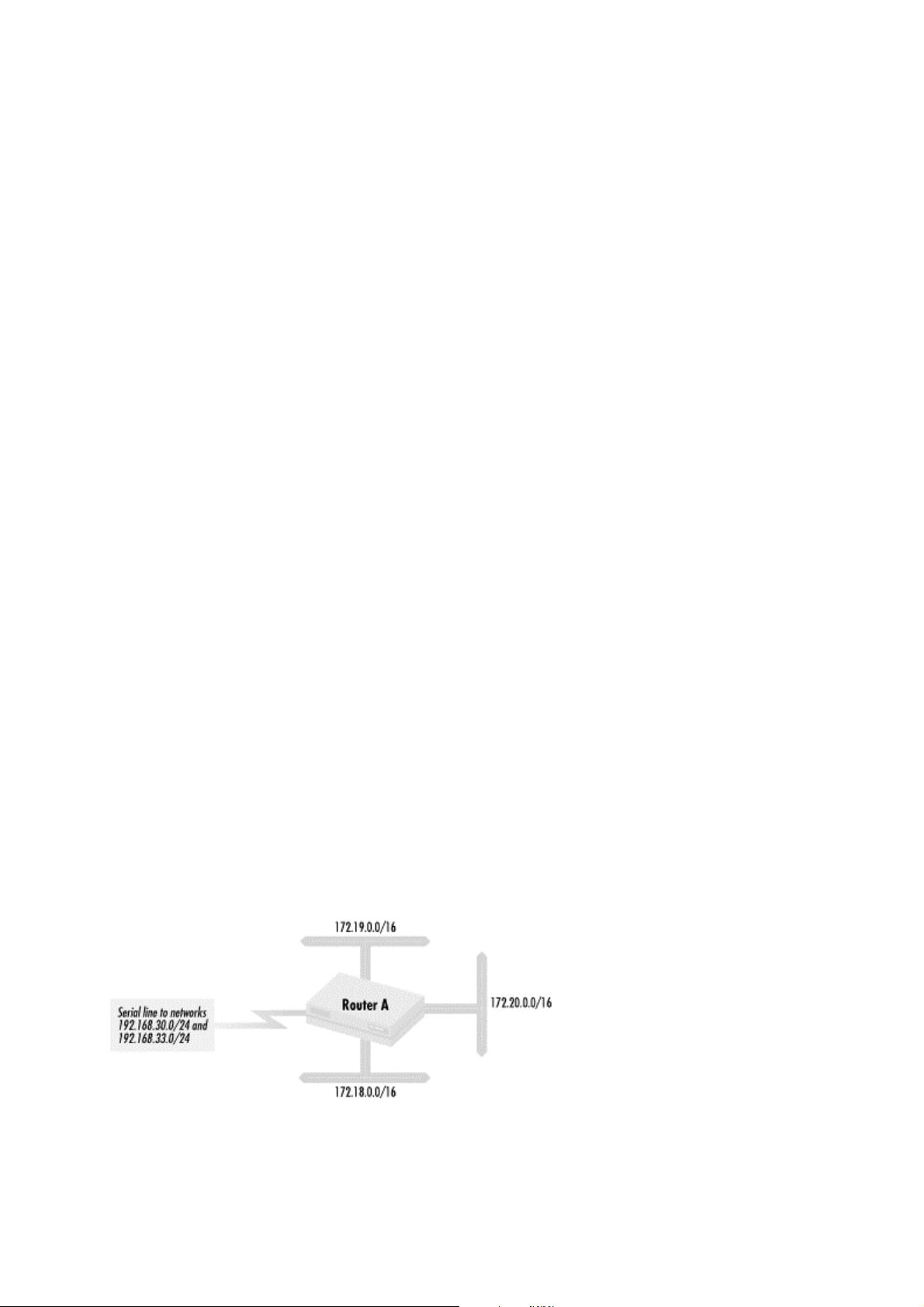
Cisco IOS Access lists
Page 16
So far, I have focused only on policy sets, so you might be wondering how Cisco access lists
come into the picture. The function of Cisco access lists is to hold the specification of a policy
set. The term "access list" is somewhat deceptive in that it implies only a security function.
Though access lists are indeed used for security functions, they are properly understood as a
general mechanism used by Cisco routers to specify a set of network objects subject to policy.
Access lists are built of access list entries, which directly correspond with policy set entries.
The framework described here is useful because it helps us think about network policies in
ways that are almost directly translatable into Cisco access lists. In future chapters, I will
almost always define network policies in terms of a policy set and a policy imposed upon it.
1.2 The policy toolkit
What do we do with our policy sets once we define them? How can we use those policy sets
to prevent the described scenarios from happening? This section talks about the "policy
toolkit," a set of four "tools" that are general techniques for manipulating policy sets.
As we know, policy sets can be described as the "what" of a policy. The policy tools fit into
our conceptual framework as the "how." Once we define a policy set, we must do something
with it to implement a policy. There are four kinds of tools we can use with policy sets to
implement network policy. These tools control the following:
•
Router resources
• Packets passing through the router
•
Routes accepted and distributed
• Routes based on characteristics of those routes
It may not be obvious why a network administrator would use these tools. To understand this,
think about the functions that a router performs in a network. First, in many ways, a router
functions like a host in that there are certain services it provides—logins, network time,
SNMP MIB data. These are router resources that a network administrator can control.
Secondly, a router's key function is to forward packets from one network interface to another.
Hence the network administrator can do packet filtering, i.e., can control the packets passing
through the router. The last key function of a router is to accept and distribute routing
information. Thus, there must be a way to control routes that are accepted and distributed. The
most common way to do this is with the routes themselves: by filtering routes based on their
network numbers. A second, more complex way to filter routes is to use another characteristic
of the routes, like last hop or some other arbitrary route attribute. It can be argued that all
route filtering is done based on some route characteristic, be it the network number or some
other attribute, but we keep them in separate categories because route filtering based on route
characteristics tends to be much more complex than filtering using network numbers.
Controlling routes based on route properties also tends to use radically different access list
constructs.
For each of the four policy tools, I describe the typical policy set and provide an example of
how the tool is used. I'll come back to these examples in later chapters when I show how to
build and use access lists.