extension to the network device address to interact with it. The ZigBee Device Object (ZDO) is a special object
which offers services to the APOs: it allows them to discover devices in the network and the service they
implement. It also provides communication, network and security management services. The Application Sublayer
(APS) provides data transfer services for the APOs and the ZDO. Figure 2 illustrates the various components in the
Application Layer.
A ZigBee application must conform to an existing (ZigBee Alliance-accepted) application profile. An application
profile defines message formats and protocols for interactions between APOs that collectively form a distributed
application. The application profile framework allows different developers to independently build and sell ZigBee
devices that can interoperate with each other in a given application profile. Each APO encapsulates a set of
attributes (data entities representing internal state, etc.) and provides functionalities (services) for setting/retrieving
values of these attributes or being notified when an attribute value changes. In the context of a profile, a group of
related attributes is termed a "cluster" and identified with a numeric id. Typically a cluster represents a sort of
interface (or part of it) of the APO to the other APOs.
The application profile must specify one of two possible communication service types. For the Key Value Pair
(KVP) service type the ZigBee standard has predefined message layouts which must be suitably filled by APOs to
request a given operation on attributes residing on a remote APO. The interactions between APOs is limited by the
operations supported on attributes. The Generic Message service type is suitable for applications that do not fit in
the KVP service type and leaves responsibility to the application profile for specifying message types and their
contents.
A special application profile, named the Device Profile, must be implemented by all nodes in a ZigBee network.
The object responsible for this profile is the ZDO. The Device Profile requires its implementing objects (ZDOs) to
support device/service discovery procedures wherein a node attempts to discover existing nodes in the network,
active endpoints on some node and/or the services they implement (available cluster ids).
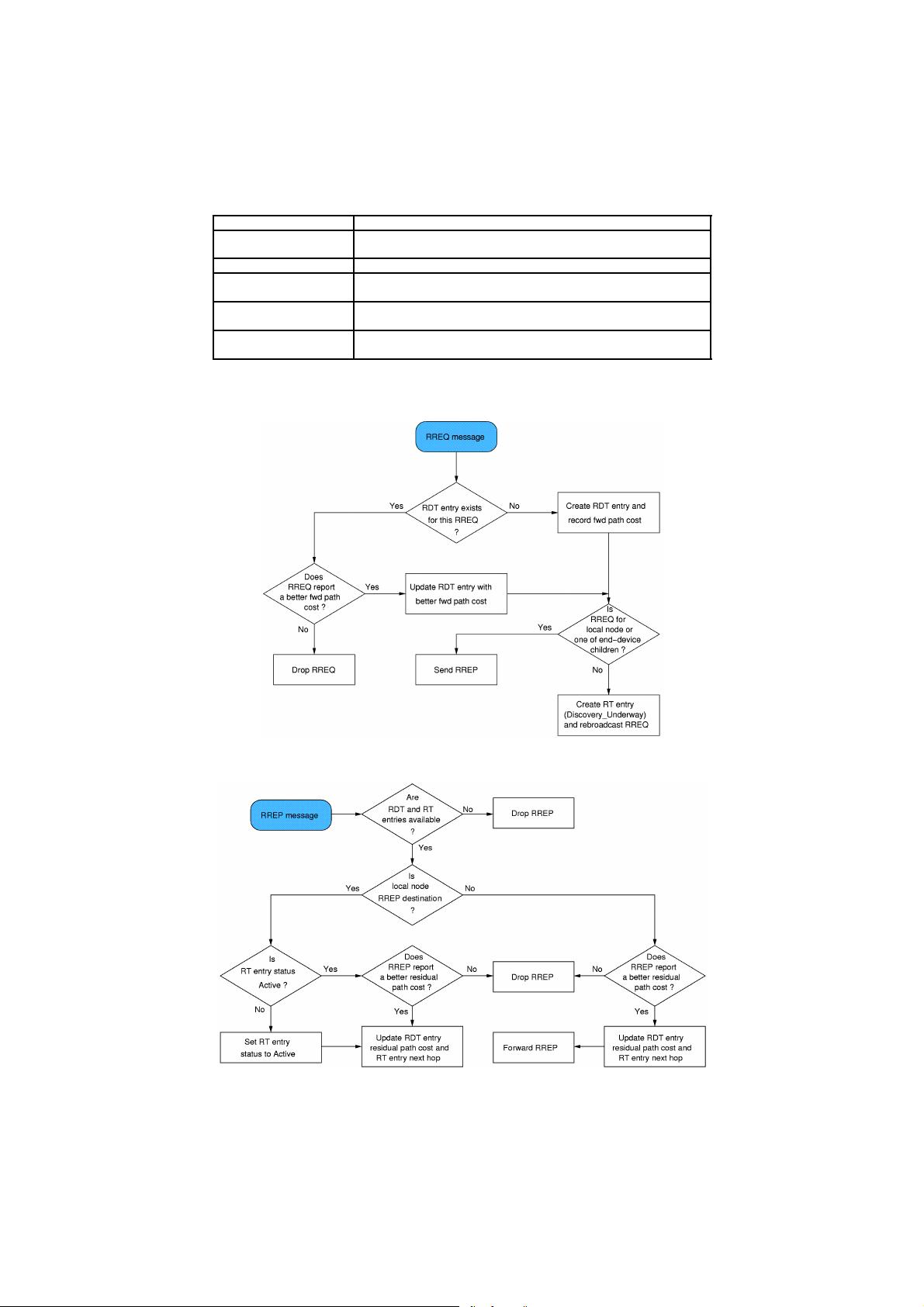
Discovery procedures are crucial to APO addressing. In direct addressing mode a message is addressed to a specific
destination address (16-bit network address) and endpoint number and the sending node is responsible for
discovering both via the ZDO discovery services. Indirect addressing mode only requires the sender to supply a
cluster id but needs support from a neighbouring (or local) ZigBee router (or coordinator) to locate the destination
node(s) for the message. This is possible thanks to the APS of the ZigBee router that maintains a binding table
associating (source address, source endpoint, cluster id) tuples to a list of (destination address, destination endpoint)
tuples, one for each device the message must reach. A message sent by an end-device with indirect addressing
reaches the parent node. Here the APS consults its binding table in order to determine the actual destinations and
send them appropriate messages with direct addressing. Adding and removing entries in the binding table is
commanded by the ZDO in response to local/remote binding requests, as defined in the Device Profile.
3.3 Security in ZigBee
Security services provided for ZigBee include methods for key establishment, key transport, frame protection, and
device management [ZIG05]. The ZigBee Alliance describe the security functionalities based on an open trust
model for a device whereby the different layers of the communication stack and all applications running on a
single device trust each.
The ZigBee specifications provide different means to achieve the following security requirements:
• Freshness: ZigBee devices maintain incoming and outgoing freshness counters to maintain data freshness.
These counters are reset every time a new key is created. Devices that communicate once per second will not
overflow their freshness counters for 136 years.
• Message Integrity: ZigBee specifications provide options of providing 0, 32, 64 or 128 bit data integrity for the
transmitted messages. The default is 64 bit integrity.
• Authentication: Network level authentication is achieved by using a common network key. This prevents
outsider attacks while adding very little in memory cost. Device level authentication is achieved by using
unique link keys between pairs of devices. This prevents insider and outsider attacks but has higher memory
cost.
• Encryption: ZigBee uses 128-bit AES encryption. Encryption protection is possible at network level or device
level. Network level encryption is achieved by using a common network key. Device level encryption is
achieved by using unique link keys between pairs of devices. Encryption can be turned off without impacting
freshness, integrity, or authentication as some applications may not need any encryption.
The ZigBee architecture includes security mechanisms at the MAC, NWK and APS Layers of the protocol stack.
Furthermore, the APS sub-layer provides services for the establishment, and maintenance of security relationships.
The ZigBee Device Object (ZDO) manages the security policies and the security configuration of a device [ZIG05].
The following architectural design choices for security are made in ZigBee specifications:
• The layer that originates a frame is responsible for initially securing it. For example, the MAC layer frames and
NWK command frames are secured by MAC layer security and Network Layer security respectively.
9