1580 IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY, VOL. 10, NO. 8, AUGUST 2015
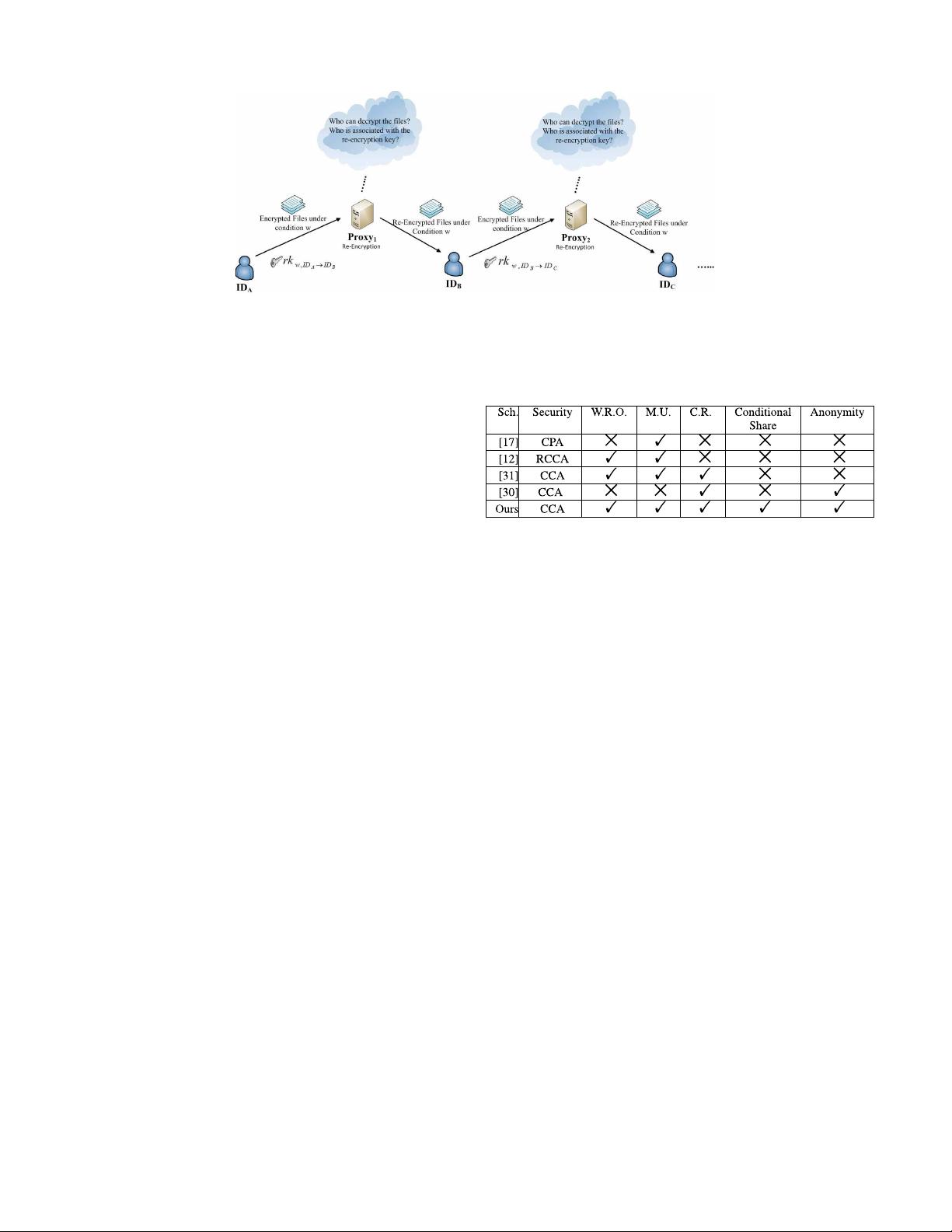
Fig. 1. Anonymous Multi-Hop Identity-Based Conditional Proxy Re-Encryption.
in the ROM: one is CPA secure and the other holds against
CCA. Later on, two CPA-secure IBE-PRE schemes (in the
types of PKE-IBE and IBE-IBE) [27] have been proposed.
Afterwards, some IBPRE systems have been proposed for
various requirements (see [28], [34]).
In the multiple ciphertext receiver update
1
scenario,
Green and Ateniese [17] proposed the first MH-IBPRE scheme
with CPA security. Later on, a RCCA-secure MH-IBPRE
scheme without random oracles was proposed by Chu and
Tzeng [12]. These schemes, however, are not collusion-safe.
To solve the problem, Shao and Cao [31] proposed
a CCA-secure MH-IBPRE in the standard model with
collusion-safe property.
To hide the information leaked from re-encryption key,
Ateniese et al. [1] defined the notion of key-privacy
(i.e. an adversary cannot identify delegator and delegatee even
given re-encryption key). Later on, Shao et al. [33] revised
the security model introduced in [1]. To prevent a ciphertext
from being traced, Emura et al. [15] proposed a unidirectional
IBPRE scheme in which an adversary cannot identify the
source from the destination ciphertext. To ensure the privacy of
both delegator and delegatee, Shao et al. [32] proposed the first
Anonymous PRE (ANO-PRE) system. The system guarantees
that an adversary cannot identify the recipient of original
and re-encrypted ciphertext even given the corresponding
re-encryption key. In 2012, Shao [30] also proposed the first
anonymous IBPRE with CCA security in the ROM.
In the context of IBE/ABE, some well-known systems
supporting anonymity that have been proposed, such as [8],
[9], [16], and [29]. Leveraging them may partially fulfill
our goals. However, we need to focus on the combination
of anonymity and ciphertext update properties. Therefore,
the aforementioned systems are not taken in comparison
below.
Here, we compare our work with the some related systems,
and summarize the comparison of properties in Table I. While
multiple ciphertext receiver update (denoting as M.U.), con-
ditional (data) share, collusion resistance (denoting as C.R.),
anonymity, and without random oracle (denoting as W.R.O.),
have all five been partially achieved by previous schemes,
1
We refer to multiple ciphertext receiver update to a notion called Multi-Hop
(MH) in this paper.
TABLE I
F
UNCTIONALITY AND SECURITY COMPARISON
there is no effective CCA-secure proposal that achieves all
properties simultaneously in the standard model. This paper,
for the first time, fills the gap.
II. S
YSTEM DEFINITION AND THREAT MODELS
A. System Definition
Definition 1: A unidirectional Multi-Hop Identity-Based
Conditional Proxy Re-Encryption (MH-IBCPRE) scheme
consists of the following algorithms:
1) (mpk, msk) ← Setup(1
k
): on input a security parameter k,
output a master public key mpk and a master secret key
msk. For simplicity, we omit mpk in the expression of
the following algorithms.
2) sk
ID
← KeyGen(msk, ID): on input msk, and an identity
ID∈{0, 1}
∗
, output a secret key sk
ID
.
3) rk
w,ID
i
→ID
i
← ReKeyGen(I D
i
, sk
ID
i
, ID
i
,w): on
input a delegator’s identity ID
i
and the corresponding
secret key sk
ID
i
, a delegatee’s identity ID
i
, and a condi-
tion w ∈{0, 1}
∗
, output a re-encryption key rk
w,ID
i
→ID
i
from ID
i
to ID
i
under condition w.
4) C
1,ID
i
,w
← Enc(ID
i
, w,m):on input an identity ID
i
,a
condition w and a message m, output a 1-level ciphertext
C
1,ID
i
,w
under identity ID
i
and w.
5) C
l+1,ID
i
,w
← ReEnc(rk
w,ID
i
→ID
i
,C
l,ID
i
,w
): on input
rk
w,ID
i
→ID
i
,andanl-level ciphertext C
l,ID
i
,w
under
identity ID
i
and w, output an (l + 1)-level ciphertext
C
l+1,ID
i
,w
under identity ID
i
and w or ⊥ for failure,
where l ≥ 1, l ∈ N.
6) m ← Dec(sk
ID
i
, C
l,ID
i
,w
): on input sk
ID
i
,andanl-level
ciphertext C
l,ID
i
,w
under identity ID
i
and w, output a
message m or ⊥ for failure, where l ≥ 1, l ∈ N.









