Fundamentals
[ 6 ]
Vulnerability Assessment and
Penetration Testing
Vulnerability Assessment (VA) and Penetrating Testing (PT or PenTest) are
the most common types of technical security risk assessments or technical audits
conducted using different tools. These tools provide best outcomes if they are used
optimally. An improper conguration may lead to multiple false positives that may
or may not reect true vulnerabilities. Vulnerability assessment tools are widely used
by all, from small organizations to large enterprises, to assess their security status.
This helps them with making timely decisions to protect themselves from these
vulnerabilities. This book outlines the steps involved in conducting Vulnerability
Assessments and PenTests using Nessus. Nessus is a widely recognized tool for such
purposes. This section introduces you to basic terminology with reference to these
two types of assessments.
Vulnerability in terms of IT systems can be dened as potential weaknesses in
system/infrastructure that, if exploited, can result in the realization of an attack on
the system.
An example of a vulnerability is a weak, dictionary-word password in a system that
can be exploited by a brute force attack (dictionary attack) attempting to guess the
password. This may result in the password being compromised and an unauthorized
person gaining access to the system.
The word system in this book refers to any asset existing in an
information technology or non-information technology environment.
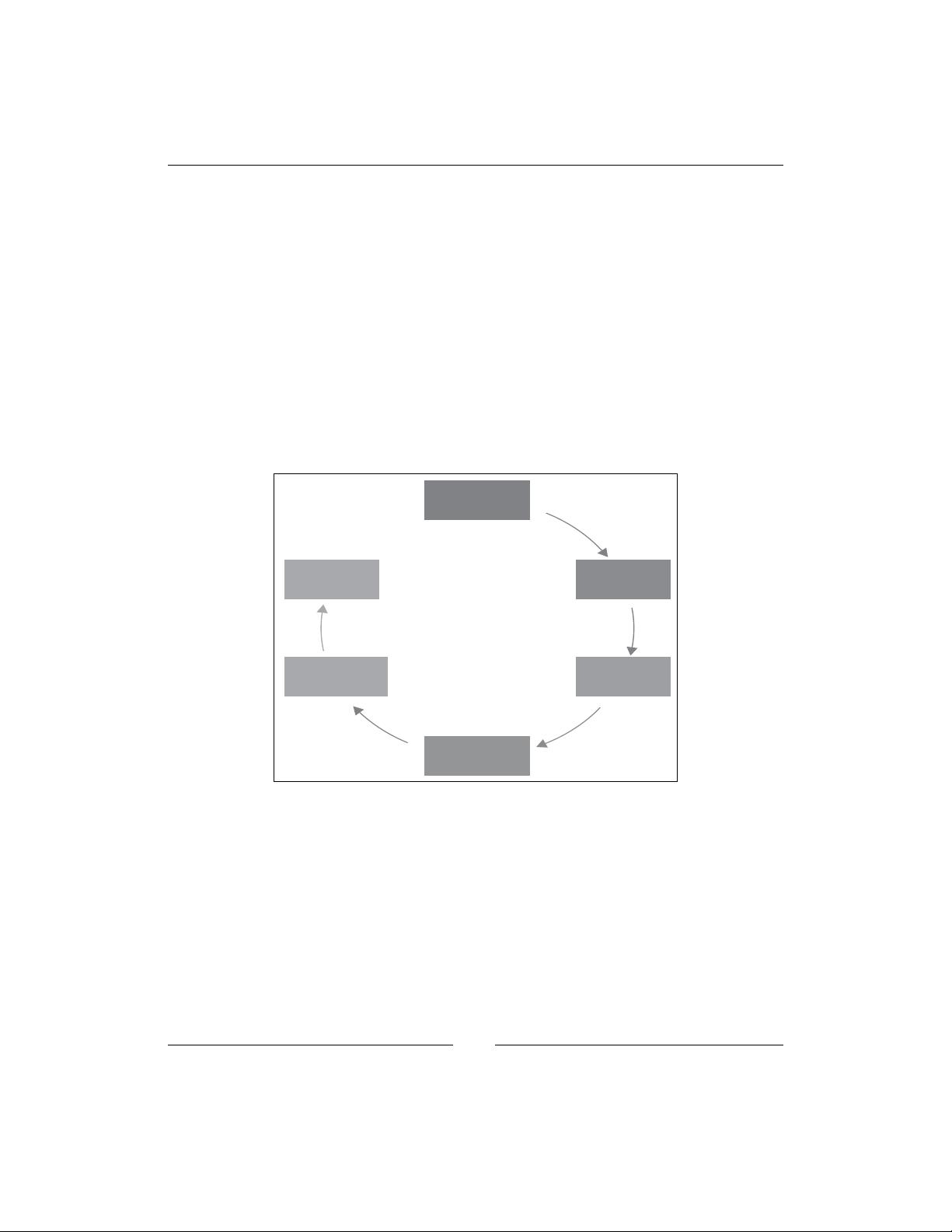
Vulnerability Assessment is a phase-wise approach to identifying the vulnerabilities
existing in an infrastructure. This can be done using automated scanning tools such
as Nessus, which uses its set of plugins corresponding to different types of known
security loopholes in infrastructure, or a manual checklist-based approach that uses
best practices and published vulnerabilities on well-known vulnerability tracking
sites. The manual approach is not as comprehensive as a tool-based approach and
will be more time-consuming. The kind of checks that are performed by
a vulnerability assessment tool can also be done manually, but this will take a lot
more time than an automated tool.
Penetration Testing has an additional step for vulnerability assessment, exploiting
the vulnerabilities. Penetration Testing is an intrusive test, where the personnel
doing the penetration test will rst do a vulnerability assessment to identify the
vulnerabilities, and as a next step, will try to penetrate the system by exploiting the
identied vulnerabilities.