D. Xie et al. / Digital Signal Processing 95 (2019) 102587 3
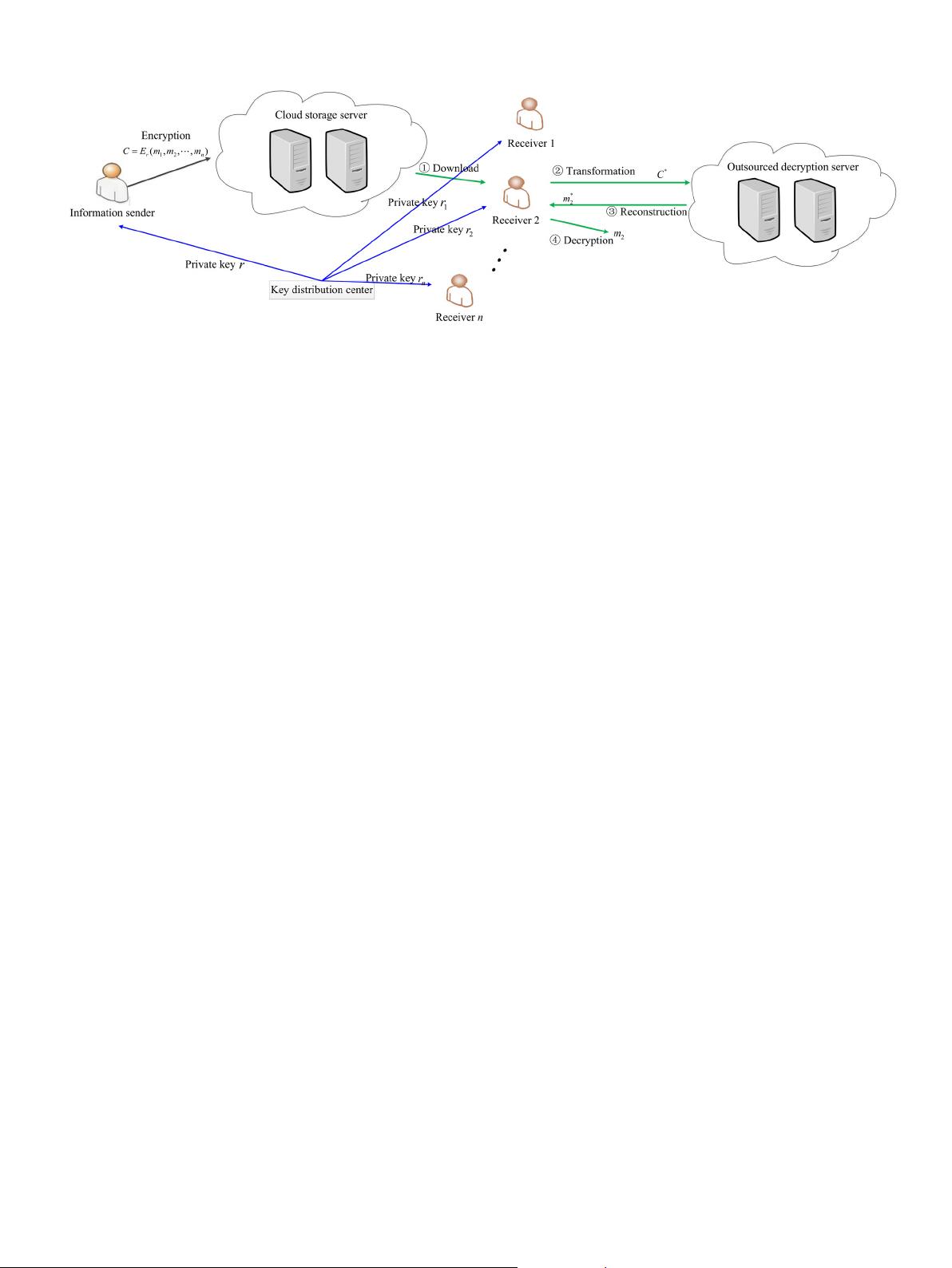
Fig. 3. The framework of the proposed scheme.
requirements of decryption algorithms. Thus, the efficiency is one
of the major obstacles to applying this encryption framework to a
resource-constrained embedded application scenarios.
In
this paper, we present aone-to-many encryption method
with the privacy-preserving homomorphic outsourced decryption
based on CS. Fig. 3 shows the schematic diagram of the proposed
framework. The main contribution of this work can be summarized
as follows:
• First, we present a novel attribute-based key distribution
mechanism for the proposed symmetric cryptosystem. In tra-
ditional
symmetric encryption schemes, each user should store
n − 1private keys and the number of keys are C
2
n
, where n
is
the number of users. Our scheme employs the social at-
tributes
of each user. We formalize these social attributes of
each user according to certain partitioning rules, and these at-
tributes
form the attribute set of this user. Thus, all attributes
of n users form the maximum attribute set MAS. The trusted
key distribution center (KDC) distributes private keys for each
user according to the attribute set of this user. Thus, the pri-
vate
key storage space of each user is equal to the size of its
attribute set, and the number of the total keys is |MAS |.
• Second, we break through the traditional one-to-one CS-based
encryption method, and introduce aone-to-many encryption
framework according to the proposed attribute-based key dis-
tribution
mechanism. In our scheme, the sender can encrypt
multiple plaintexts for different users simultaneously accord-
ing
to the attributes he owns. If a user has one or more
attributes which the sender uses for encryption, then he can
decrypt the corresponding plaintexts from the ciphertexts.
• Last, the receiver does not decrypt each acquired ciphertext
himself, but outsources the decryption process to an un-
trusted
third party cloud server, called Outsourced Decryption
Server (ODS). The purpose of doing this is to improve the
efficiency of the decryption process. Note that CS-based en-
cryption
schemes are not applicable for resource-constrained
embedded systems, especially for high-dimensional image de-
cryptions.
To protect the secrecy of plaintexts, we introduce
a transformation algorithm which can transform the original
decryption problem into a variant one. The receiver does not
send the original decryption problem directly to the ODS, but
sends a variant one. Thus, the ODS does not obtain the original
plaintexts after performing the decryption process.
1.1. Organization
The rest of this paper is organized as follows. Section 2 recalls
some basic background of chaotic maps and the CS theory. We
will introduce the proposed one-to-many encryption scheme ex-
plicitly
in Section 3. Section 4 gives the security analysis about our
scheme. In Section 5, some experiments are carried out to show
the feasibility and the superiority of the proposed scheme. Finally
we conclude this paper in Section 6.
2. Background
2.1. Chaotic maps
Here we give the simple definitions of three kinds of chaotic
maps, which are used for constructing chaotic measurement ma-
trices
in our experiments.
2.1.1.
Logistic map
The
standard logistic map is defined recurrently by
x(n +1) = 4x(n)(1 − x(n)), (1)
where x(0) ∈ (0, 1) is the initial value and thus x(n) ∈ (0, 1).
2.1.2.
Skew tent map
The
one-dimensional skew tent map with parameter μ is given
by
y(n + 1) =
y(n)/μ 0 < y(n)<μ
1 − y(n)/(1 −μ) μ ≤ y(n)<1
, (2)
where y(0) ∈ (0, 1) is the initial value and μ ∈ (0, 1) is a system
parameter.
2.1.3.
Chebyshev map
The
w-th order Chebyshev map is defined by
z(n + 1) = cos(w arccos(z(n))), (3)
where this map is chaotic for w ≥2, and z(n) ∈ (−1, 1).
2.2. Compressed sensing
To compress an n-dimensional sparse vector x, the compression
process of CS can be represented by a special case of the underde-
termined
linear system:
y =Ax, (4)
where A ∈ R
m×n
(m < n) and y ∈ R
m
denote the measurement
matrix and the measurement vector, respectively. Here we call a
vector x k-sparse if it has at most k nonzero entries. Similarly, the
sparsity of a matrix X is the maximum number of nonzero entries
of column vectors in X. Previous studies show that some natural
signals can be represented using only a few non-zero coefficients









