Special Publication 800-53A Guide for Assessing the Security Controls in Federal Information Systems
________________________________________________________________________________________________
determination statements are closely linked to the content of the security control (i.e., the security
control functionality) and the assurance requirements in NIST Special Publication 800-53 to
ensure traceability of assessment results back to the fundamental control requirements. The
application of an assessment procedure to a security control produces assessment findings. These
assessment findings are subsequently used in helping to determine the overall effectiveness of the
security control.
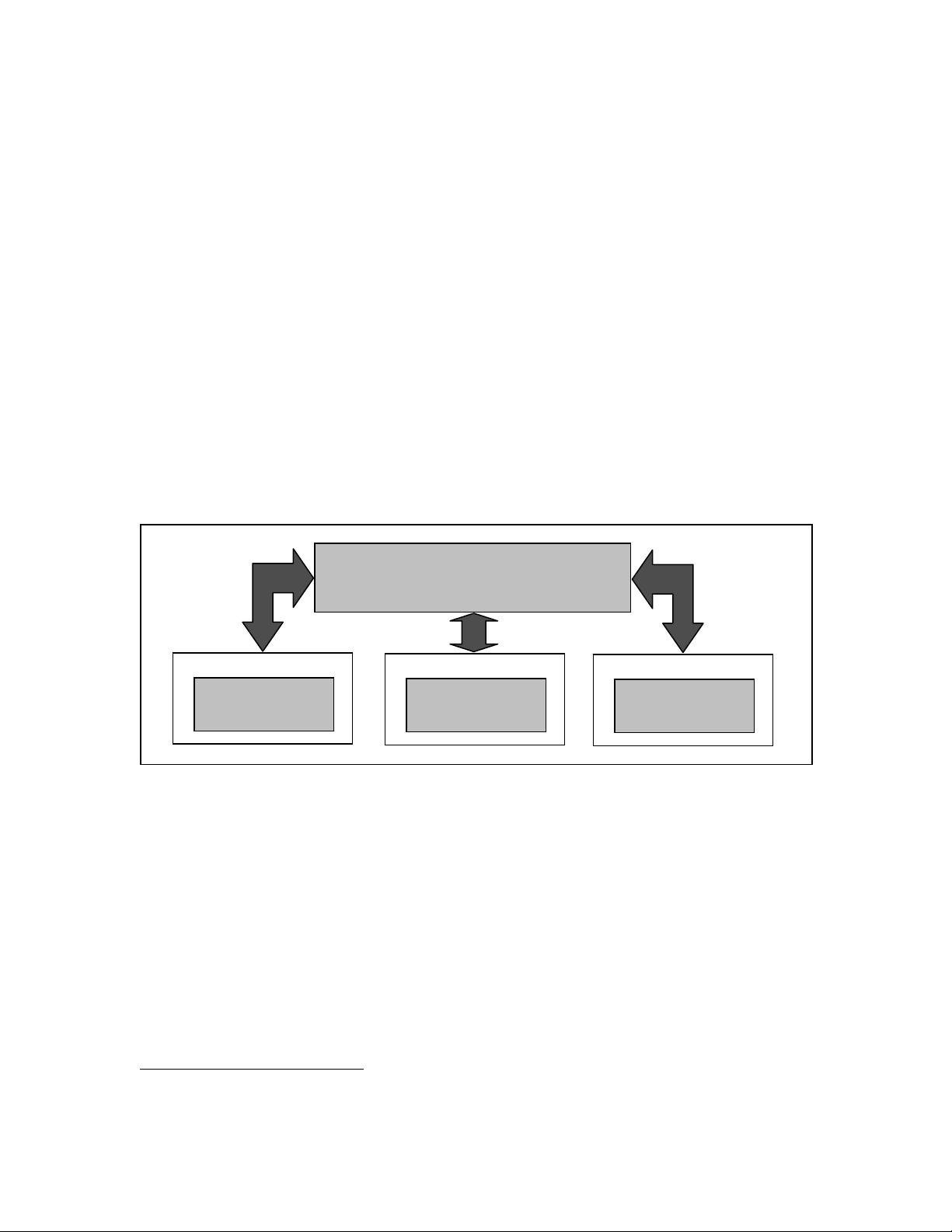
The assessment objects identify the specific items being assessed and include specifications,
mechanisms, activities, and individuals. Specifications are the document-based artifacts (e.g.,
policies, procedures, plans, system security requirements, functional specifications, and
architectural designs) associated with an information system. Mechanisms are the specific
hardware, software, or firmware safeguards and countermeasures employed within an information
system.
20
Activities are the specific protection-related pursuits or actions supporting an
information system that involve people (e.g., conducting system backup operations, monitoring
network traffic, exercising a contingency plan). Individuals, or groups of individuals, are people
applying the specifications, mechanisms, or activities described above.
The assessment methods define the nature of the assessor actions and include examine, interview,
and test. The examine method is the process of reviewing, inspecting, observing, studying, or
analyzing one or more assessment objects (i.e., specifications, mechanisms, or activities). The
purpose of the examine method is to facilitate assessor understanding, achieve clarification, or
obtain evidence. The interview method is the process of conducting discussions with individuals
or groups of individuals within an organization to once again, facilitate assessor understanding,
achieve clarification, or obtain evidence. The test method is the process of exercising one or
more assessment objects (i.e., activities or mechanisms) under specified conditions to compare
actual with expected behavior. In all three assessment methods, the results are used in making
specific determinations called for in the determination statements and thereby achieving the
objectives for the assessment procedure.
Each of the assessment methods described above has a set of associated attributes, depth and
coverage, which help define the expected level of effort for the assessment. These attributes are
hierarchical in nature, providing the means to define the rigor and scope of the assessment for the
increased assurance needed for higher impact level information systems. The depth attribute
addresses the rigor of and level of detail in the examination, interview, and testing processes.
Values for the depth attribute include generalized, focused, and detailed. The coverage attribute
addresses the scope or breadth of the examination, interview, and testing processes including the
number and type of specifications, mechanisms, and activities to be examined or tested and the
number and types of individuals to be interviewed. Values for the coverage attribute include
representative, specific, and comprehensive. Appendix D provides attribute definitions and
descriptions of each assessment method. The appropriate depth and coverage attribute values for
a particular assessment method are the values needed to achieve the assessment expectations
defined in Appendix E (described further below) based upon the characteristics of the information
system being assessed (including impact level) and the specific determinations to be made.
Each of the information system impact levels (i.e., low, moderate, high) has an associated set of
minimum assurance requirements defined in NIST Special Publication 800-53. The assurance
requirements are directed at security control developers and implementers. Based on the
assurance requirements, security control developers and implementers carry out required
20
Mechanisms also include physical protection devices associated with an information system (e.g., locks, keypads,
security cameras, fire protection devices, fireproof safes, etc.).
CHAPTER 2 PAGE 9