The SELinux Notebook - The Foundations
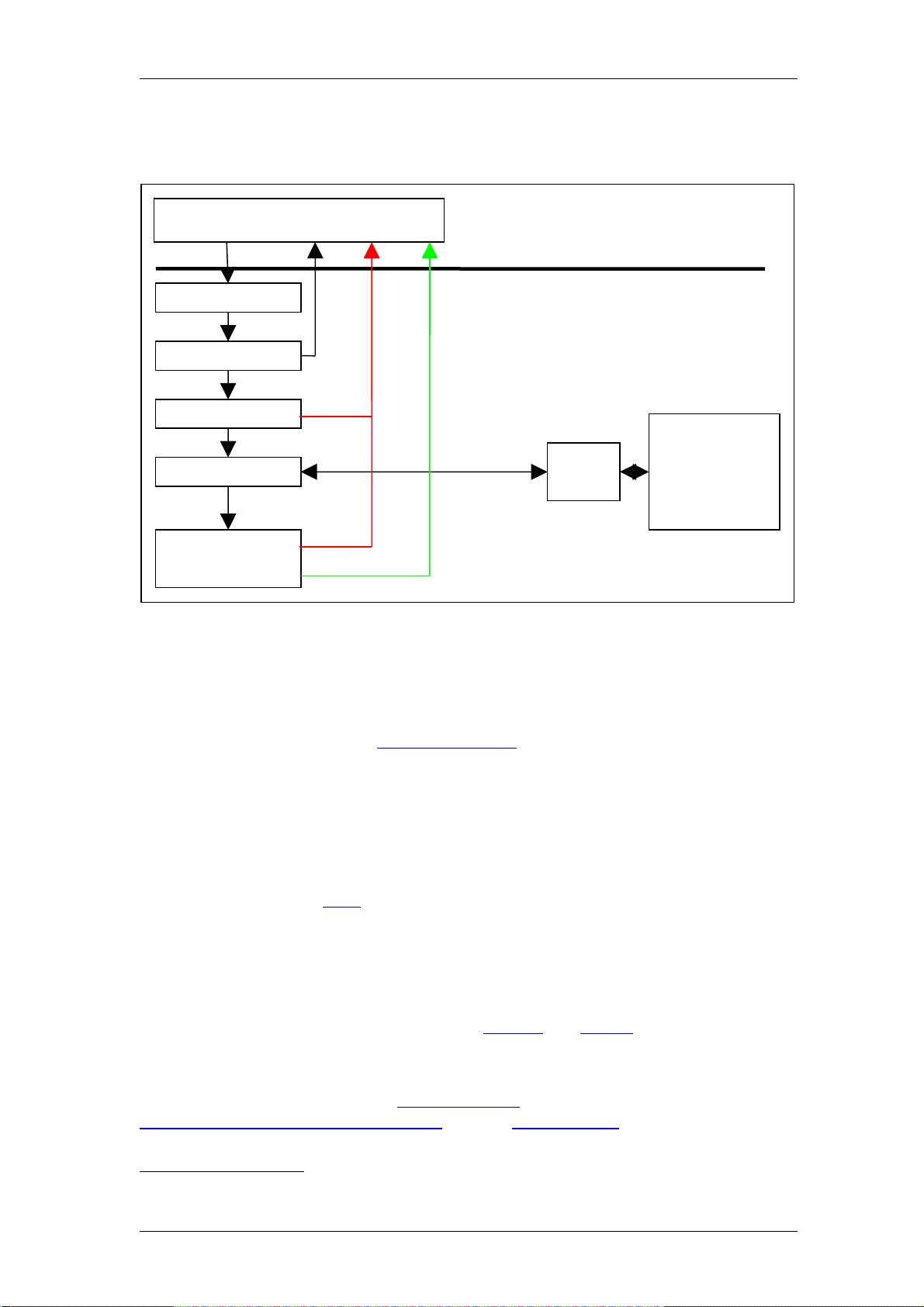
Figure 2.2 shows a more complex diagram of kernel and userspace with a number of
supporting services which are used to manage the SELinux environment. This diagram
will be referenced a number of times to explain areas of SELinux, therefore using
Figure 2.2 as the reference and starting from the bottom:
a) In the current implementation of SELinux, the security server is embedded in
the kernel
2
with the policy being loaded from userspace via a series of functions
contained in a library (libselinux).
However the object managers (OM) and access vector cache (AVC) can reside
in:
kernel space – These object manages are for the kernel services such as
files, directory, socket, IPC etc. and are provided by hooks into the SELinux
sub-system via the Linux Security Module (LSM) framework (shown as
LSM Hooks in Figure 2.2) that is discussed in the LSM section. The
SELinux kernel AVC service is used to cache their requests and the security
servers response.
userspace – These object managers are provided with the application /
service that requires support for MAC and are known as ‘SELinux-aware
3
’
applications or services. Examples of these are: X-Windows, D-bus
messaging (used by the Gnome desktop), PostgreSQL database, Name
Service Cache Daemon (nscd), and the GNU / Linux passwd command.
Generally, these OMs use the AVC services built into the SELinux library
(libselinux), however they could if required supply their own AVC or
not use an AVC at all.
b) The loadable policy (right hand side of Figure 2.2) and its supporting
configuration files are contained in the /etc/selinux directory. This
directory contains the main SELinux configuration file (config) that names
the policy to be loaded and the initial status of SELinux at boot time (enforcing
4
the policy or not). The area also holds all policies that can be activated in their
respective directories /etc/selinux/<policy_name> (e.g.
/etc/selinux/targeted would hold the ‘targeted’ F-12 policy and all its
configuration files). All know configuration files for F-12 SELinux are shown in
the SELinux Configuration Files section.
c) SELinux supports a ‘modular policy’, this means that a policy does not have to
be one large policy, but can be built from modules. A modular policy consists of
a base policy that contains the mandatory information (such as object classes,
permissions etc.), and zero or more policy modules that generally support a
particular application or service. These modules are compiled, linked, and held
in a ‘policy store’ where they can be built into a binary format that is then
loaded into the security server. The types of policy and their construction are
covered in the Types of SELinux Policy section.
2
There is a project developing a Policy Management Server (PMS) that will utilise a user-space
security server, however it is beyond the scope of this Notebook.
3
Generally this means that they use the services provided by the libselinux library as a minimum.
4
When SELinux is enabled the policy can be running in ‘permissive mode’, where all accesses are
allowed and logged in the audit log, even if they are not permitted by the policy (useful for
debugging policy). The policy can also be run in ‘enforcing mode’, where any access that is not
defined in the policy is deigned and an entry placed in the audit log.
Page 16