0
−0.2
0
0.2
0.4
0.6
0.8
1
Distance
Correlation coefficien
Indoor
Outdoor
L
L
L
L
L
Figure 1: Pearson corre-
lation coefficient decreas-
es with growing distance
2
0
3
4
Mismatch rate
0
0.
0.
0.
0.
'LVFDUGHG rate
0
0.2
0.4
0.6
0.8
1
MismatchUDWH
'LVFDUGHG UDWH
$EDQGRQHG=RQH
Figure 2: Dilemma of mis-
match rate and discarded
rate
0 5 10 15 20 25 30 35 40
# of Error %its
0
50
100
150
200
250
# of Check 7imes
RISDVVHV 5
RISDVVHV
RISDVVHV
Figure 3: Mismatched
bits cause high cost in er-
ror correction
0 5 10 15 20 25 30 35 40
# of Error Bits
0
0.2
0.4
0.6
0.8
1
Recall Rate
5 times
6 times
7 times
Figure 4: Information
reconciliation fails more
seriously with increasing
error bits
Eve know about the key. We have the following security
requirements.
• Authenticity. A device needs to ensure that it is mak-
ing key agreement with other legitimate devices. Any
spoofer will be detected.
• Confidentiality. Any information of the key should not
be exposed to Eve.
• Integrity. The key should be consistent at all legiti-
mate devices.
We do not consider availability in this work. If Eve block
all WiFi signals, devices may not agree on any key.
2.2 Feasibility of CSI-based key generation
In this paper, we use CSI as the proof of authenticity and
source of common secret information. The intuition of us-
ing CSI is that it is a unique and correlated measurement
for devices around a particular physical location. CSI mea-
surements at different devices are rapidly de-correlated with
distance between them. In addition, CSI is unpredictable
due to its random property caused by the multipath effect
of signal propagation. CSI is a much richer source of secret
information than the one of RSS, because it contains the
information of 56 subcarriers in each measurement sample.
We demonstrate the properties using experimental vali-
dation. We use two laptop computers Alice and Bob, each
equipped with COTS wireless NIC model Intel 5300 oper-
ating in the 802.11n 2.4GHz channel.
2
They then collect
measurement results of the CSI amplitude values indepen-
dently from a public WiFi while varying their distance from
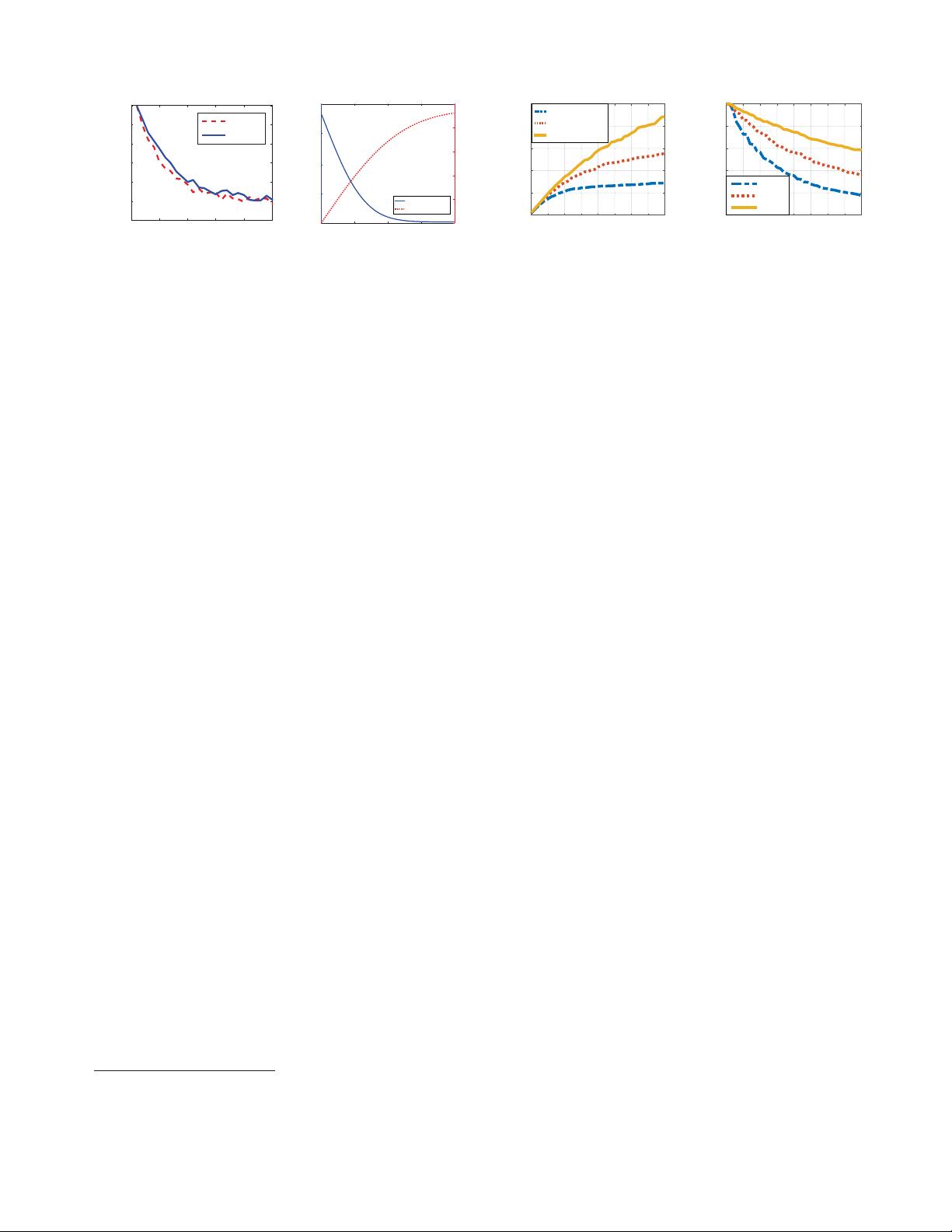
0.1λ to 2.5λ, where the wavelength λ =12.5cm for 2.4GHz.
Figure 1 shows the Pearson product-moment correlation co-
efficient of the CSI samples from the two devices. We found
that when the distance is smaller than 0.5λ, the samples are
highly correlated. The correlation drops quickly with the
distance growth. When the distance > 2λ, the samples are
uncorrelated.
The above properties of CSI are important for device au-
thentication and key agreement. Only if the samples from
different devices nearby are similar, CSI can be a proof of
2
We use laptops for the ease of programming. The method
can be applied to any devices with 802.11 NICs.
physical proximity. Only if the samples are rapidly de-
correlated with distance between the devices, CSI can be
a common secure information.
2.3 Challenges of CSI-based key generation
Suppose two devices, Alice and Bob both listen to a public
WiFi source. For each of them, the CSI amplitude value h(t)
at time t can be directly obtained from an existing API of
the Intel 5300 network card. To extract secret information
from two similar measurements of CSI amplitude values, a
simple approach is to determine a cut-off amplitude level
h anduse0torepresentsamplessmallerthanh and 1 to
represent samples larger than h. For example, h can be 0.5
for CSI amplitude varying in [0, 1]. This method is called
reciprocal quantization.
Reciprocal quantization may cause mismatched bits at t-
wo devices. For example, if Alice gets a CSI value 0.53 for
a particular bit, Bob gets 0.48, and the cut-off is 0.5, then
they will have a different bit. To reduce these mismatched
bits, existing quantization methods often use an abandoned
zone. For example, if the abandoned zone is [0.4, 0.6], then
only if a CSI value is less than 0.4 (or larger than 0.6), it
canbeconvertedtoa0-bit(or1-bit).
Selecting the size of the abandoned zone is a dilemma: if
the zone is small, mismatched bits still occur; if the zone
is large, too many CSI samples will be discarded, slowing
secret bit generation. Figure 2 shows the bit mismatch rate
versus the discarded bit rate by varying the abandoned zone
from 0 to 4σ, where σ is the standard deviation of the Gaus-
sian noise. We find that when the abandoned zone is smaller
than σ, the discarded rate is low but it causes more than 10%
mismatched bits. When the zone is large, e.g.,3σ,themis-
match rate is negligible but more than 80% samples will be
discarded. To further demonstrate the harm of mismatched
bits, we use an existing method, information reconciliation
[3] [8], to fix mismatched bits by iterative parity checks.
Figure 3 shows that the rounds of parity checks increase sig-
nificantly with growing mismatched bits, for generation of a
256-bit key. For 20 mismatched bits, it requires more than
70-150 parity check bits to correct them. Besides tremen-
dous communication and time cost, the number of secret
bits is also reduced from 256 to < 150 due to privacy am-
plification [17]. Additionally, information reconciliation is a









