MySQL数据库锁机制详解:从锁类型到锁优化,彻底掌握数据库锁机制
发布时间: 2024-07-24 03:52:38 阅读量: 40 订阅数: 43 

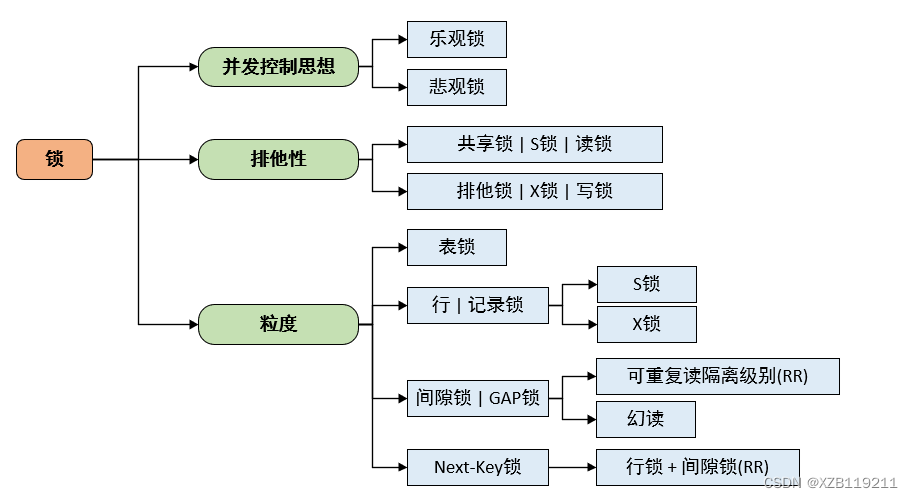
# 1. MySQL数据库锁机制概述
MySQL数据库锁机制是一种并发控制机制,用于协调对数据库资源的访问,防止数据不一致和损坏。锁机制通过对数据库对象(如表、行)进行加锁,确保在同一时刻只有一个事务可以修改这些对象。
锁机制在数据库系统中至关重要,它可以防止以下问题:
- **脏读:**一个事务读取了另一个未提交事务修改的数据。
- **不可重复读:**一个事务多次读取同一数据,但由于另一个事务的修改导致数据发生变化。
- **幻读:**一个事务读取了另一个事务插入或删除的数据,导致读取结果不一致。
# 2. MySQL数据库锁类型详解
### 2.1 共享锁与排他锁
**共享锁(S锁)**允许多个事务同时读取同一数据,但禁止修改。当事务对数据进行读取操作时,会自动获取共享锁。
**排他锁(X锁)**允许一个事务独占地修改数据,禁止其他事务同时读取或修改。当事务对数据进行修改操作时,会自动获取排他锁。
**代码块:**
```sql
-- 获取共享锁
SELECT * FROM table_name WHERE id = 1 LOCK IN SHARE MODE;
-- 获取排他锁
UPDATE table_name SET name = 'new_name' WHERE id = 1 LOCK IN EXCLUSIVE MODE;
```
**逻辑分析:**
* `LOCK IN SHARE MODE`获取共享锁,允许其他事务读取数据。
* `LOCK IN EXCLUSIVE MODE`获取排他锁,禁止其他事务读取或修改数据。
### 2.2 行锁与表锁
**行锁**只锁定被访问的行,而**表锁**锁定整个表。行锁粒度更细,并发性更高,但开销也更大。表锁粒度更粗,并发性较低,但开销较小。
**代码块:**
```sql
-- 获取行锁
SELECT * FROM table_name WHERE id = 1 FOR UPDATE;
-- 获取表锁
LOCK TABLE table_name WRITE;
```
**逻辑分析:**
* `FOR UPDATE`获取行锁,只锁定被查询的行。
* `LOCK TABLE ... WRITE`获取表锁,锁定整个表。
### 2.3 乐观锁与悲观锁
**乐观锁**假设数据不会被其他事务修改,在提交事务时才检查数据是否被修改。如果数据被修改,则回滚事务。
**悲观锁**假设数据会被其他事务修改,在获取数据时就锁定数据,防止其他事务修改。
**代码块:**
```sql
-- 乐观锁
SELECT * FROM table_name WHERE id = 1;
UPDATE table_name SET name = 'new_name' WHERE id = 1 AND version = 1;
-
```
0
0





