8 MIPS32™ 4KEc™ Processor Core Datasheet, Revision 02.00
Copyright © 2001-2002 MIPS Technologies Inc. All rights reserved.
modes with the same capability. This is done by
introducing multiple copies of the GPRs, called shadow
sets, and allowing privileged software to associate a
shadow set with entry to kernel mode via an interrupt
vector or exception. The normal GPRs are logically
considered shadow set zero.
The number of GPR shadow sets is a build-time option on
the 4KEc core. Although Release 2 of the Architecture
defines a maximum of 16 shadow sets, the core allows one
(the normal GPRs), two, or four shadow sets. The highest
number actually implemented is indicated by the
SRSCtl
HSS
field. If this field is zero, only the normal GPRs
are implemented.
Shadow sets are new copies of the GPRs that can be
substituted for the normal GPRs on entry to kernel mode
via an interrupt or exception. Once a shadow set is bound
to a kernel mode entry condition, reference to GPRs work
exactly as one would expect, but they are redirected to
registers that are dedicated to that condition. Privileged
software may need to reference all GPRs in the register file,
even specific shadow registers that are not visible in the
current mode. The RDPGPR and WRPGPR instructions
are used for this purpose. The CSS field of the SRSCtl
register provides the number of the current shadow register
set, and the PSS field of the SRSCtl register provides the
number of the previous shadow register set (that which was
current before the last exception or interrupt occurred).
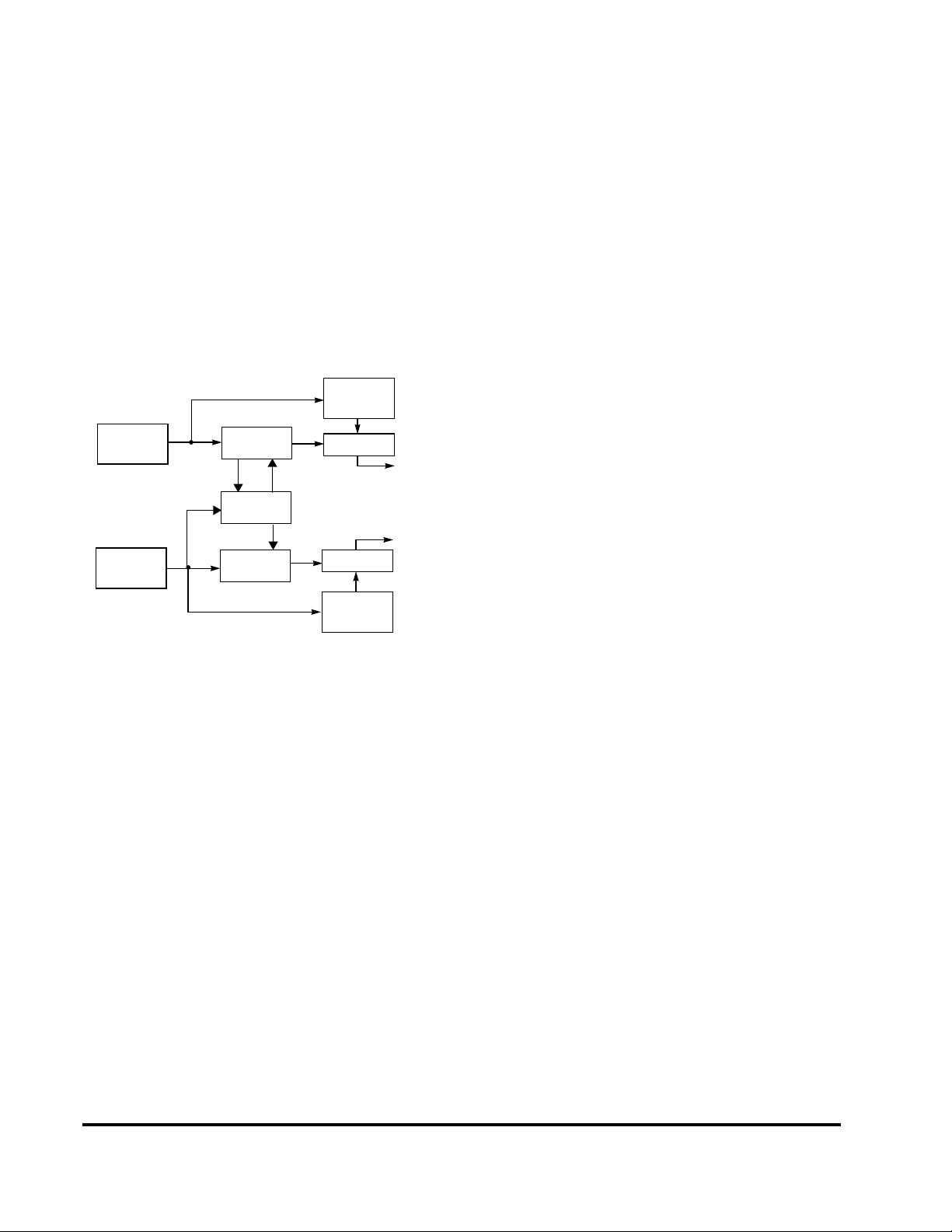
If the processor is operating in VI interrupt mode, binding
of a vectored interrupt to a shadow set is done by writing to
the SRSMap register. If the processor is operating in EIC
interrupt mode, the binding of the interrupt to a specific
shadow set is provided by the external interrupt controller,
and is configured in an implementation-dependent way.
Binding of an exception or non-vectored interrupt to a
shadowset is done by writing to the ESS field of the SRSCtl
register. When an exception or interrupt occurs, the value
of SRSCtl
CSS
is copied to SRSCtl
PSS
, and SRSCtl
CSS
is set
to the value taken from the appropriate source. On an
ERET, the value of SRSCtl
PSS
is copied back into
SRSCtl
CSS
to restore the shadow set of the mode to which
control returns.
Modes of Operation
The 4KEc core supports three modes of operation: user
mode, kernel mode, and debug mode. User mode is most
often used for applications programs. Kernel mode is
typically used for handling exceptions and operating
system kernel functions, including CP0 management and I/
O device accesses. An additional Debug mode is used
during system bring-upandsoftwaredevelopment. Refer to
the EJTAG section for more information on debug mode.
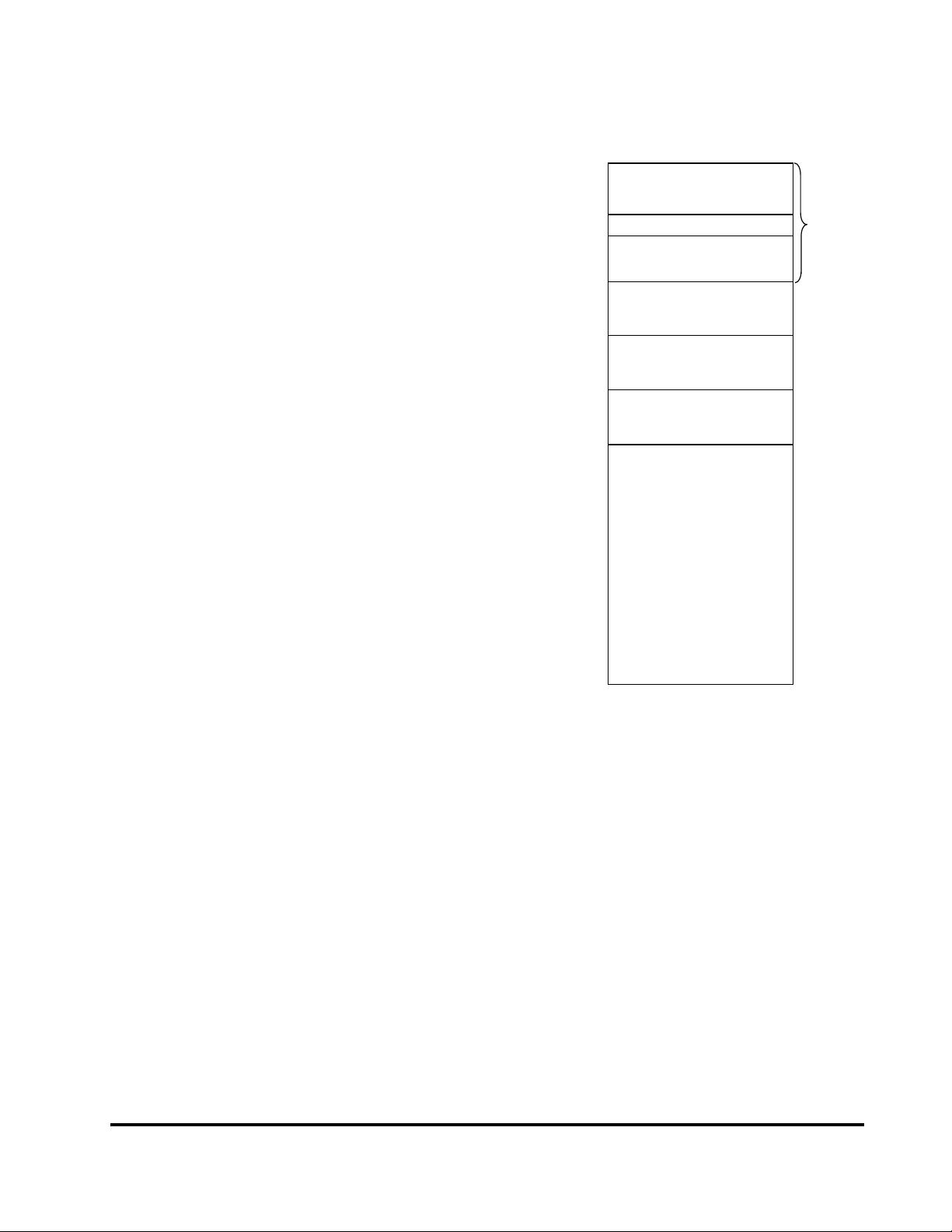
Figure 3 4KEc Core Virtual Address Map
Memory Management Unit (MMU)
The 4KEc core contains a fully functional MMU that
interfaces between the execution unit and the cache
controller. Although the 4KEc core implements a 32-bit
architecture, the MMU is modeled after that found in the
64-bit R4000 family, as defined by the MIPS32 Privileged
Resource Architecture (PRA).
The 4KEc core implements a TLB-based MMU. The TLB
consists of three translation buffers: a 16 dual-entry fully
associative Joint TLB (JTLB), a 4-entry fully associative
Instruction TLB (ITLB) and a 4-entry fully associative data
TLB (DTLB).
When an instruction address is calculated, the virtual
address is compared to the contents of the 4-entry ITLB. If
kuseg
kseg0
kseg1
kseg2
kseg3
0x00000000
0x7FFFFFFF
0x80000000
0x9FFFFFFF
0xA0000000
0xBFFFFFFF
0xC0000000
0xDFFFFFFF
0xE0000000
0xF1FFFFFF
Kernel virtual address space
Unmapped, 512 MB
Kernel virtual address space
Uncached
Unmapped, 512 MB
Kernel virtual address space
User virtual address space
1. This space is mapped to memory in user or kernel mode,
and by the EJTAG module in debug mode.
0xFF200000
0xFF3FFFFF
0xFF400000
0xFFFFFFFF
Memory/EJTAG
1
Mapped, 2048 MB
Mapped, 512 MB
Memory Mapped
Memory Mapped