Chapter 3. SELinux Contexts
8
is the same as s0). Each level is a sensitivity-category pair, with categories being optional. If there
are categories, the level is written as sensitivity:category-set. If there are no categories, it is written
as sensitivity.
If the category set is a contiguous series, it can be abbreviated. For example, c0.c3 is the same
as c0,c1,c2,c3. The /etc/selinux/targeted/setrans.conf file maps levels (s0:c0)
to human-readable form (ie. CompanyConfidential). Do not edit setrans.conf with a text
editor: use semanage to make changes. Refer to the semanage(8) manual page for further
information. In Red Hat Enterprise Linux, targeted policy enforces MCS, and in MCS, there is
just one sensitivity, s0. MCS in Red Hat Enterprise Linux supports 1024 different categories: c0
through to c1023. s0-s0:c0.c1023 is sensitivity s0 and authorized for all categories.
MLS enforces the Bell-La Padula Mandatory Access Model
1
, and is used in Labeled Security
Protection Profile (LSPP) environments. To use MLS restrictions, install the selinux-policy-mls
package, and configure MLS to be the default SELinux policy. The MLS policy shipped with
Red Hat Enterprise Linux omits many program domains that were not part of the evaluated
configuration, and therefore, MLS on a desktop workstation is unusable (no support for the X
Window System); however, an MLS policy from the upstream SELinux Reference Policy
2
can be
built that includes all program domains.
3.1. Domain Transitions
A process in one domain transitions to another domain by executing an application that has the
entrypoint type for the new domain. The entrypoint permission is used in SELinux policy, and
controls which applications can be used to enter a domain. The following example demonstrates a
domain transition:
1. A user wants to change their password. To do this, they run the passwd application. The /usr/
bin/passwd executable is labeled with the passwd_exec_t type:
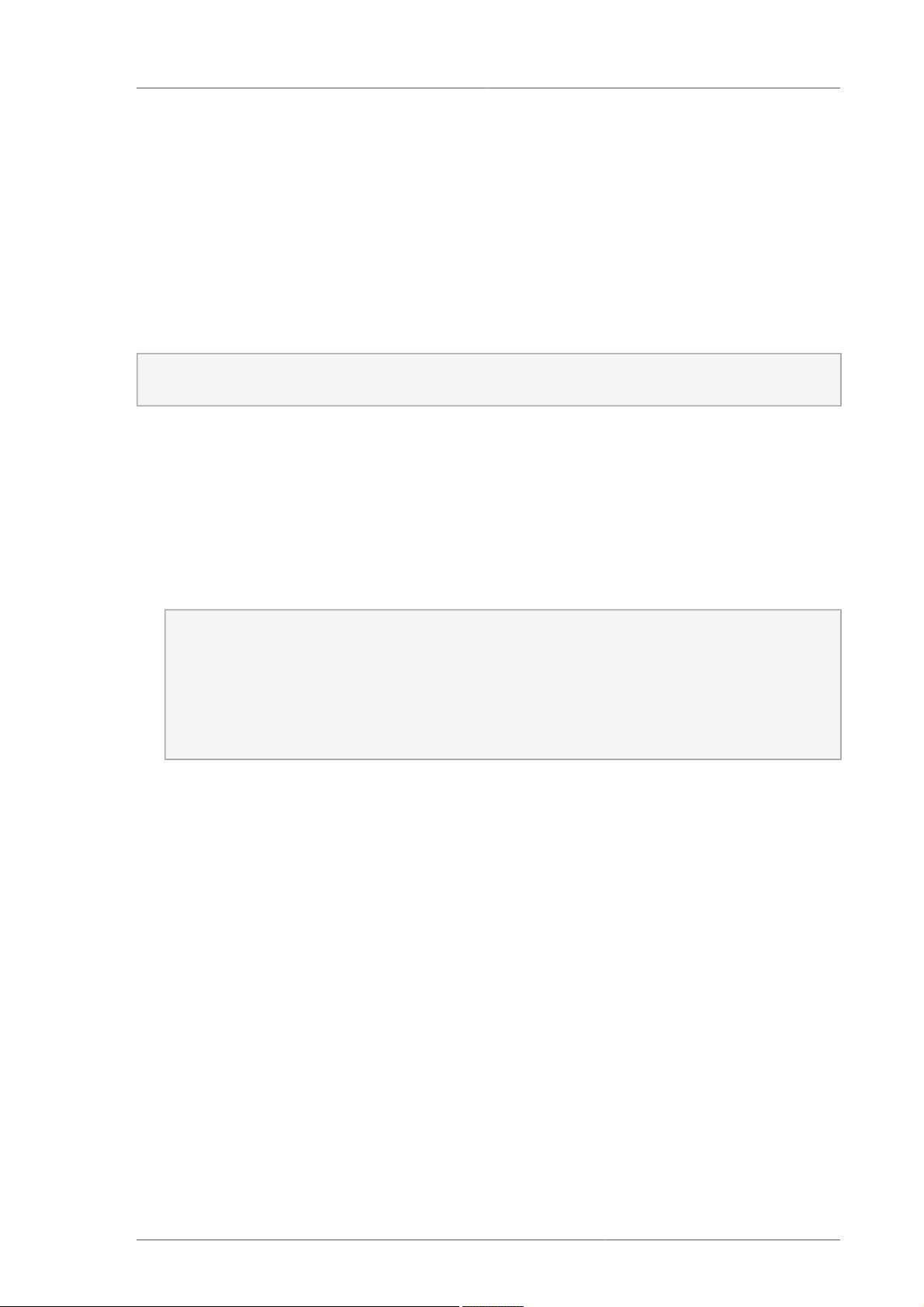
$ ls -Z /usr/bin/passwd
-rwsr-xr-x root root system_u:object_r:passwd_exec_t:s0 /usr/bin/passwd
The passwd application accesses /etc/shadow, which is labeled with the shadow_t type:
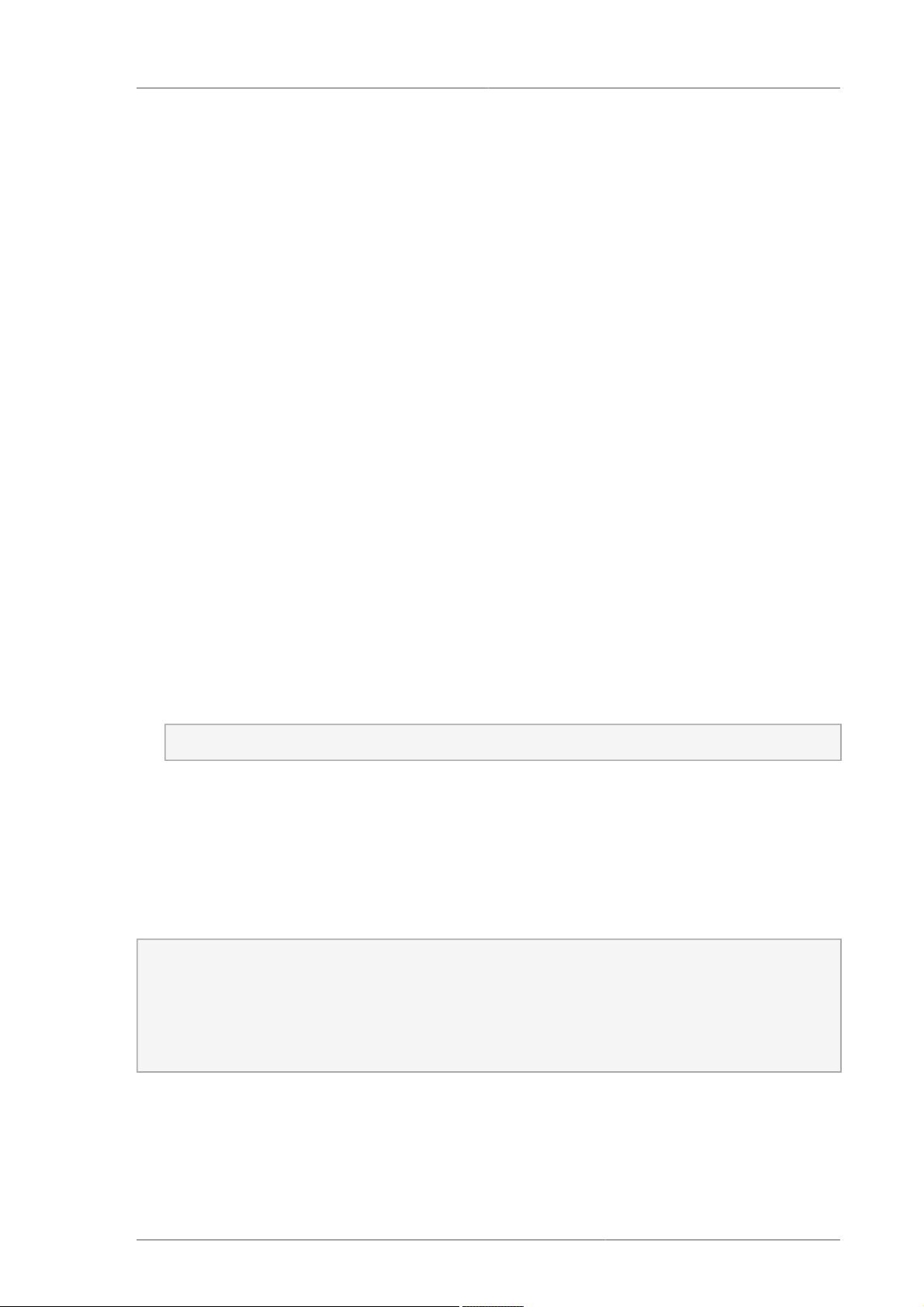
$ ls -Z /etc/shadow
-r--------. root root system_u:object_r:shadow_t:s0 /etc/shadow
2. An SELinux policy rule states that processes running in the passwd_t domain are allowed to read
and write to files labeled with the shadow_t type. The shadow_t type is only applied to files that
are required for a password change. This includes /etc/gshadow, /etc/shadow, and their
backup files.
3. An SELinux policy rule states that the passwd_t domain has entrypoint permission to the
passwd_exec_t type.
4. When a user runs the /usr/bin/passwd application, the user's shell process transitions to the
passwd_t domain. With SELinux, since the default action is to deny, and a rule exists that allows
(among other things) applications running in the passwd_t domain to access files labeled with
the shadow_t type, the passwd application is allowed to access /etc/shadow, and update the
user's password.
1
http://en.wikipedia.org/wiki/Bell-LaPadula_model
2
http://oss.tresys.com/projects/refpolicy