a
re required to trust the machine and feel safe. In this
way, a thing might be a patient with a medical implant to
facilitate real-time monitoring in a healthcare application
or an accelerometer for movement attached to the cow
in a farm environment [26].
These things or devices in IoT include familiar
scannables and wearables and more complex systems
like home appliances, vehicles, and smart roads and
bridges. It is predicted that IoT will consist of 50 billion
connected devices by 2020 and that the worldwide IoT
market will be more than a $10 trillion industry. These
projections depict the possibility of a smarter, efficient
and safer world of inter-connected devices [27] while
some observers show concerns that the IoT represents
a darker world of surveillance, privacy and security
violations, and consumer lock–in. Attention-grabbing
headlines about the hacking of internet-connected
automobiles, surveillance concerns arising from voice
recognition features in “smart” TVs, and privacy fears
stemming from the potential misuse of IoT data have
captured public attention. This “promise vs. peril”
debate along with an influx of information though
popular media and marketing can make the IoT a
complex topic to understand [22].
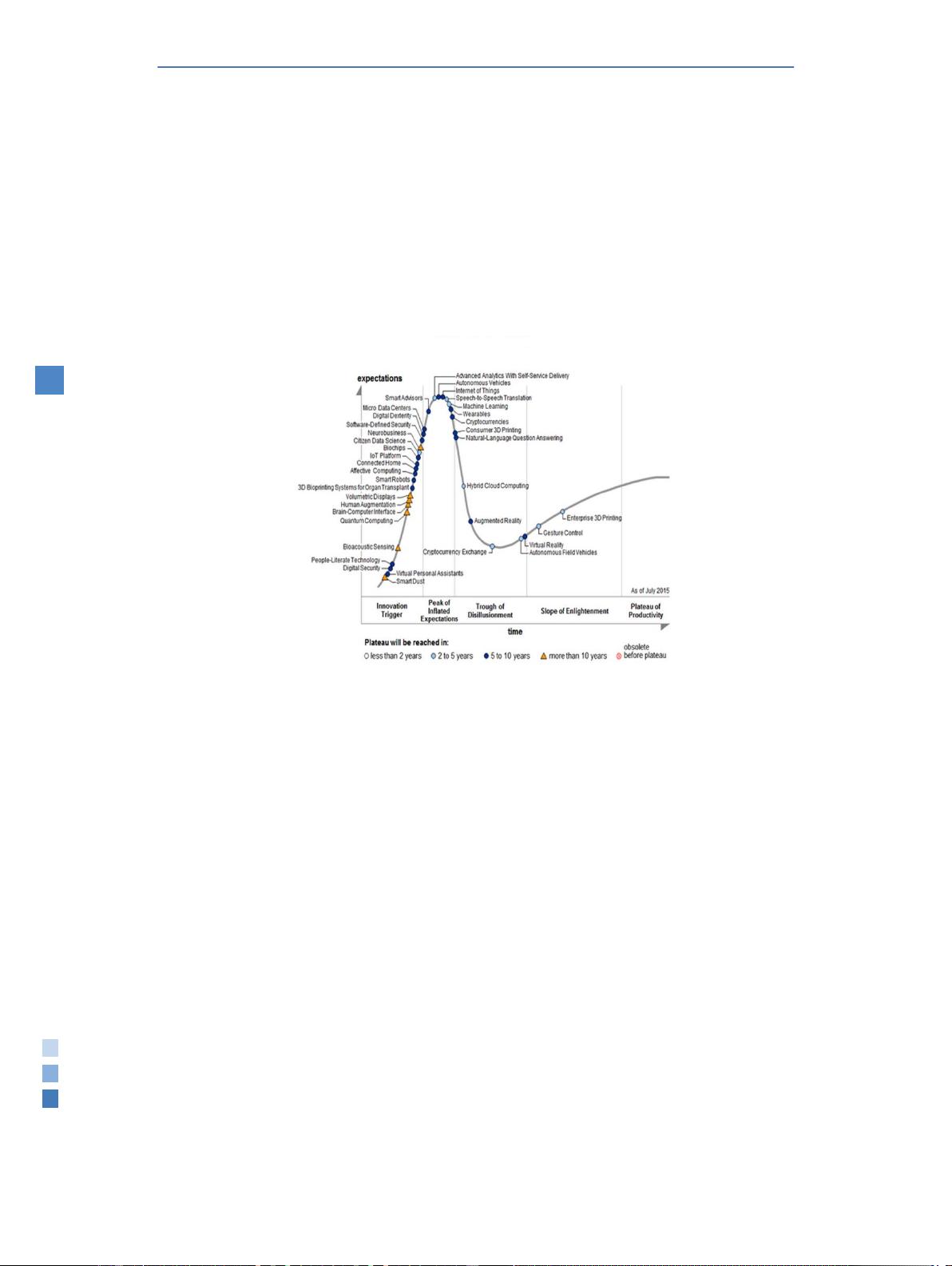
Fi
gure
1:
Hyper Cycle for Emerging Technologies, 2105[12]
G
arter’s Hype Cycle is a way to represent
e
mergence, adoption, maturity and impact on
a
pplications of specific technologies. The latest Gartner
H
ype Cycle for Emerging Technologies places it at the
p
eak. IoT has been identified as one of the emerging
te
chnologies as shown below in the Hype Cycle in
E
merging Technologies Report for the year 2015[28].
II.
S
e
curity for
I
n
ternet of
T
hi
ngs
I
f one thing can prevent the Internet of things
fr
om
tra
nsforming
the
way we live and work, it will be
a b
reakdown
in
security. While security considerations
a
re not new in the context of information technology, the
a
ttributes of many IoT implementations present new and
unique security challenges. Addressing these challen-
g
es and ensuring security in IoT products and services
mus
t be a fundamental priority. Users need to trust that
I
oT devices and related data services are secure from
vuln
erabilities, especially as this technology become
mo
re pervasive and integrated into our daily lives.
I
mportant challenge is the integration of security
me
chanisms and the user acceptance. User must feel
t
hat they control any information that is related to them
ra
ther than they feel they are being controlled by the
s
ystem. This integration generates new requirements,
n
ot been previously considered.
T
he interconnected nature of IoT devices means
t
hat every poorly secured device that is connected
o
nline potentially affects the security and resilience of
t
he Internet globally. This challenge is amplified by other
c
onsiderations like the mass-scale deployment of
ho
mogenous IoT devices, the ability of some devices to
a
utomatically connect to other devices, and the
lik
elihood of fielding these devices in unsecure
e
nvironments. As a matter of principle, developers and
us
ers of IoT devices and systems have a collective
ob
ligation to ensure they do not expose users and the
I
oT infrastructure itself to potential harm. Accordingly, a
c
ollaborative approach to security will be needed to
d
evelop effective and appropriate solutions to IoT
s
e
c
urity
challenges that are well suited to the scale and
com
plexity of the issues [22].
F
ull potential of the IoT depends on strategies
tha
t respect individual privacy choices across a broad
s
pectrum of expectations. The data streams and user
s
pecificity afforded by IoT devices can unlock incredible
a
nd unique value to IoT users, but concerns about
p
rivacy and potential harms might hold back full
Global Journal of Computer Science and Technology Volume XVI Issue VII Version I
2
Year
2016
(
)
©2
0
16 Global Journals Inc. (US)1
E
A R
eview on Internet of Things (Iot): Security and Privacy Requirements and the Solution Approaches









