V 7.1
10
CIS Control 1: Procedures and Tools
This Control requires both technical and procedural actions, united in a process that accounts for
and manages the inventory of hardware and all associated information throughout its life cycle.
It links to business governance by establishing information/asset owners who are responsible
for each component of a business process that includes information, software, and hardware.
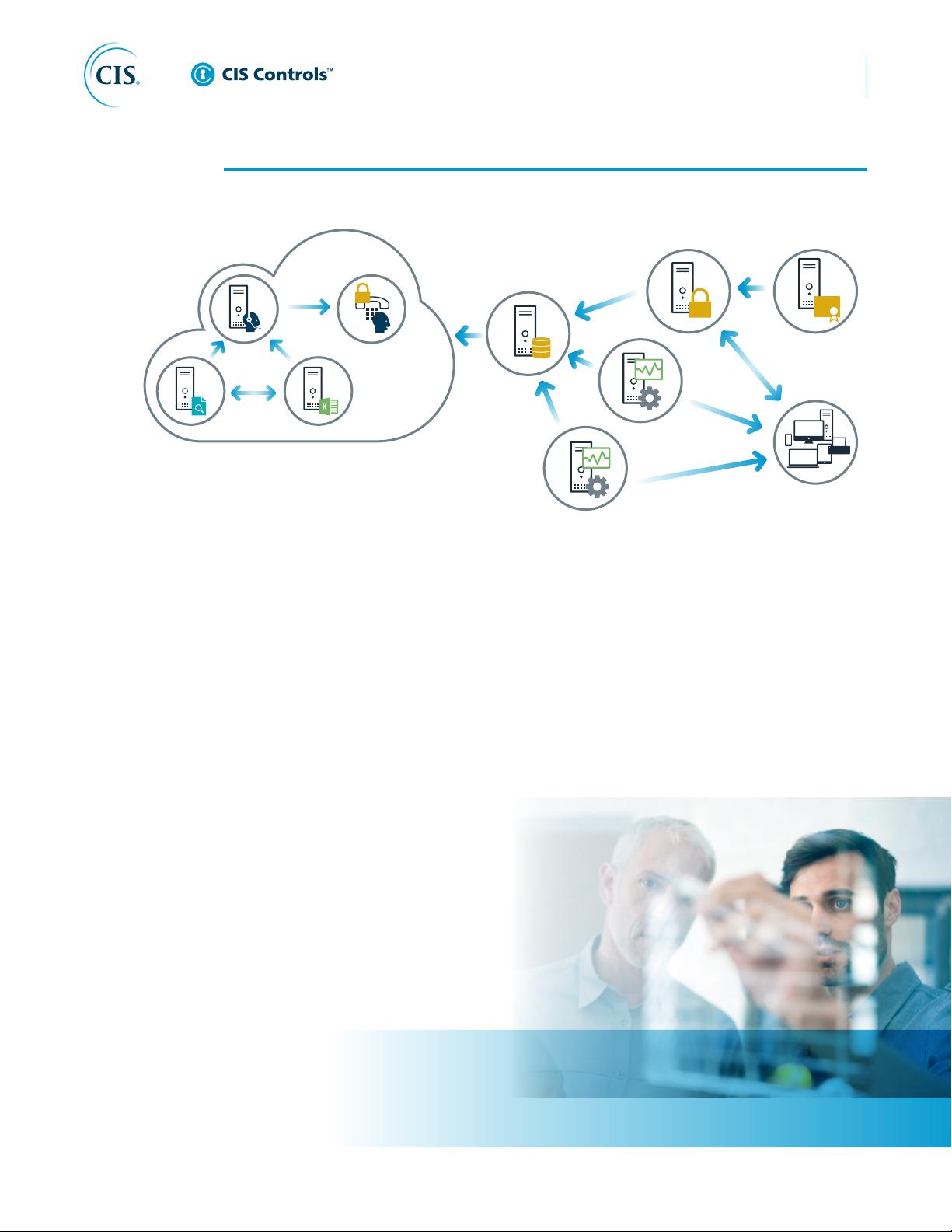
Organizations can use large-scale, comprehensive enterprise products to maintain IT asset
inventories. Others use more modest tools to gather the data by sweeping the network, and
manage the results separately in a database.
Maintaining a current and accurate view of IT assets is an ongoing and dynamic process.
Organizations can actively scan on a regular basis, sending a variety of dierent packet types to
identify devices connected to the network. Before such scanning can take place, organizations
should verify that they have adequate bandwidth for such periodic scans by consulting load
history and capacities for their networks.
In conducting inventory scans, scanning tools could send traditional ping packets (ICMP Echo
Request) looking for ping responses to identify a system at a given IP address. Because some
systems block inbound ping packets, in addition to traditional pings, scanners can also identify
devices on the network using transmission control protocol (TCP), synchronize (SYN), or
acknowledge (ACK) packets. Once they have identified IP addresses of devices on the network,
some scanners provide robust fingerprinting features to determine the operating system type of
the discovered machine.
In addition to active scanning tools that sweep the network, other asset identification tools
passively listen on network interfaces for devices to announce their presence by sending trac.
Such passive tools can be connected to switch span ports at critical places in the network to
view all data flowing through such switches, maximizing the chance of identifying systems
communicating through those switches.
Many organizations also pull information from network assets such as switches and routers
regarding the machines connected to the network. Using securely authenticated and encrypted
network management protocols, tools can retrieve media access control (MAC) addresses
and other information from network devices that can be reconciled with the organization’s
asset inventory of servers, workstations, laptops, and other devices. Once MAC addresses are
confirmed, switches should implement 802.1x and Network Access Control (NAC) to only allow
authorized systems that are properly configured to connect to the network.
Wireless devices (and wired laptops) may periodically join a network and then disappear, making
the inventory of currently available systems very dynamic. Likewise, virtual machines can be
dicult to track in asset inventories when they are shut down or paused. Additionally, remote
machines accessing the network using virtual private network (VPN) technology may appear
on the network for a time, and then be disconnected from it. Whether physical or virtual, each
machine using an IP address should be included in an organization’s asset inventory.