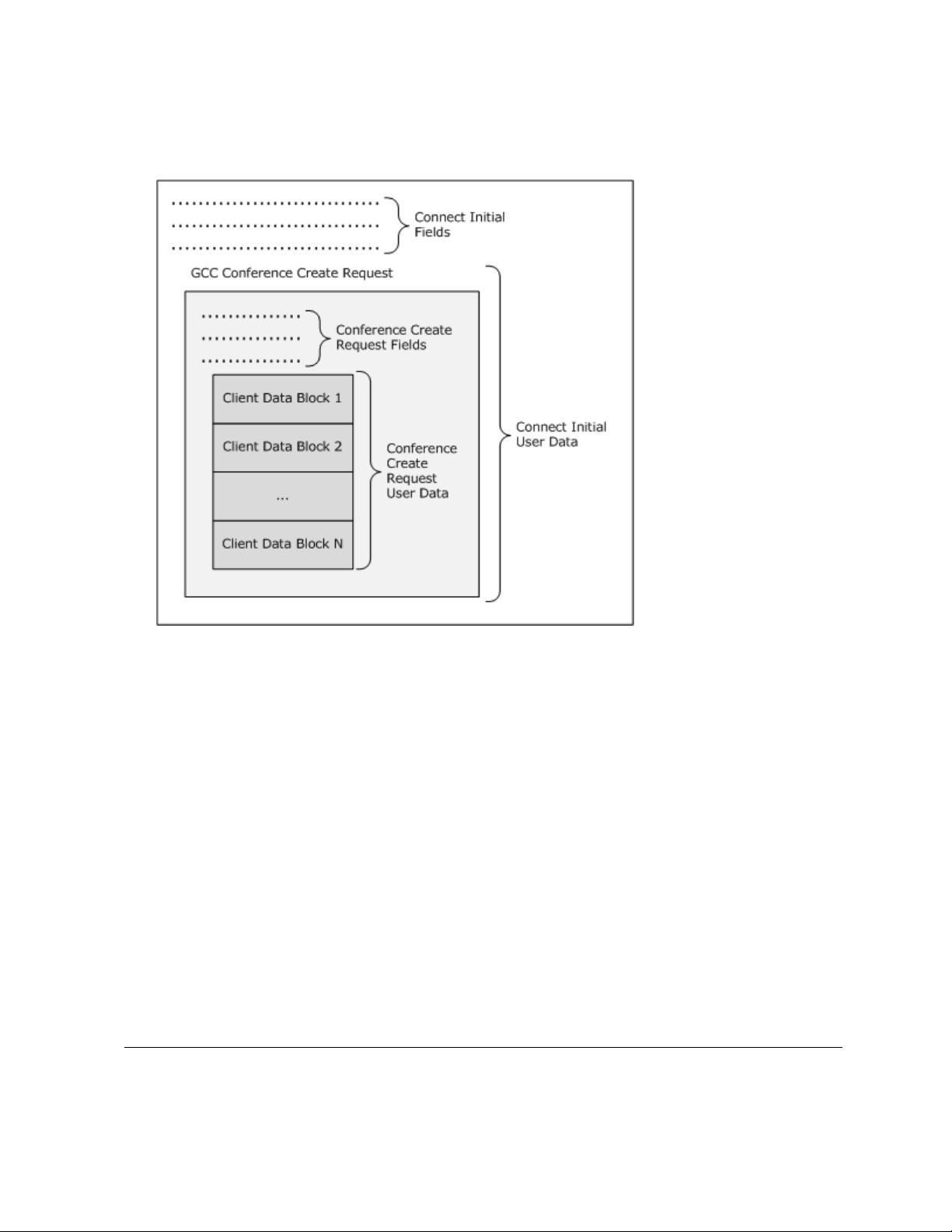
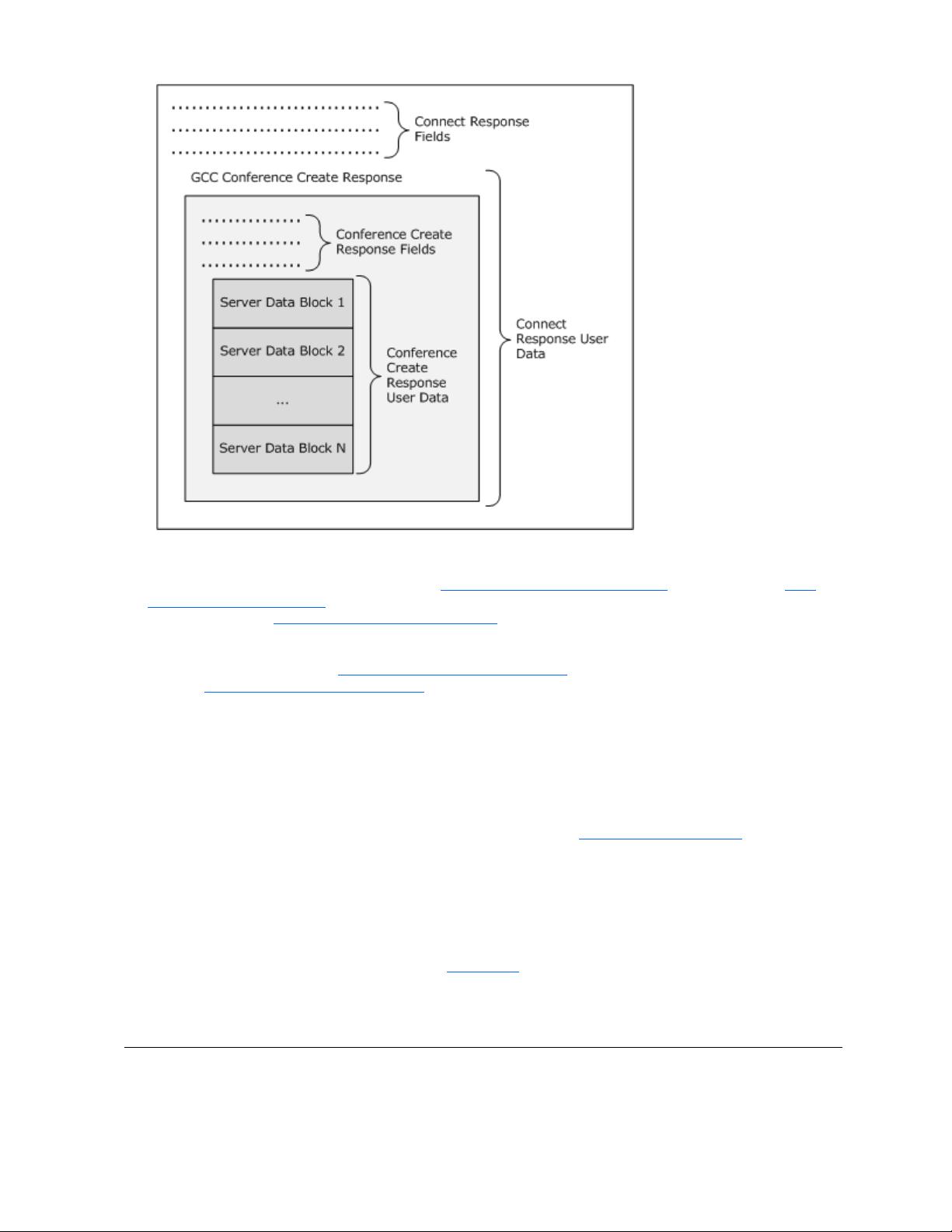
19 / 378
[MS-RDPBCGR] — v20090223
Remote Desktop Protocol: Basic Connectivity and Graphics Remoting Specification
Copyright © 2009 Microsoft Corporation.
Release: Monday, February 23, 2009
client traffic may not always be encrypted, while client-to-server traffic will always be encrypted
by Microsoft RDP implementations (encryption of licensing PDUs is optional, however).
5. Secure Settings Exchange: Secure client data (such as the username, password, and auto-
reconnect cookie) is sent to the server using the Client Info PDU.
6. Licensing: The goal of the licensing exchange is to transfer a license from the server to the client.
The client should store this license and on subsequent connections send the license to the server
for validation. However, in some situations the client may not be issued a license to store. In
effect, the packets exchanged during this phase of the protocol depend on the licensing
mechanisms employed by the server. Within the context of this document, it is assumed that the
client will not be issued a license to store. For details regarding more advanced licensing
scenarios that take place during the Licensing Phase, see [MS-RDPELE].
7. Capabilities Exchange: The server sends the set of capabilities it supports to the client in a
Demand Active PDU. The client responds with its capabilities by sending a Confirm Active PDU.
8. Connection Finalization: The client and server send PDUs to finalize the connection details. The
client-to-server and server-to-client PDUs exchanged during this phase may be sent concurrently
as long as the sequencing in either direction is maintained (there are no cross-dependencies
between any of the client-to-server and server-to-client PDUs). After the client receives the Font
Map PDU it can start sending mouse and keyboard input to the server, and upon receipt of the
Font List PDU the server can start sending graphics output to the client.
Besides input and graphics data, other data that can be exchanged between client and server after
the connection has been finalized includes connection management information and virtual channel
messages (exchanged between client-side plug-ins and server-side applications).
1.3.1.2 Security-Enhanced Connection Sequence
The RDP Connection Sequence does not provide any mechanisms which ensure that the identity of
the server is authenticated, and as a result it is vulnerable to man-in-the-middle attacks (these
attacks can compromise the confidentiality of the data sent between client and server).
The goal of the Security-Enhanced Connection Sequence is to provide an extensible mechanism
within RDP so that well-known and proven security protocols (such as Secure Socket Layer (SSL) or
Kerberos) can be used to fulfill security objectives and to wrap RDP traffic. There are two variations
of the Security-Enhanced Connection Sequence. The negotiation-based approach aims to provide
backward-compatibility with previous RDP implementations, while the Direct Approach favors more
rigorous security over interoperability.
Negotiation-Based Approach: The client advertises the security packages which it supports (by
appending a negotiation request structure to the X.224 Connection Request PDU and the server
selects the package to use (by appending a negotiation response structure to the X.224 Connection
Confirm PDU). After the client receives the X.224 Connection Confirm PDU the negotiated security
package is executed and used to secure all subsequent RDP traffic.
Direct Approach: Instead of negotiating a security package, the client and server immediately
execute a predetermined security protocol (for example, the CredSSP Protocol) prior to any RDP
traffic being exchanged on the wire. This approach results in all RDP traffic being secured using the
hard-coded security package. However, it has the disadvantage of not working with servers that
expect the connection sequence to be initiated by an X.224 Connection Request PDU.
For more details about Enhanced RDP Security, see section 5.4.