Detecting App-DDoS Attacks Based on Marking Access and d-SVDD
LI Jin-ling, WANG Bin-qiang
National Digital Switching System Engineering & Technological R&D Center
Zhengzhou , China
zifenglingsworld@163.com
Abstract---In order to enhance the extensibility of current
attack feature extracted and detection means for
App-DDoS(Application Layer Distributed Denial of Service,
App-DDoS)attacks, a novel feature extracted method based
on marking access and a new detection algorithm named
d-SVDD are proposed. After expressing kinds of App-DDoS
attacks as characteristic vectors by access marked strategy
and feature extracted strategy, d-SVDD algorithm is used
for secondary classification and detection of pre-set area
around decision boundary based on SVDD. It is proved by
experiments that the proposed feature extracted and
detection means can realize effective detection for kinds of
App-DDoS attacks, both have satisfying time, space and
extensibility performance.
Keywords-App-DDoS attack; Marking access; d-SVDD;
Anomaly detection
I. INTRODUCTION
Being different only in purpose from normal behavior,
App-DDoS attacks can easily cross the low-level defense
systems for traditional DDoS attacks, along with the fact
that dealing with a high-level application request is much
more complex, finding out effective detection and defense
means for App-DDoS attacks becomes more and more
important
[1]
.
Currently, most detection methods for App-DDoS
attacks are mainly based on behavior analysis
[2]
and log
analysis
[3]
. One typical detection method based on users’
browsing information detects HTTP flooding attacks
according to users’ browsing order and the relationship
between view time and page information
[4]
. Another
detection method proposed by Xie Yi and Yu Shunzheng
introduces HsMM model to detection algorithm
[5][6]
. In
literature [7], App-DDoS attacks are divided into three
categories by session parameter: request flooding attacks,
asymmetric workload attacks and repeated one-shot
attacks. According to this classification, a session
suspicious degree model is proposed for anomaly
detection and filtering.
After analyzing the detection methods above, we can
conclude: 1) App-DDoS attacks have lots of different
types because of the differences among application layer
services and protocols, while means based on behavior
analysis and log analysis only consider Web server mostly,
the extracted characters have poor extensibility; 2)
Anomaly detection methods deeply depend on extracted
characters, so the poor extensibility of characters directly
affects the extensibility of detection methods.
In order to enhance the extensibility of extracted
characters and corresponding detection algorithms,
achieve effective detection for various attacks, a novel
feature extracted method based on marking access and a
new detection algorithm named d-SVDD are proposed in
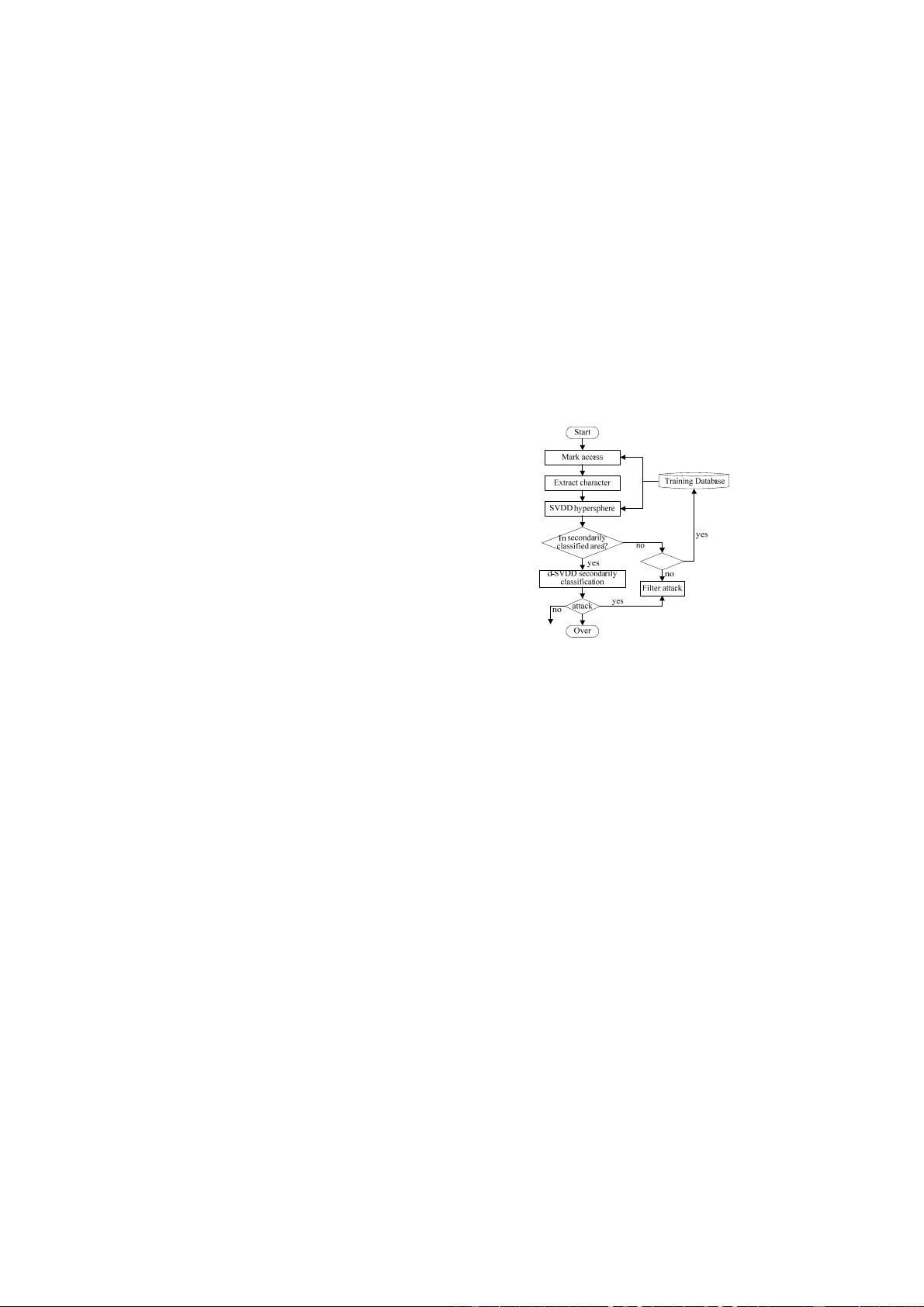
this paper. The flow chart of such detection algorithm is
shown in Figure 1.
i
dR<
Figure 1. The flow chart of detection algorithm
The detection algorithm is divided into training and
detection phases in detail. In training phase, mark normal
users’ access behavior with no marking strategy firstly,
and then set marking period
t and average interval
between consecutive access stamps
d
t
according to the
initial marked results. After that process the initial access
stamps with marking strategy. When all of these are
completed, feature extracted method is applied to obtain
effective detection characters, and SVDD algorithm is
used to get normal users’ SVDD hypersphere. All of the
results will be saved in training database and get fully
prepared for the next detection phase.
II. FEATURE EXTRACTED METHOD BASED ON
MARKING ACCESS
In detection phase, every user accessing to the server
will be marked with marking strategy, including marking
access time and access page. According to different
servers, different requests will be selected to mark. For
example, HTTP GET requests will be marked in attacks
against Web server, while DNS requests will be marked
during attacks against DNS server.
Take attacks against Web server for example, access
time marked method adopts strategy as follow: if the
current stamp interval
'
d
t is less than
d
t
, 1 will be assigned
to current stamp, otherwise 0 will be assigned. Access
page is marked using the following strategy: if the page
requested by current user doesn’t exist in protected Web
Proceedings of the 2nd International Symposium on Computer, Communication, Control and Automation (ISCCCA-13)
Published by Atlantis Press, Paris, France.
© the authors, 2013
0728









