1.1 The Quantified Self 3
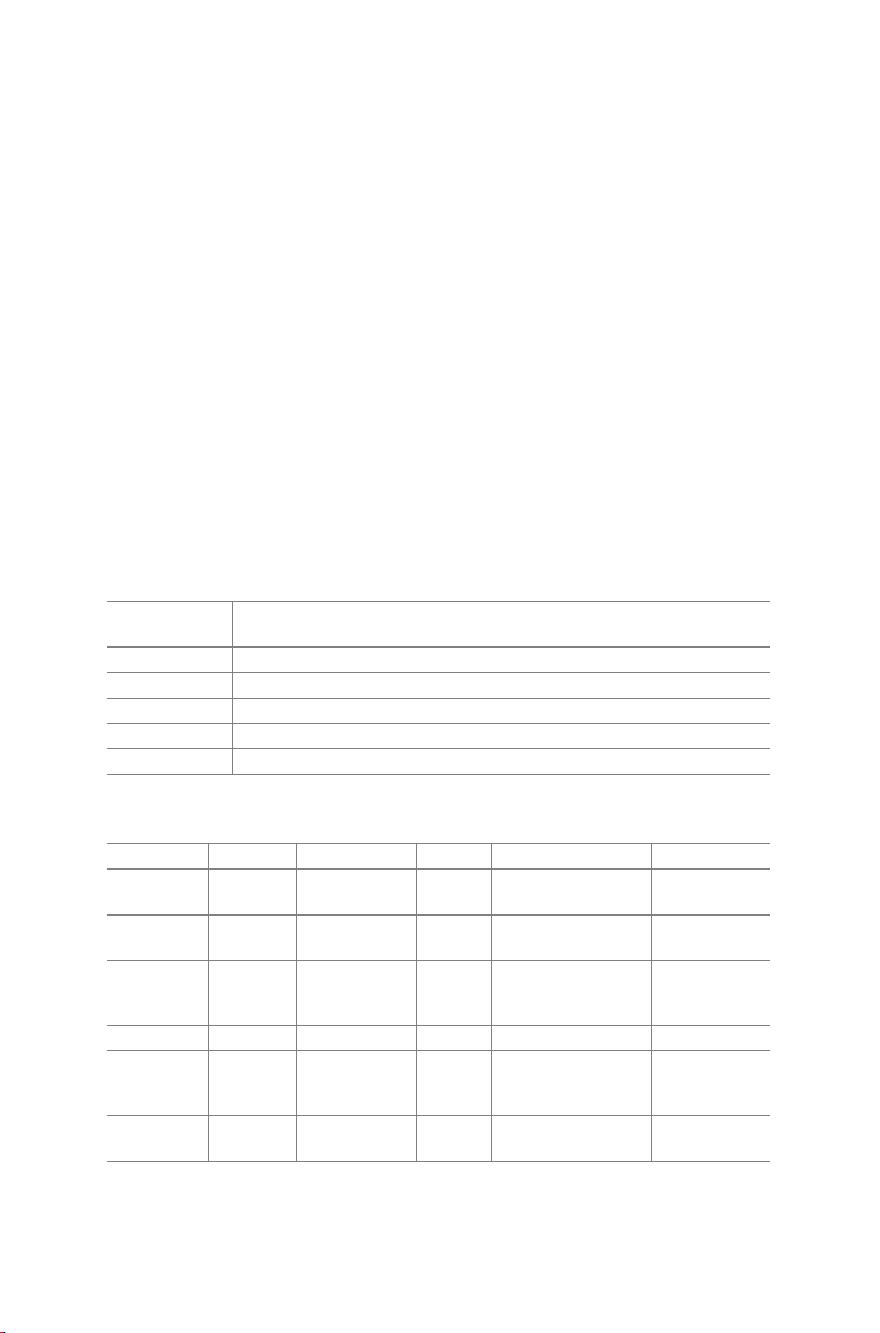
Table 1.1 Examples of quantified self data (cf. Augemberg [9], taken from Swan [114])
Type of measurement Examples
Physical activities miles, steps, calories, repetitions, sets, METs (metabolic
equivalents)
Diet calories consumed, carbs, fat, protein, specific
ingredients, glycemic index, satiety, portions,
supplement doses, tastiness, cost, location
Psychological states and traits mood, happiness, irritation, emotions, anxiety,
self-esteem, depression, confidence
Mental and cognitive states and traits IQ, alertness, focus, selective/sustained/divided
attention, reaction, memory, verbal fluency, patience,
creativity, reasoning, psychomotor vigilance
Environmental variables location, architecture, weather, noise, pollution, clutter,
light, season
Situational variables context, situation, gratification of situation, time of day,
day of week
Social variables influence, trust, charisma, karma, current role/status in
the group or social network
belongs to the group of quantified selves. Even if we restrict our definition to those
who use online or mobile applications or wearables for self tracking, the number of
users is high: An international consumer survey by GfK [50] in 16 countries states
that 33% of the participants (older than 15 years) monitor their health by electronic
means, China being in the lead with 45%. There are many indicators that the group
of quantified selves will continue to grow, one is, the number of wearables that is
expected to increase from 325 million in 2016 to more than 800 million in 2020 [110].
What drives these quantified selves to gather all this information? Choe et al. [38]
interviewed 52 enthusiastic quantified selves and identified three broad categories
of purposes, namely to improve health (e.g. cure or manage a condition, achieve
a goal, execute a treatment plan), to enhance other aspects of life (maximize work
performance, be mindful), and to find new life experiences (e.g. learn to increasingly
enjoy activities, learn new things). A similar type of survey is presented in [51] and
considers self-healing (help yourself to become healthy), self-discipline (like the
rewarding aspects of the quantified self), self-design (control and optimize yourself
using the data), self-association (enjoying being part of a community and to relate
yourself to the community), and self-entertainment (enjoying the entertainment value
of the self-tracking) as important motivational factors for quantified selves. They refer
to these factors as “Five-Factor-Framework of Self-Tracking Motivations”.
While Gimple et al. [51] study the goals behind the quantified self, Lupton [83]
focus on what she calls modes of self-tracking and distinguishes between private and
pushed self-tracking, the latter referring to situations in which the incentive to engage
in self-tracking does not come from the user himself but another party. This being
said, not only users themselves are interested in the data generated within the context
of the quantified self. Health and life insurances come to one’s mind immediately,