643
Asymmetric self-recovery oriented stereo image watermarking method for three dimensional…
1 3
of the left and right views are denoted as
and
,
respectively, where 1 ≤ i ≤ N
1
/4 and 1 ≤ j ≤ N
2
/4.
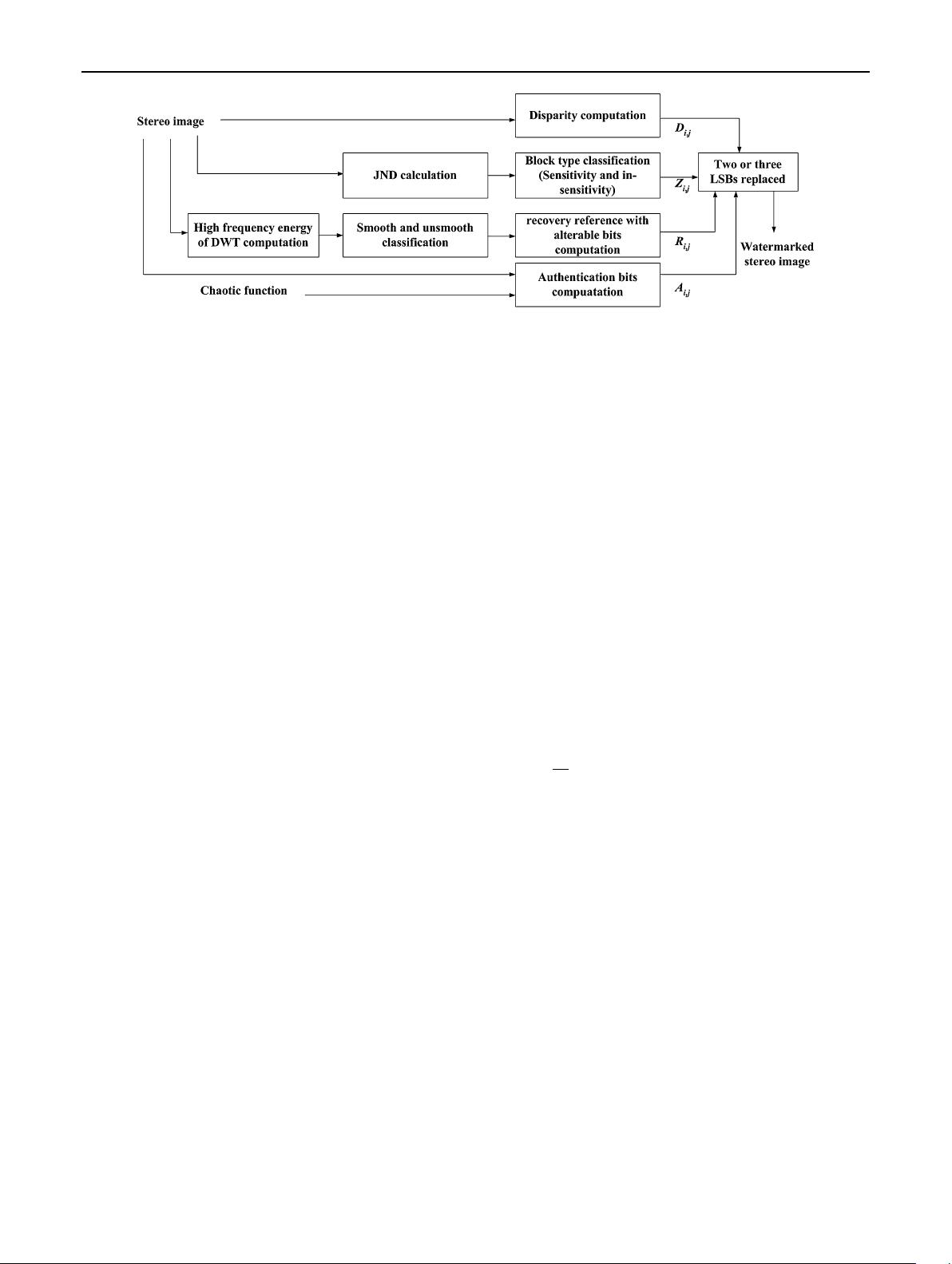
Step 2 The pixel-wise disparity map is divided into non-
overlapping blocks with the size of 4 × 4, and is trans-
formed to a block-wise disparity map. The block-wise
disparity D
i,j
is computed that if pixel-wise disparities in
the same block are all equal, D
i,j
is d(a, b), otherwise, it
is set to 255.
Step 3 JND value is computed for each block to deter-
mine the block type Z
i,j
, that is, sensitive or insensitive.
Compared with the sensitive block, large modifica-
tion of the insensitive block can not be discovered by
human vision. Thus, two and three LSBs of sensitive
and insensitive blocks are supplied for embedding
watermark, respectively. It is concretely described in
Sect. 2.1.1.
Step 4 Since DWT coefficients with high frequency ener-
gies represent detail information of blocks, they are used
to classify blocks into smooth and unsmooth. Recovery
reference R
i,j
are computed based on block’s smooth-
ness. It will be depicted specifically in Sect. 2.1.2.
Step 5 Authentication bits A
i,j
are computed and
described in Sect. 2.1.3.
Step 6 Watermarking capacity is allocated for asymmet-
ric embedding, and D
i,j
, Z
i,j
, R
i,j
and A
i,j
are embedded
into the left and right views of the original stereo image
to obtain its watermarked stereo image. In detail, they
are depicted in Sects. 2.1.4 and 2.1.5, respectively.
2.1.1 Block type classification
To obtain a trade-off between watermarking’s transparency
and capacity, blocks of the left and right views are clas-
sified into sensitive or insensitive ones according to JND
value which is related to background luminance masking
and texture masking. Background luminance masking is
taken into account that luminance contrast is more sensitive
than absolute luminance, and texture masking is built
on that textured regions can hide more information than
smooth or edge regions [21]. Let
denote the JND
value of the pixel p at the position (a, b) and then it is com-
puted by using Eq. (1) [21].
where U
l
and U
t
are visibility thresholds of background
luminance masking and texture masking, respectively, and
they are specifically defined in [21]. v
l
,
t
is the parameter
accounting for the overlapping effect in masking between
0 and 1. Since JND value of each pixel is computed for
detecting tamper, in the process of computing texture
masking, the threshold for image edge detection with Sobel
operator is a secret key
.
Let
denote the JND value of
each block, and it is computed as follows
Then, let Z
i,j
denote block type, and it is calculated by
where 1 and 0 indicates that the block is sensitive and
insensitive, respectively. When three LSBs of a pixel are
substituted, the largest difference between the original pixel
and the modified pixel is 7. Thus, T
s
is set to 7 for control-
ling LSB substitution without exceeding JND values. As
illustrated in Fig. 1, the pixels of the sensitive block only
offer two LSBs for embedding watermark, while the pixels
of the insensitive block offer three LSBs [23].
2.1.2 Recovery reference generation
Alterable bits are adopted to represent recovery reference
R
i,j
so as to recover the corresponding block when the
(1)
= U
l
+ U
t
− v
l,t
× min(U
l
, U
t
(2)
B
i,j
=
1
16
i×4
�
a=(i−1)×4+1
j×4
�
b=(j−1)×4+1
JND
p
a,b
(3)
i,j
=
1, JND
i,j
< T
0, otherwise
Fig. 1 Block diagram of watermark embedding









