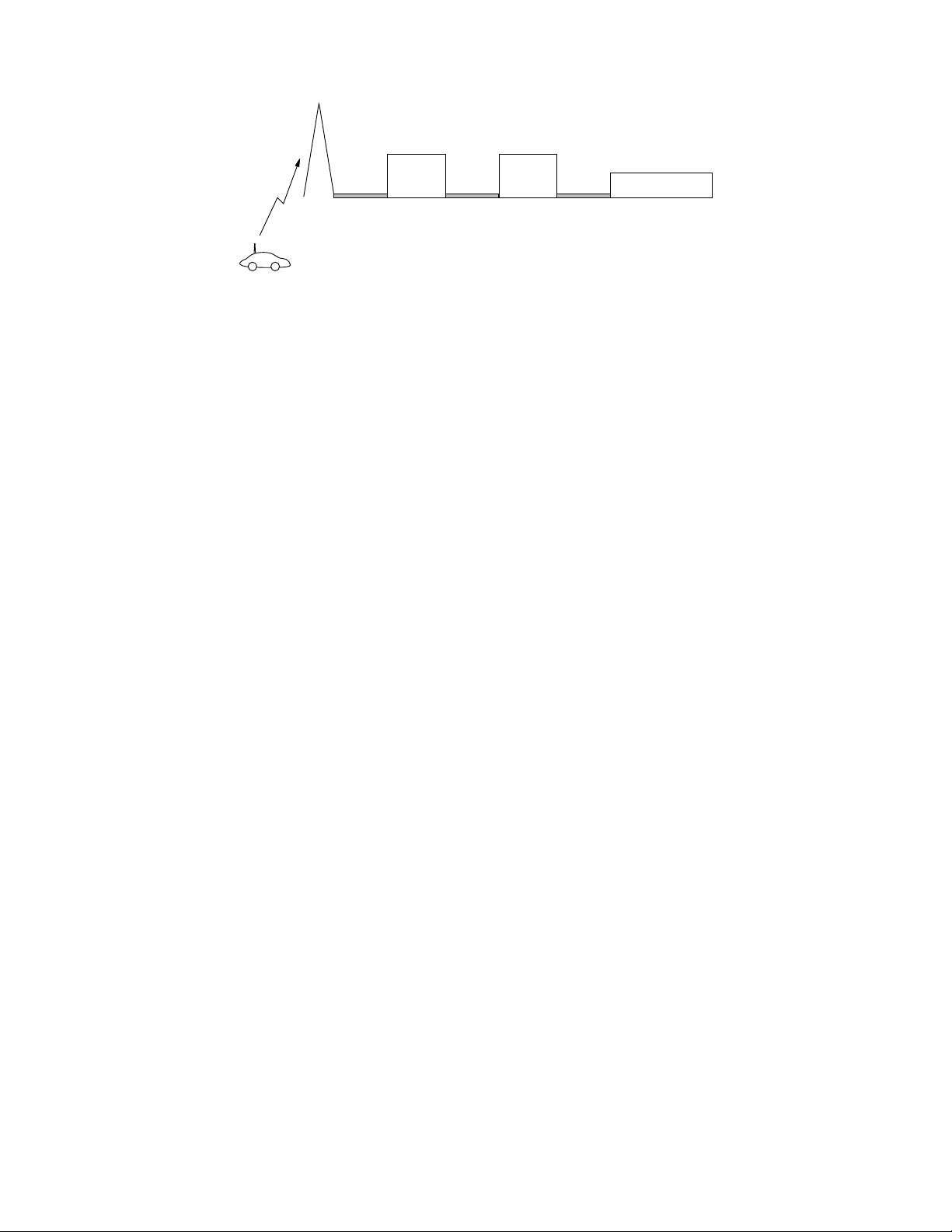
1.3 Technical Issues
The technical problems that must be solved to make the wireless vision a reality extend across all levels of
the system design. At the hardware level the terminal must have multiple modes of operation to support
the different applications and media. Desktop computers currently have the capability to process voice,
image, text, and video data, but breakthroughs in circuit design are required to implement multimode
operation in a small, lightweight, handheld device. Since most people don’t want to carry around a
twenty pound battery, the signal processing and communications hardware of the portable terminal must
consume very little power, which will impact higher levels of the system design. Many of the signal
processing techniques required for efficient spectral utilization and networking demand much processing
power, precluding the use of low power devices. Hardware advances for low power circuits with high
processing ability will relieve some of these limitations. However, placing the processing burden on fixed
sites with large power resources has and will continue to dominate wireless system designs. The associated
bottlenecks and single points-of-failure are clearly undesirable for the overall system. Moreover, in some
applications (e.g. sensors) network nodes will not be able to recharge their batteries. In this case the finite
battery energy must be allocated efficiently across all layers of the network protocol stack [5]. The finite
bandwidth and random variations of the communication channel will also require robust compression
schemes which degrade gracefully as the channel degrades.
The wireless communication channel is an unpredictable and difficult communications medium. First
of all, the radio spectrum is a scarce resource that must be allocated to many different applications and
systems. For this reason spectrum is controlled by regulatory bodies both regionally and globally. In
the U.S. spectrum is allocated by the FCC, in Europe the equivalent body is the European Telecommu-
nications Standards Institute (ETSI), and globally spectrum is controlled by the International Telecom-
munications Union (ITU). A regional or global system operating in a given frequency band must obey
the restrictions for that band set forth by the corresponding regulatory body as well as any standards
adopted for that spectrum. Spectrum can also be very expensive since in most countries, including the
U.S., spectral licenses are now auctioned to the highest bidder. In the 2 GHz spectral auctions of the
early 90s, companies spent over nine billion dollars for licenses, and the recent auctions in Europe for 3G
spectrum garnered over 100 billion dollars. The spectrum obtained through these auctions must be used
extremely efficiently to get a reasonable return on its investment, and it must also be reused over and
over in the same geographical area, thus requiring cellular system designs with high capacity and good
performance. At frequencies around several Gigahertz wireless radio components with reasonable size,
power consumption, and cost are available. However, the spectrum in this frequency range is extremely
crowded. Thus, technological breakthroughs to enable higher frequency systems with the same cost and
performance would greatly reduce the spectrum shortage, although path loss at these higher frequencies
increases, thereby limiting range.
As a signal propagates through a wireless channel, it experiences random fluctuations in time if the
transmitter or receiver is moving, due to changing reflections and attenuation. Thus, the characteristics
of the channel appear to change randomly with time, which makes it difficult to design reliable systems
with guaranteed performance. Security is also more difficult to implement in wireless systems, since
the airwaves are susceptible to snooping from anyone with an RF antenna. The analog cellular systems
have no security, and you can easily listen in on conversations by scanning the analog cellular frequency
band. All digital cellular systems implement some level of encryption. However, with enough knowledge,
time and determination most of these encryption methods can be cracked and, indeed, several have been
compromised. To support applications like electronic commerce and credit card transactions, the wireless
network must be secure against such listeners.
Wireless networking is also a significant challenge [23, 24, 25, 26]. The network must be able to
8