162 IEEE TRANSACTIONS ON NETWORK AND SERVICE MANAGEMENT, VOL. 17, NO. 1, MARCH 2020
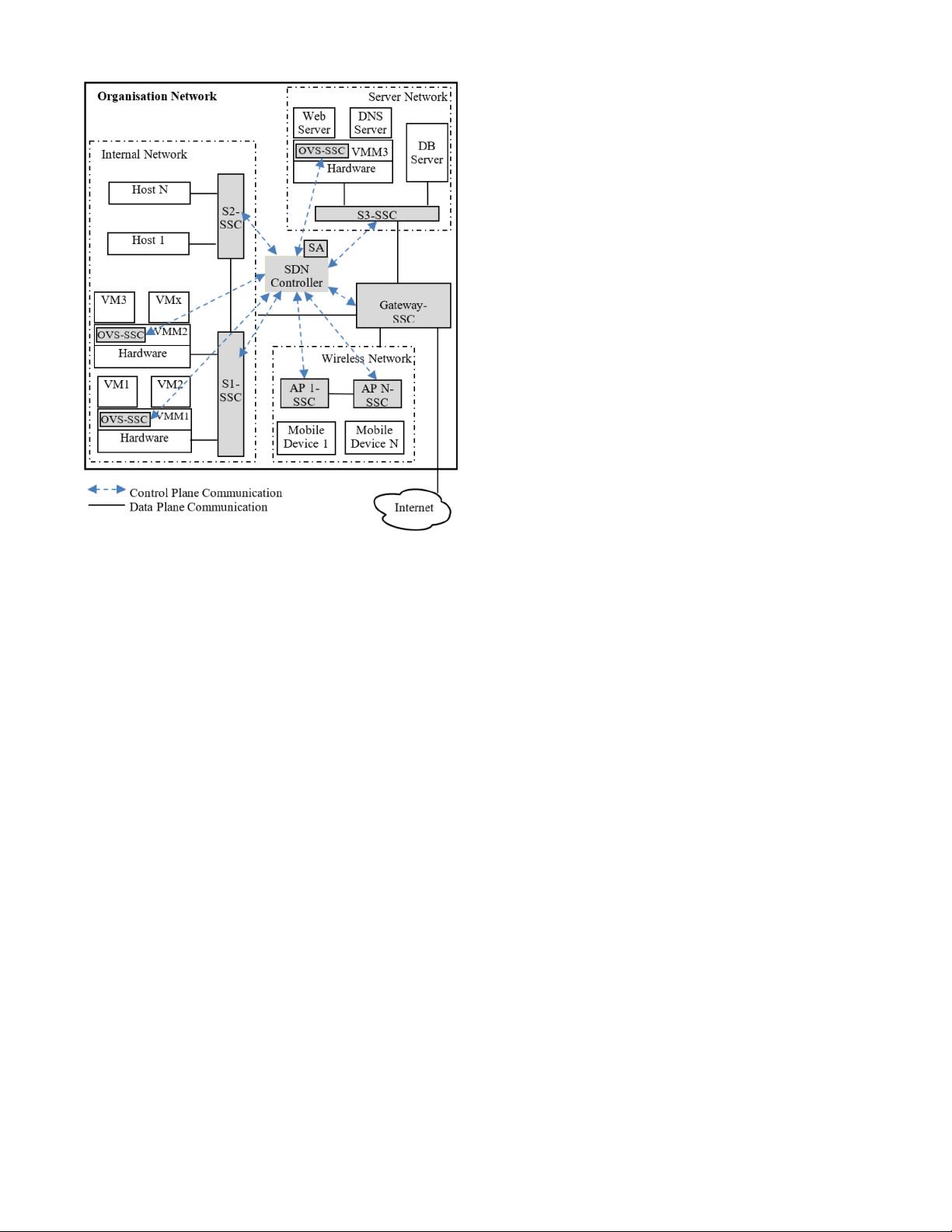
Fig. 2. SDN Environment.
II. ATTACKER MODEL
Consider an SDN environment shown in Figure 2 with
heterogeneous devices such as client and server machines,
and wireless mobile devices. The client and server machines
are either physical hosts or implemented as virtual machines
(VMs) running on a hypervisor or virtual machine monitor
(VMM) [16] based system. A VMM is an additional software
layer that has complete control over the physical resources
underneath and enables to run multiple VMs on a scalable
computer. The hosts are connected to the Internet using a
gateway/switch.
The SDN Controller enables programming the networking
devices and establishes routes for communication between the
hosts. For example, the Controller in Figure 2 configures the
Flow Tables in switches S2, S1 and the OVS in VMM1 to
enable communication between Host 1 and VM1. The switches
can be physical or virtual devices and can have any function-
ality from layer 2 to 7 in the OSI model. For example, client
and server machines can be connected using physical switches;
VMs hosted on the VMM are connected using the virtual
Open vSwitch (OVS) based on OpenFlow. Hence depending
on the functionality supported by a switch, appropriate secu-
rity policies can be enforced in that switch. For example, a
layer 2 device can enforce security mechanisms based on the
MAC protocol values, whereas layer 3 devices can have secu-
rity mechanisms on IP protocol values, and layer 7 devices can
enforce application level security policies, and virtual switches
can use introspection to monitor the internal state of the virtual
machines in their enforcement of security policies.
The focus of this paper is on the attacker model where the
goal of the attacker is to exploit the weaknesses in the end
hosts to compromise them (and turn them malicious) and make
use of the compromised hosts to generate attacks. As network
systems are ofen large and dynamic, there exist several oppor-
tunities for an attacker to compromise some system within an
organisation’s network and then use the compromised system
to access sensitive information, inject malicious messages into
the network and spread the attacks. There is an ever increas-
ing number of attacks including zero day attacks for which
no solutions are previously known (e.g., no software patches
exist) at the time of the attack. Although such attacks are not
specific to SDNs, there is a need to deal with such attacks in
SDNs just like in any network system.
Our proposed security solution is aimed at dealing with the
following set of attacks in a SDN environment.
• Flooding attacks from malicious end hosts: Our security
solution aims is to protect the switches and the SDN
Controller from flooding attacks from malicious end hosts
such as in [17]. One of the challenges with securing the
Controller is that it has to be accessible to the users and
end host applications while at the same time protecting
the Controller from flooding attacks from such end hosts.
For example, the malicious hosts can directly flood the
Controller and/or the switches by using their address as
the destination address. This can happen in the SDN as
follows: The end hosts use intent messages in SDN for
conveying the specific flow requirements. Since all the
intent messages will be destined to the Controller, a mali-
cious end host can obtain the IP address of the Controller
by analysing the intent messages and then use this IP
address for flooding the Controller. The end hosts can
also perform a traceroute to obtain the IP addresses of the
switches in the network and use them to generate flooding
attacks on the switches. The malicious end hosts can also
indirectly flood the Controller and the switches by gen-
erating several new flow requests to other end hosts with
minor variations in the TCP/IP header values in such a
way that it will not match with the flow tables records in
the switches. This will result in all the flow requests being
forwarded to the SDN Controller for making the routing
decision as a new flow request. This will in turn cause
flooding of the switch that is connected to the end host
and subsequently flood the Controller as well, impacting
on the availability of the complete network.
• Injecting false information or tampering information by
malicious end hosts: Malicious end hosts can also inject
false messages or tamper with messages in the SDN. For
instance, [8], [13] showed how malicious messages with
spoofed addresses can be used to exploit implementa-
tion vulnerabilities in a SDN Controller to effectively
poison the network topology information, which is a
fundamental building block for topology-aware SDN
applications. Attackers can use these techniques to mis-
lead the Controller services and applications and achieve
man-in-the-middle as well as denial of service attacks.
Furthermore, the study in [8] confirms that several of the
major SDN Controllers are vulnerable to such attacks.
Furthermore, often there will be a need to contain the spread
of attacks by isolating malicious end hosts as there may be
Authorized licensed use limited to: University of Science & Technology of China. Downloaded on November 29,2020 at 11:49:18 UTC from IEEE Xplore. Restrictions apply.









