Citation: Bansal S, Bansal N (2015) Scapy – A Python Tool For Security Testing. J Comput Sci Syst Biol 8: 140-159. doi:10.4172/jcsb.1000182
Volume 8(3) 140-159 (2015) - 143
J Comput Sci Syst Biol
ISSN: 0974-7230 JCSB, an open access journal
‘E\x00\x00\x14\x00\x01\x00\x00@\x00|\xe7\x7f\x00\x00\x01\x7f\
x00\x00\x01’
>>> IP(_)
<IP version=4L ihl=5L tos=0x0 len=20 id=1 ags= frag=0L ttl=64
proto=IP
chksum=0x7ce7 src=127.0.0.1 dst=127.0.0.1 |>
>>> a=Ether()/IP(dst=”www.slashdot.org”)/TCP()/”GET /index.
html HTTP/1.0 \n\n”
>>> hexdump(a)
00 02 15 37 A2 44 00 AE F3 52 AA D1 08 00 45 00 ...7.D...R....E.
00 43 00 01 00 00 40 06 78 3C C0 A8 05 15 42 23 .C....@.x<....B#
FA 97 00 14 00 50 00 00 00 00 00 00 00 00 50 02 .....P........P.
20 00 BB 39 00 00 47 45 54 20 2F 69 6E 64 65 78 ..9..GET /index
2E 68 74 6D 6C 20 48 54 54 50 2F 31 2E 30 20 0A .html HTTP/1.0 .
0A .
>>> b=str(a)
>>> b
‘\x00\x02\x157\xa2D\x00\xae\xf3R\xaa\xd1\x08\x00E\x00\x00C\
x00\x01\x00\x00@\x06x<\xc0
\xa8\x05\x15B#\xfa\x97\x00\x14\x00P\x00\x00\x00\x00\x00\x00\
x00\x00P\x02 \x00
\xbb9\x00\x00GET /index.html HTTP/1.0 \n\n’
>>> c=Ether(b)
>>> c
<Ether dst=00:02:15:37:a2:44 src=00:ae:f3:52:aa:d1 type=0x800
|<IP version=4L
ihl=5L tos=0x0 len=67 id=1 ags= frag=0L ttl=64 proto=TCP
chksum=0x783c
src=192.168.5.21 dst=66.35.250.151 options=’’ |<TCP sport=20
dport=80 seq=0L
ack=0L dataofs=5L reserved=0L ags=S window=8192
chksum=0xbb39 urgptr=0
options=[] |<Raw load=’GET /index.html HTTP/1.0 \n\n’ |>>>>
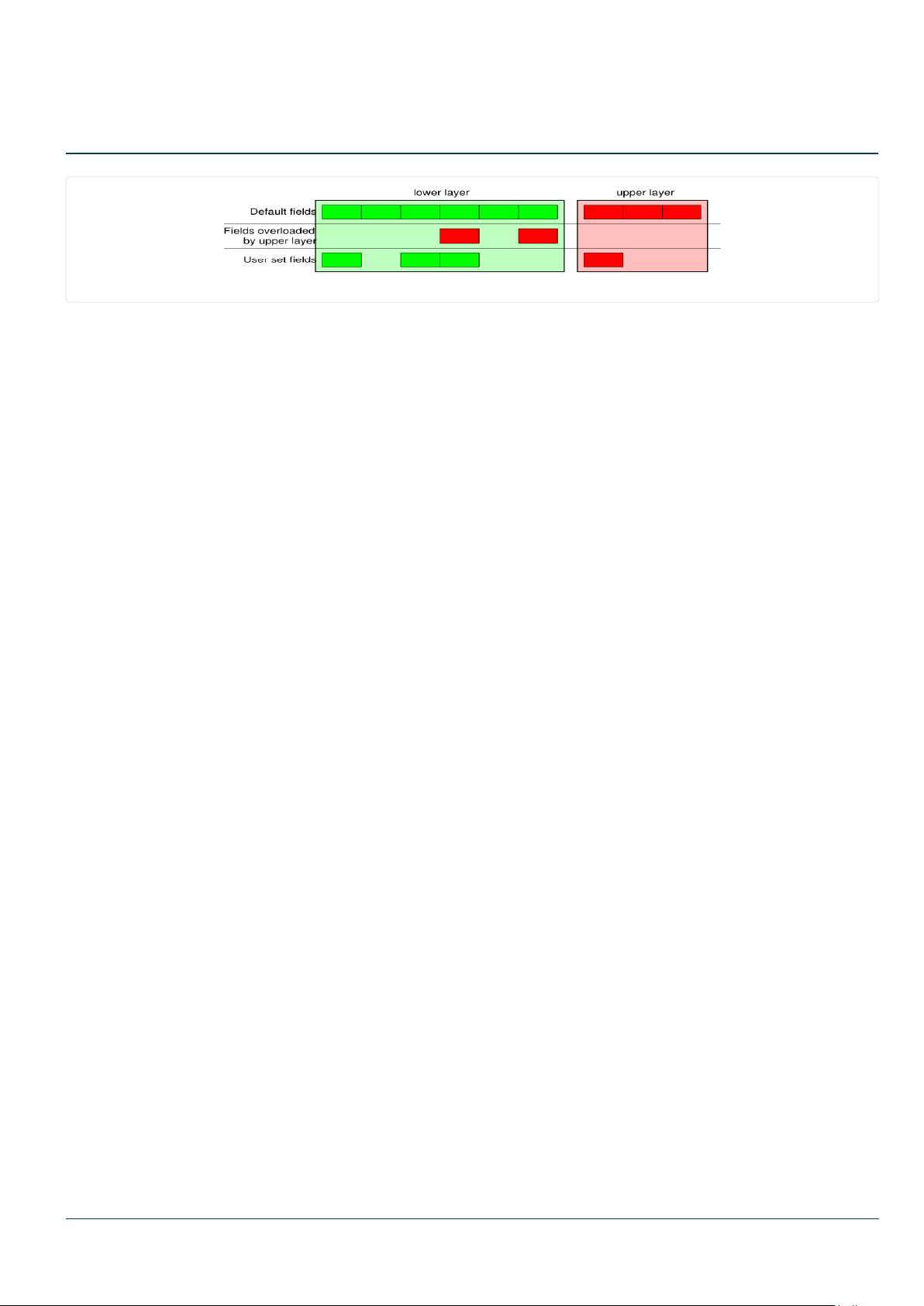
We see that a dissected packet has all its elds lled. at’s because
I consider that each eld has its value imposed by the original string.
If this is too verbose, the method hide_defaults() will delete every eld
that has the same value as the default:
>>> c.hide_defaults()
>>> c
<Ether dst=00:0f:66:56:fa:d2 src=00:ae:f3:52:aa:d1 type=0x800 |<IP
ihl=5L len=67
frag=0 proto=TCP chksum=0x783c src=192.168.5.21
dst=66.35.250.151 |<TCP dataofs=5L
chksum=0xbb39 options=[] |<Raw load=’GET /index.html
HTTP/1.0 \n\n’ |>>>>
Reading PCAP les
You can read packets from a pcap le and write them to a pcap le.
>>> a=rdpcap(“/spare/captures/isakmp.cap”)
>>> a
<isakmp.cap: UDP:721 TCP:0 ICMP:0 Other:0>
Graphical dumps (PDF, PS)
If you have PyX installed, you can make a graphical PostScript/PDF
dump of a packet or a list of packets (see the ugly PNG image below.
PostScript/PDF are far better quality...): (Figure 2, Table 1)
>>> a[423].pdfdump(layer_shi=1)
>>> a[423].psdump(“/tmp/isakmp_pkt.eps”,layer_shi=1)
Generating sets of packets
For the moment, we have only generated one packet. Let see how
to specify sets of packets as easily. Each eld of the whole packet (ever
layers) can be a set. is implicidely dene a set of packets, generated
using a kind of cartesian product between all the elds.
>>> a=IP(dst=”www.slashdot.org/30”)
>>> a
<IP dst=Net(‘www.slashdot.org/30’) |>
>>> [p for p in a]
[<IP dst=66.35.250.148 |>, <IP dst=66.35.250.149 |>,
<IP dst=66.35.250.150 |>, <IP dst=66.35.250.151 |>]
>>> b=IP(ttl=[1,2,(5,9)])
>>> b
<IP ttl=[1, 2, (5, 9)] |>
>>> [p for p in b]
[<IP ttl=1 |>, <IP ttl=2 |>, <IP ttl=5 |>, <IP ttl=6 |>,
<IP ttl=7 |>, <IP ttl=8 |>, <IP ttl=9 |>]
>>> c=TCP(dport=[80,443])
>>> [p for p in a/c]
[<IP frag=0 proto=TCP dst=66.35.250.148 |<TCP dport=80 |>>,
Figure 1: Stacking layers.









