Y. Zhang, J. Jiang and Y. Xiang et al. / Information Sciences xxx (xxxx) xxx 3
ARTICLE IN PRESS
JID: INS [m3Gsc; January 2, 2019;15:22 ]
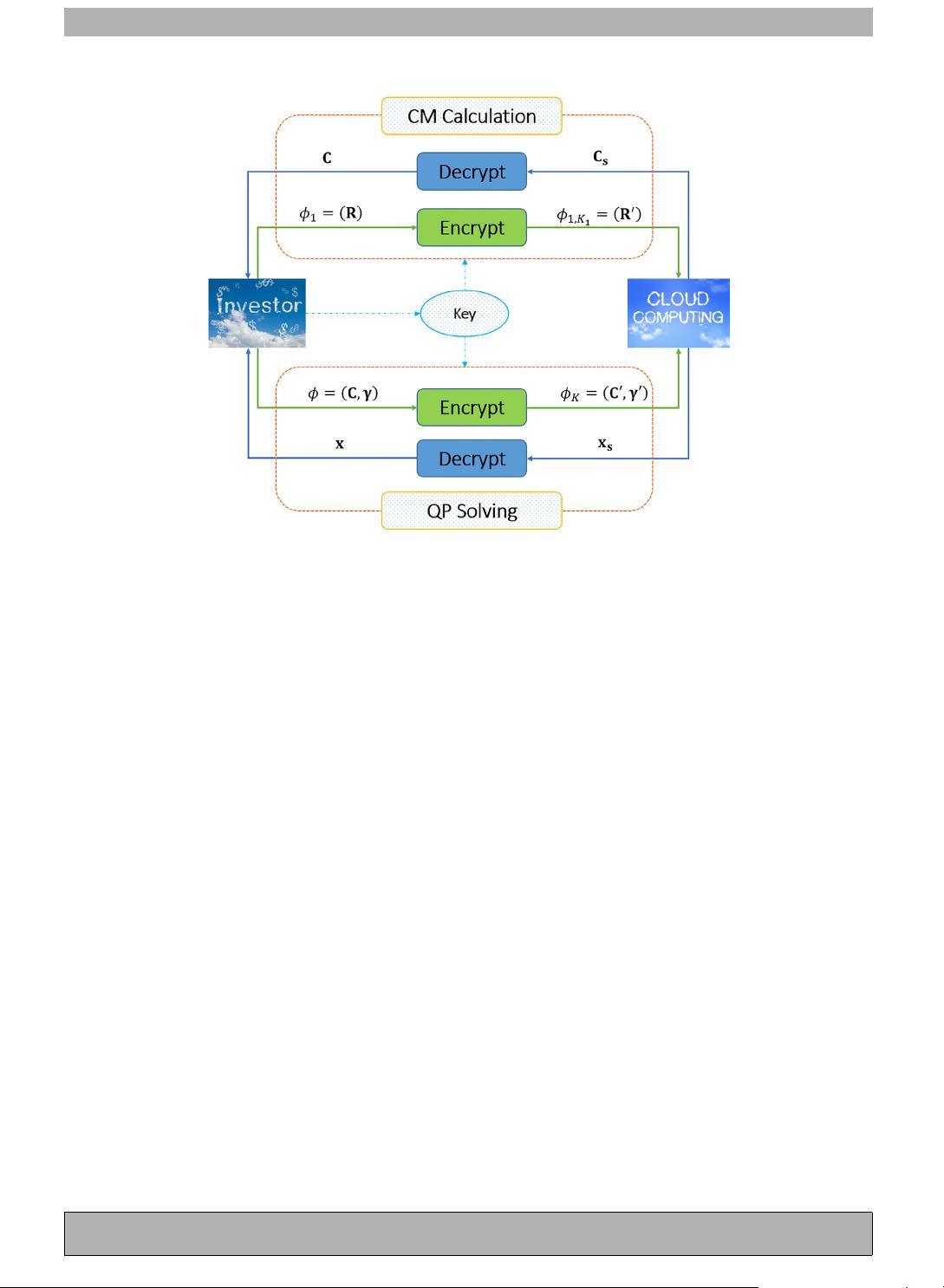
Fig. 1. The system model of MM outsourcing.
outsourcing algorithms for large-scale QR and LU factorizations
[24] . In addition, Domingo–Ferrer systematically investigated
how to exploit public clouds to calculate scalar products and matrix products on privacy-protected data [7] . The MM is not
involved in these existing works.
Our work has a connection with secure outsourcing related to equations such as linear equation, linear programming,
quadratic programming, convex optimization and linear regression. With the help of the iterative method that can be easily
implemented, Wang et al. realized a secure outsourcing for large-scale systems of linear equations to a public cloud [34,35] .
Likewise, they put forward the secure outsourcing of large-scale linear programming by employing a set of secret matrices
and vectors to hide the sensitive information [32,33] . These two kinds of outsourcing are further improved in [5] , in which
some special linear transformations are designed for linear equation solving without homomorphic encryptions and inter-
actions with the cloud, and a new standard natural form is proposed for linear programming solutions. Chen et al. used
the sparse matrix to outsource large-scale systems of linear equations for the first time, and this algorithm only requires
one-round communication, which avoids frequent interactions with the cloud [6] . Salinas et al. also exploited the sparsity
for linear equations with a lower computational complexity and a smaller number of input/output operations [28] . A novel
distributed outsourcing version in ad-hoc clouds was proposed in [30] , in which a robust consensus-based algorithm was
designed for distributively outsourcing linear algebraic equations into each cloud agent with guaranteed privacy. The case of
efficiently outsourcing large-scale linear regression was investigated in [4] , in which two protocols with different advantages
are constructed. Zhou and Li harnessed the public cloud to build a secure, verifiable, and efficient outsourcing of large-scale
quadratic programming [48] . Xu et al. suggested the case of convex optimization with an efficient integrity verification based
on the inherent structure of the optimization problems [40] . In addition, Liao et al. aimed at large-scale convex separable
programming and developed an efficient outsourcing framework based only on arithmetic operations [16] . These works did
not consider the privacy-preserving outsourcing of MM.
The proposed scheme is similar to some privacy-preserving applications. In the image field, compressive sensing can
offer high-efficiency lar ge-scale image data sampling, but the reconstruction complexity is extremely large. Thus, securely
outsourcing the image-reconstruction service to the public cloud was studied in [36] . Analogously, Hu et al. established
an outsourcing framework for image-reconstruction and identity-authentication services by integrating compressive sens-
ing and optimization outsourcing [10] . For more efficient reconstruction, the image-sparse reconstruction service was out-
sourced in parallel multi-clouds [47] , which effectively protects the support set based on the parallel compressive sensing
theories [8,41,45] . Later, this sparse reconstruction service was extended to the sparse robustness decoding service when
two-dimensional signals are transmitted over a lossy channel with packet loss [46] . In a smart grid field, some grid data
must be stored and managed by the cloud computing resources, and these data are often highly confidential; thus, Sarker
et al. developed an economic dispatch linear programming with applications in grid data management [29] . In the numer-
ical computation field, Liu et al. presented some privacy-preserving computation schemes in terms of floating-point num-
bers [20] , public data [21] , and rational numbers [17] . Furthermore, they extended these numerical computations to some
Please cite this article as: Y. Zhang, J. Jiang and Y. Xiang et al., Cloud-assisted privacy-conscious large-scale Markowitz
portfolio, Information Sciences, https://doi.org/10.1016/j.ins.2018.12.055









